
CloudWizard – The new magic box of malware tricks
For at least the last decade Ukraine has been what many cybersecurity researchers consider to be the hotbed for APT operations – BlackEnergy, GreyEnergy and Industroyer to name a few. In March 2023, Kaspersky published research on an unseen and unattributed malware framework dubbed ‘CommonMagic’ that targeted victims of agriculture and transportation services in Donetsk, Lugansk, and Crimea [1]. CommonMagic has capabilities to steal sensitive documents and to record screenshots of infected devices, exfiltrating this data via C2 to OneDrive and DropBox cloud storage.
The CommonMagic malware framework does not rely on sophisticated delivery or infection methods. The initial infection vector is distributed via ZIP files in phishing emails containing malicious .PDF or .LNK files, which point towards a remote .MSI file that drops components of PowerMagic – the backdoor that retrieves the CommonMagic framework.
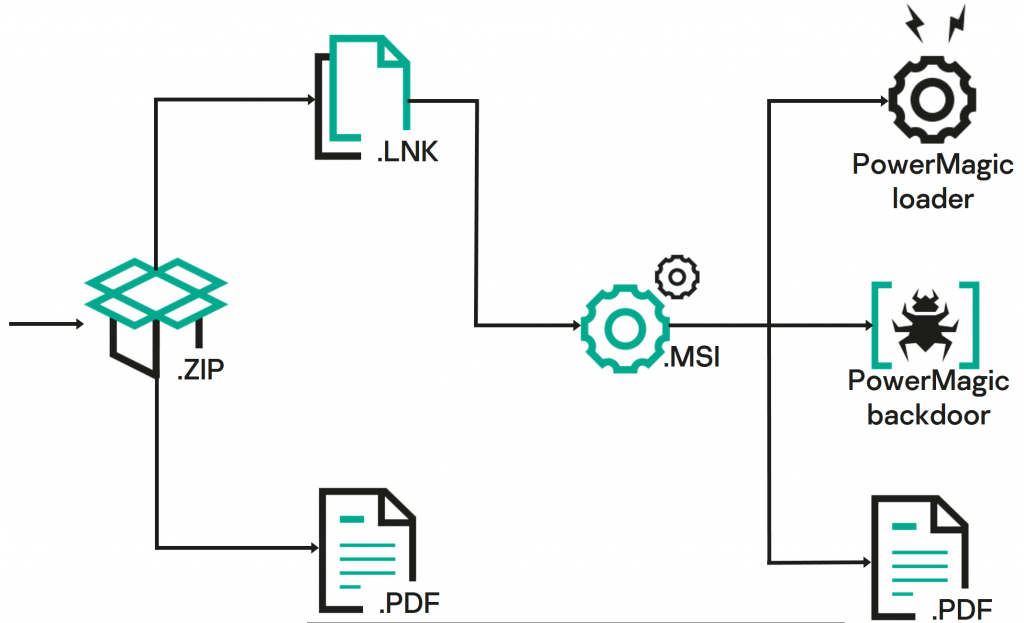
Kaspersky’s continued investigation for similar malware samples identified a much more sophisticated framework now known as ‘CloudWizard,’ with new victims in diplomatic and research organisations spilling into central and western Ukraine [2]. The CloudWizard framework builds on CommonMagic with several feature-specific modules (DLLs) for keylogging, microphone recording, USB data stealing, screenshotting, credential stealing, and Gmail email exfiltration. The Gmail module extracts cookies from the victim’s browser and accesses Gmail’s legacy web app to exfiltrate the victims contacts and their emails. CloudWizard can update, change, or install brand new modules via a web based C2 should the operator continue their development.
Kaspersky noted that characteristics of CloudWizard matched that of previous APT campaigns in Ukraine – Operation Groundbait and Operation BugDrop. These operations have gone quiet since 2017 but evidence suggests these campaigns are still active and development of their espionage kits is ongoing.
By utilising norm.’s Threat Detection & Response module, your network and endpoints are monitored around the clock for malware setup and detonation, while our phishing simulation services raise and train employee awareness of malware delivery via email.
Sources:
[1] Hackers use new PowerMagic and CommonMagic malware to steal data (bleepingcomputer.com)
[2] CloudWizard APT: the bad magic story goes on
Dropbox to your inbox; How attackers are leveraging Dropbox to perform phishing attacks
It is widely known these days that email-based cyber-attacks are a threat actor’s go-to when they want to perform a cyber-attack. According to Check Point Research, 89% of all in-the-wild attacks are delivered via email, which has increased from 33% in 2018 (a 56% increase in 4 years). Due to this increase, security providers have developed/improved ways in which they defend against these attacks; however, attackers have also adjusted and have figured out ways to circumvent modern defences.
A popular vector for email attacks is to impersonate a brand that a user is interested in or a service that they use, as this is more likely to cause an interaction. However, recently threat actors have decided that they no longer want to play the imitation game and would rather go for the real thing. This may sound like a challenging task, however it is the opposite, as an attacker can simply sign-up for a free account at a popular and legitimate website and send out phishing emails directly from the service. Using legitimate services as a tool to unleash cyber attacks is also known as Business Email Compromise (BEC), with the latest innovations called BEC 3.0.
This article will run through an attack brief developed by researchers at Avanan, which outlines how attackers can create malicious files with Dropbox and send a legitimate link from Dropbox, sharing a malicious file containing a fake OneDrive link.
Step One
The attack starts by simply sharing a file via Dropbox, and to see it, the end user must add said file to their Dropbox. At this stage, there is nothing malicious. However, attackers are employing it in a different manner. Once a user clicks the link and enters Dropbox, they will see a page that is hosted by Dropbox. This page will prompt the user to enter their email address and password to view the shared document. Entering these credentials will in turn, provide them to the attacker, meaning that before even viewing the document, an attacker has access to your credentials.
Step Two
Once the user has “logged in”, they will be redirected to a website, which leads to a malicious URL. Using such a simple attack methodology, attackers can create two potential security breaches: stealing your credentials and causing you to click a malicious URL. The ingenious thing about this form of attack is that the URL is legitimate, it’s the content of the website that’s the issue.
Threat actors are a devious but clever bunch. They’ll find an attack that works and develop it until it no longer provides them success. In the case of these forms of attacks, we could be seeing them for a long time due to their leverage of legitimate sites to deliver malicious payloads to users. The main reason for its potential longevity is how it can deceive security services, as it will present itself as legitimate and this will allow it to slip through detection software. And it’s able to do so because it is from a legitimate source. Until there is a way to detect these attacks, we can be sure to expect threat actors to utilise this attack format going forward.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
Sources:
Leveraging Dropbox to Soar Into Inbox (avanan.com)
Microsoft Azure Serial Console and SIM swap attack
If the title does not grab your attention let us explain why you need to know about this in more detail and what you can do to fight against it.
This attack has been contributed back to the UNC3944 group and was identified by Mandiant back in 2022. They state that their investigation revealed malicious use of the Serial Console on Azure virtual machine (VM) and third party remote management within the client environment. This is not a traditional route that attackers use to gain access to admin accounts, and this means that it could slip through the cracks with attackers avoiding detection and providing full admin access to the VM. This highlights the importance of checking for misconfigurations within your environment helping you to fight against this attack and removing vulnerabilities. As businesses migrate to the cloud, attackers are pivoting on how they compromise environments.
The uncategorised group UNC3944 are a financially motivated threat actor that Mandiant have been tracking since May 2022. One of their tactics is SIM swapping, which they are using to establish persistence using compromised accounts. Once they have established persistence, they have been observed modifying and stealing data from the organisation’s environment. This heavily relies on email and SMS phishing, highlighting the importance of keeping staff training up to date. By utilising the Cyber Safety & Phishing module from norm. you can better equip your staff to spot potential phishing emails and know what they need to do to follow company procedure when reporting phishing emails. What makes this more dangerous is that they are also running phishing campaigns after they have gained access to the employee database, this gives them the ability to do more targeted attacks on your employees.
They often leverage compromised credentials of administrators or other privileged accounts for initial access. The attacker often uses the tactic of SMS phishing of privileged users, SIM swapping, and then impersonating the user to trick help desk agents into sending a multi-factor reset code via SMS. Further highlighting the danger of using SMS as your method of multi factor authentication (MFA). norm. recommends using an authenticator app, not only would the bad actor need to have direct control of the smart phone, but you can often setup other controls like face ID or fingerprint access to these apps and the device itself. Employees should be encouraged to never share a code generated under any circumstances.
The attacker’s goal is to gain access to the Azure administrator account, because then they have full access to the Azure tenant due to the global privileges granted to the administrator’s account. With full access to the tenant, they can perform many actions. Such as, exporting information about users in the tenant, gather information about the Azure environment configuration and the VMs, and create or modify accounts. It is important to employ the least privilege model and ensure that you utilise role-based access, group access, using least privilege, and separation of admin accounts away from your everyday user accounts. This separation ensures that not one account has access to everything, limiting the impact of a compromised account. norm. recommends that an audit of your environment be undertaken. Often people move from one role to another and are granted privileges of the new role but don’t have the old role’s privileges revoked. Start utilising things like just-in-time (JIT) access and using conditional access for the accounts that you can’t afford to lose access to.
UNC3944 utilises the “CollectGuestLogs” via the Azure diagnostic extensions, enabling them to be able to gather log files for offline analysis. Once the attacker completes their reconnaissance, they will use the serial console functionality in order to gain an administrative command prompt inside of the Azure VM. The special Administrative Console (SAC) allows you to connect to your running OS via serial port. After the attacker successfully logs in to the target VM, the attacker will deploy multiple commercially available remote administration tools via PowerShell, this gives them the advantage as they are legitimately signed applications and provide the attacker remote access without triggering alerts in many endpoint detection platforms. They then setup a reverse SSH tunnel to the attacker’s command control (C2) server. They have been observed using port 12345 remote machine port forwarding to localhost 3389 (RDP) allowing the attacker direct connection to the Azure VM via remote desktop.
The attackers are using the VMAccessAgent extension to enable Remote Desktop and facilitate a password reset of an admin account. The attacker then leverages a known compromised user account to perform a logon, resulting in a successful type 2 (interactive) logon to the same compromised Windows VM. This is important because the user then transitions from the serial console to a local command prompt on the target VM. This is logged as a type 2 (interactive) event rather than a type 10 (remote interactive) event often associated with RDP.
This is a great example of “living off the land,” showing that bad actors are constantly evolving and utilising the land to stay under the radar for as long as possible. The use of the serial console is a perfect example that attacks are evolving all the time and many are no longer using traditional ways.
By leveraging the Cyber Safety and Phishing module of the smartbloc. service from norm. you can ensure that you’re better protected against these threats.
Sources:
SIM Swapping and Abuse of the Microsoft Azure Serial Console
Sotdas Malware analysis
Researchers at Qualys have discovered a new variant from the malware known as Sotdas, which demonstrates a high level of persistence and resource optimisation in its cryptomining operations. This new threat has several upgraded features and advanced defence evasion techniques, with the primary purpose to gather information from the compromised systems and execute malicious activities.
To establish a lasting presence on the infected system, Sotdas employs persistence mechanisms that enable it to remain undetected over an extended period. Once successfully embedded, the malware proceeds to collect relevant system information, such as CPU and memory details. By acquiring this data, Sotdas gains insights into the system’s hardware capabilities, which it utilises for its subsequent operations.
Leveraging the gathered CPU and memory details, Sotdas aims to achieve maximum performance in its cryptomining endeavors. The malware strategically utilises all available CPU resources, effectively harnessing the processing power of the infected system. By doing so, it maximizes its mining capabilities while minimizing the chances of arousing suspicion or triggering detection mechanisms.
Aware of the need to remain covert, Sotdas implements several evasion techniques such as setting up a daemon process, it will create a script using /proc file system and exploiting system V runlevel configuration to avoid detection. The malware continuously monitors the system’s CPU utilisation to ensure it maintains a low profile, carefully adjusting its resource usage, as necessary. By dynamically adapting its mining activities, Sotdas avoids sudden spikes in CPU usage that could raise red flags and attract attention.
The malware periodically verifies the system’s memory usage to guarantee sufficient available memory for uninterrupted mining operations. This proactive measure prevents excessive memory consumption, which could lead to system instability or unexpected crashes, ultimately drawing attention to the illicit activities.
Moreover, Sotdas employs DNS tunnelling as a means of communication with its command and control (C&C) server. This technique involves the use of custom DNS query messages and payload encoding within DNS records.
With its advanced detection capabilities, the Qualys Multivector EDR platform is proficient in effectively scanning and identifying the Sotdas malware.
Indicators of compromise
Hashes
MD5: 31d5a627bcc63682c43e6e8c785c4d57
SHA-1: 019baa5eeec142d143fce17694c47bc40ce3122d
SHA-256: f7a8eb6dda1d15bead43d94df0bcfdd2a7dccab0eb06c89e5e85034561f60563
File name: .iamgood
Domain
sockt.best
Directories
/etc/rc2.d/
/etc/rc3.d/
/etc/rc4.d/
/etc/rc5.d/
/etc/init.d
/tmp/
MITRE ATT&CK Techniques
T1037.004 – Boot or Logon Initialization Scripts: RC Scripts
T1543.002 – Create or Modify System Process: Systemd Service
T1036 – Masquerading: Match Legitimate Name or Location
T1070.004 – Indicator Removal: File Deletion
T1222 – File and Directory Permissions Modification
T1564.001 – Hide Artifacts: Hidden Files and Directories
T1082 – System Information Discovery
T1057 – Process Discovery
T1071.004 – Application Layer Protocol: DNS
Sources:
New Strain of Sotdas Malware Discovered | Qualys Security Blog
Qualys Discovers New Sotdas Malware Variant – T O L T E C S Information Technology
Qualys Discovers New Sotdas Malware Variant | Cyware Alerts – Hacker News
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: