
Critical Apache text commons vulnerability
On 13th October, Apache disclosed a critical vulnerability in one of their code libraries, alongside a patch to remediate. This vulnerability has garnered significant media attention due to the similarities to Log4Shell and has been coined Text4Shell. Like Log4Shell, which rose to infamy at the tail end of 2021, this vulnerability allows a potential attacker to execute their own malicious code on a susceptible web-facing server. The potential impacts of such an exploit could be far reaching and severe.
However, unlike Log4Shell, the vulnerable code library is far less commonly used and the exploitable implementation is not present by default. This results in a dramatically reduced exposure compared to Log4Shell, which is supported by the lack of successful exploits declared to date.
Technical Breakdown
For this vulnerability to be exploitable, the attacker would need to be able to make web requests (HTTP or HTTPS) to a web application running Apache Text Commons 1.9 or earlier. The implementation of this library would also need to utilise the StringSubstitutor class along with a method to pass the request data to it.
The vulnerability has had several reported exploit attempts, but none have yet been declared as successful.
To identify the vulnerability, you will need authenticated access to the Apache server. The following Linux commands can then be run to identify any affected versions of the library:
`ls -l /proc/*/fd | grep -Eo ‘\S+\/commons-text\S+jar’ | uniq 2`
`locate -b -e -r ‘^commons-text.*\.jar$`
norm. are actively monitoring the threat to keep abreast of any exploits that arise, any customers that have taken vulnerability management with agents deployed across their environment would be alerted to vulnerable systems.
Despite the reduced exposure, we would still consider this a serious vulnerability as the risk to reputation is considerably elevated with the extent of media coverage and availability of a patch. With that in mind, we recommend that you review all Apache web servers for the vulnerable library and strongly consider patching as a priority.
For businesses with web applications hosted by 3rd parties, we would recommend contacting them to confirm that they have taken appropriate remediation.
CVE Reference: CVE-2022-42889
Vendor Advisory: Apache Commons Text
Original Discovery: Security Lab
Log4Shell Reference: CVE-2021-44228
Affected Versions: Apache Commons Text prior to 1.10.0
Mitigation: Upgrade to Apache Commons Text 1.10.0
Mark-of-the-Web, what is it?
Mark-of-the-Web (MoTW) is a security mechanism in Windows. Files that are downloaded from the internet are automatically tagged by Windows with a hidden field, the operating system uses this field to restrict certain actions the file can perform to maintain security.
For example, Microsoft Office files that are downloaded from the internet will open in “protected view“, this restricts automatic macro execution along with other security protections. Executables are run through Windows Defender SmartScreen which will compare the file with Microsoft’s allow list along with warning the user before execution.
Mark of the Web exploitation
Attackers have been developing methods to bypass this functionality to improve their exploitation success rates. Recently we have seen reports that the ‘Magniber’ ransomware variant utilises a zero-day exploit to bypass MoTW checks on their payloads. This is achieved by providing an invalid digital signature to the payload, Windows identifies a signature (regardless of legitimacy) and skips the MoTW checks.
From testing performed by researchers it was found that Windows 10 was the most exploitable, any file with a signature did not apply MoTW checks. Windows 11 however only skipped MoTW checks when the file was contained within an archive (.zip/.iso/.cab).
Protection
Whilst Microsoft have not provided an official solution / patch to prevent MoTW bypassing, third party security tooling such as norm.’s EDR service will still detect and prevent malicious files on write, regardless of their source.
If using a Windows 11 device, it is recommended any archive files received via the internet are extracted fully (using supported archive software) before being interacted with, this will ensure MoTW is correctly applied.
Microsoft Defender SmartScreen
Emotet botnet distributing self-unlocking password-protected RAR files to drop malware
The notorious Emotet botnet has been linked to a new wave of ‘malspam’ campaigns that take advantage of password-protected archive files to drop CoinMiner and Quasar RAT on compromised systems.
Malspam, short for malware spam or malicious spam, is spam email that delivers malware. Coinminers (also called cryptocurrency miners) are programs that generate Bitcoin, Monero, Ethereum, or other cryptocurrencies. Quasar remote administration tool (RAT) is a multi-functional and light-weight malware actively used by APT actors since 2014.
This latest discovery is significant because one of the most difficult obstacles threat actors face when conducting this type of spam campaign is to convince the target to open the archive using the provided password.
Researchers have found this campaign sidesteps the aforementioned challenge by attaching a zip file which contains a nested self-extracting archive, with the first archive acting as a means to launch the second. The self-extracting archive has been around for a long time and eases file distribution among end users. However, it poses a security risk since the file contents are not easily verifiable, and it can run commands and executables silently. Additionally, by password protecting an archive, this file can at times be skipped by some antivirus solutions.
While phishing attacks like these traditionally require persuasion of the target into opening the attachment via social engineering, this method prevents this need by making use of a batch file to automatically supply the password to unlock the payload. This leads to the installation of the malware within the password protected self-extracting RAR archive. In addition to providing the password, the batch script also specifies the destination folder where the payload will be extracted and a command prompt is invoked, with its aim to display a decoy in the shape of an image or PDF attempting to hide the extraction process from the view of the user. Finally, the infection concludes in the execution of CoinMiner or Quasar RAT, depending on the payload packed in the archive.
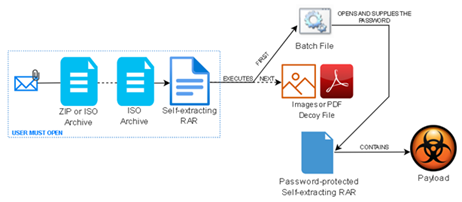
norm.’s EDR service actively scans on demand files when they are created and/or modified, this in addition to scheduled scans provides coverage of the above zip files being created and/or downloaded. Users can remain cautious and on the look out for any unsolicited emails, especially if they have attachments. norm.’s EDR toolkit and phishing awareness training together continue to keep customers protected.
Sources:
Emotet Botnet Distributing Self-Unlocking Password-Protected RAR Files to Drop Malware
Archive Sidestepping: Self-Unlocking Password-Protected RAR
CISA releases security configuration baselines for Microsoft 365
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) have released a set of security configuration baselines for Microsoft 365, they provide a set of easily adoptable recommendations to help strengthen the Microsoft 365 environment. They have also released a tool called ScubaGear, which when ran against your Microsoft 365 environment will quickly and easily asses your environment against the baselines developed.
The areas covered by the security baselines are:
- Microsoft Teams
- SharePoint Online
- OneDrive for Business
- Exchange Online
- Power Platform
- Defender for Office 365
- Power BI
- Azure Active Directory
The baselines have been written primarily for US federal agencies, such as Department of Homeland Security and Federal Trade Commission, however by running and reviewing the baselines against your own Microsoft 365 environment it will quickly and easily identify any gaps in security posture as well as advise on how to mitigate and reduce risk levels.
Sources:
Critical remote authentication bypass vulnerability in Fortinet firewalls, web proxies
There is a critical vulnerability that affects FortiOS, FortiProxy and FortiSwitchManager products. The vulnerability allows remote, unauthenticated attackers to bypass authentication and gain access to the administrative interface of each of these products with only a specially crafted HTTP/HTTPS request.
There are now multiple exploits in the wild for this, including a widely accessible module for Metasploit, a popular tool to automate attacks.
Affected products
- FortiOS 7.0.0 to 7.0.6
- FortiOS 7.2.0 to 7.2.1
- FortiProxy 7.0.0 to 7.0.6
- FortiProxy 7.2.0
- FortiSwitchManager 7.0.0
- FortiSwitchManager 7.2.0
It is imperative that you upgrade any vulnerable versions of these devices to the latest version.
Sources:
FortiOS / FortiProxy / FortiSwitchManager – Authentication bypass on administrative interface
Fortinet FortiOS / FortiProxy / FortiSwitchManager Authentication Bypass
Get norm.’s threat bulletin direct to your inbox
Norm. tracks and monitors the latest security trends and latest cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: