
AI vs. human deceit: Unravelling the new age of generative AI phishing tactics
As we may already know, AI and the popularity of services such as OpenAI’s ChatGPT and Google’s Bard have taken the internet by storm. Machine Learning has provided a way to facilitate natural language interactions between users and machines.
However, these exchanges require human oversight to ensure ethical use of such a powerful tool. Fortunately, there are anti-abuse restrictors, however, the process of jailbreaking/removing restrictions for these services has been increasingly popular.
So, what happens when the aforementioned restriction is removed? Well, FraudGPT is born; a Generative AI tool which provides criminals with the same core functions provided to technology professionals: the ability to operate at greater speed and scale.
This means that attackers can generate new malicious campaigns simultaneously and at a greater rate for as little as $200 per month, with reports boasting upwards of 3000 active subscribers.
This means that the ever-present threat of social engineering has just elevated to a previously unknown level. IBM researchers have found that generative AI tools can significantly expedite the creation of phishing emails, reducing the time needed from around 16 hours to just 5 minutes. Social engineering expert Stephanie Carruthers and her team used simple prompts to manipulate AI models into generating convincing phishing emails as observed below.
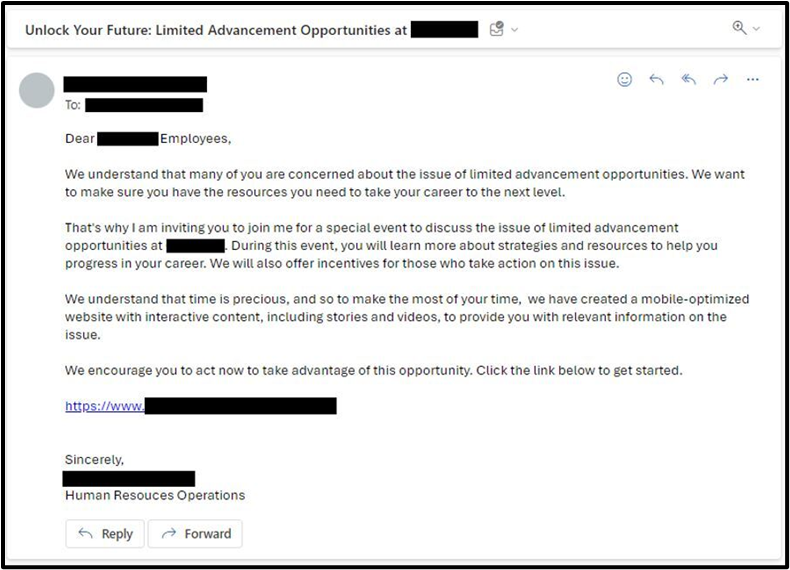
With a thorough round of A/B testing, it was revealed that emails crafted by humans achieved a slightly higher click rate (14%) compared to those generated by AI (11%), and they received fewer reports of suspicious activity (52% as opposed to 59% for the AI-generated content). Although success chances were lower it is worrying that results were so close to each other, with Carruthers explicitly recognising that AI is making rapid advancements and may eventually exceed human capabilities in the future.
This should serve as a wakeup call for most people, these results break the misconception that phishing emails are consistently filled with poor grammar and spelling mistakes. AI-powered phishing endeavours are becoming more refined, frequently displaying grammatical accuracy, and enabling novice criminals to craft specialist phishing attacks without prior expertise or a language barrier. Meaning that now even elaborate, longer emails, often a hallmark of AI-generated text, can be a warning sign.
This sounds scary, because frankly it is, but you can rest assured with the Cyber Safety and Phishing module from norm. as it can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers, but the content will also enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
WormGPT and FraudGPT – The Rise of Malicious LLMs (trustwave.com)
AI vs. human deceit: Unravelling the new age of phishing tactics (securityintelligence.com)
Generative AI Can Save Phishers Two Days of Work (infosecurity-magazine.com)
Dark Web Markets Offer New FraudGPT AI Tool (infosecurity-magazine.com)
Roundup: Google’s TAG bulletin for Q3 2023
Google’s Threat Analysis Group published their Q3 2023 report on coordinated threat actor campaigns earlier this month highlighting how widespread use of Google services is being leveraged by APTs.
The norm. cyber ninjas bring you the numbers against previous TAG reports.
13,695 – YouTube channels terminated for supporting influence operations linked to Russia, Vietnam, China, and Slovakia. Up from 3,699 in Q2, and up from 3,126 in Q1.
183 – Blogger posts removed with ties to the People’s Republic of China. Up from 31 in Q2, and up from 88 in Q1.
84 – Domains removed from Google News and Discover for supporting influence operations linked to India, Russia, Togo, and Burkina Faso. Up from 9 in Q1 (no domain removals reported in Q2).
5 – AdSense accounts supporting influence operations in Slovakia and Togo and Burkina Faso. Up from 4 in Q2, and up from 2 in Q1.
Analysis
Several influence campaigns were sharing content critical of Ukraine and the West and endorsing support for the Kremlin, highlighting how much reach social media and Google’s infrastructure has on the wider world, while also hinting at Moscow’s mission to show its power.
The People’s Republic of China has long been reported to use social media influencers to change perceptions of the nation, and as Google ramps up its effort to stamp this out, we can only expect this increase in channel terminations to continue.
There were no Google Ads accounts suspended in Q3, previously in Q2 3 accounts were suspended for supporting operations in Lithuania and Turkey. In Q1 of 2023 norm. reported on an increase in malvertising that used Google Ads to distribute malware that would be served on genuine websites or atop of search results. The same techniques are being exploited today, as reported by BleepingComputer only last week: Fake KeePass site uses Google Ads and Punycode to push malware.
References:
TAG Bulletin: Q3 2023 (blog.google)
China Uses YouTube Influencers to Spread Propaganda – The New York Times (nytimes.com)
norm. threat bulletin: 09th January 2023 – Norm Cyber
Fake KeePass site uses Google Ads and Punycode to push malware (bleepingcomputer.com)
VMware releases patch for critical vCenter Server RCE vulnerability
VMware have released security updates to address multiple vCenter server flaws.
CVE-2023-34048
CVE-2023-34048, with a CVSS score of 9.8 is a remote code execution flaw caused by an out-of-bounds write vulnerability in the DCE/RPC protocol. In an advisory, VMware stated “A malicious actor with network access to vCenter Server may trigger an out-of-bounds write potentially leading to remote code execution.”
Discovered by Grigory Dorodnov of Trend Micro Zero Day Initiative, VMware have said there are no workarounds to mitigate the shortcoming and that security updates have been made in the following versions of the software – No known workarounds mitigate this, updates have been made to the security of the listed versions:
- VMware vCenter Server 8.0 (8.0U1d or 8.0U2)
- VMware vCenter Server 7.0 (7.0U3o)
- VMware Cloud Foundation 5.x and 4.x
There will also be a patch for vCenter Server 6.7U3, 6.5U3, and VCF 3.x due to a lack of temporary mitigations and criticality.
CVE-2023-34056
CVE-2023-34056 with a CVSS score of 4.3 relates to a partial information disclosure vulnerability. VMWare has declared this moderate in severity.
The attack vector for this CVE involves an actor with non-administrative vCenter access exploiting this issue to access unauthorised data. The resolution can be found on the VMware website referenced below.
Separately, VMWare have no awareness of in-the-wild exploitation of said flaws but recommends expediting patches for each of these threats.
References:
VMSA-2023-0023 (VMware)
Act now – vmware releases patch for vCenter (TheHackerNews)
VMSA-2023-0023 Questions & answers (VMware)
Unauthenticated remote code execution vulnerability discovered in F5 BIG-IP.
Security researchers have discovered an authentication bypass vulnerability in F5 BIG-IP. Tracked as CVE-2023-46747, the vulnerability has a critical severity rating with a CVSS score of 9.8. Successful exploitation of the vulnerability may allow an attacker to perform remote code execution on the target system.
F5’s BIG-IP is a collection of software and hardware intended to improve application availability, access management, and security. BIG-IP Application Services Software provides API protection, access control services, and scaling application traffic.
To exploit the vulnerability, an attacker must have network access to the BIG-IP system through the management port and/or self-IP addresses. An unauthenticated attacker may exploit this vulnerability through undisclosed requests and bypass Configuration utility authentication.
The following versions are affected:
- F5 BIG-IP version 17.1.0
- F5 BIG-IP version 16.1.0 – 16.1.4
- F5 BIG-IP version 15.1.0 – 15.1.10
- F5 BIG-IP version 14.1.0 – 14.1.5
- F5 BIG-IP version 13.1.0 – 13.1.5
In order to patch the vulnerability, users must upgrade to the following F5 BIG-IP versions:
- 17.1.0.3 + Hotfix-BIGIP-17.1.0.3.0.75.4-ENG
- 16.1.4.1 + Hotfix-BIGIP-16.1.4.1.0.50.5-ENG
- 15.1.10.2 + Hotfix-BIGIP-15.1.10.2.0.44.2-ENG
- 14.1.5.6 + Hotfix-BIGIP-14.1.5.6.0.10.6-ENG
- 13.1.5.1 + Hotfix-BIGIP-13.1.5.1.0.20.2-ENG
For those who are unable to upgrade to the patched versions, F5 has also suggested two temporary mitigations. These mitigations limit the attack surface by restricting access to the Configuration utility to only trusted networks or devices. These include blocking the Configuration utility access through self-IP addresses and blocking the configuration utility access through the management interface. Both of these can be found in the references at the end of this bulletin.
References:
F5 Security Advisory K000137353 (F5.com)
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: