
Persistent Chinese Hackers who exploited VMware Zero-Day Vulnerability for two years
The China-nexus cyber espionage group associated with China, previously known for exploiting vulnerabilities in VMware and Fortinet appliances, has now been identified for exploiting a critical flaw in VMware vCenter Server as a zero-day since late 2021. Mandiant, a cyber security company owned by Google, revealed in a recent report that UNC3886, has a history of using zero-day vulnerabilities to carry out its operations discreetly. The group’s latest activity underscores its advanced capabilities.
The specific vulnerability in focus is CVE-2023-34048 (CVSS score: 9.8), characterised by an out-of-bounds write. This flaw could be exploited by a malicious actor with network access to vCenter Server to achieve remote code execution. Broadcom, the owner of VMware, addressed this vulnerability on October 24th 2023, after it was discovered. UNC3886 was first identified in September 2022, initially exploiting undisclosed security flaws in VMware to compromise Windows and Linux systems, deploying malware families such as VIRTUALPITA and VIRTUALPIE.
Further investigations by Mandiant revealed that the recent zero-day utilised by UNC3886 to target VMware was CVE-2023-34048. This vulnerability allowed the group to gain privileged access to the vCenter system, enabling the enumeration of all ESXi hosts and their respective guest virtual machines connected to the system.
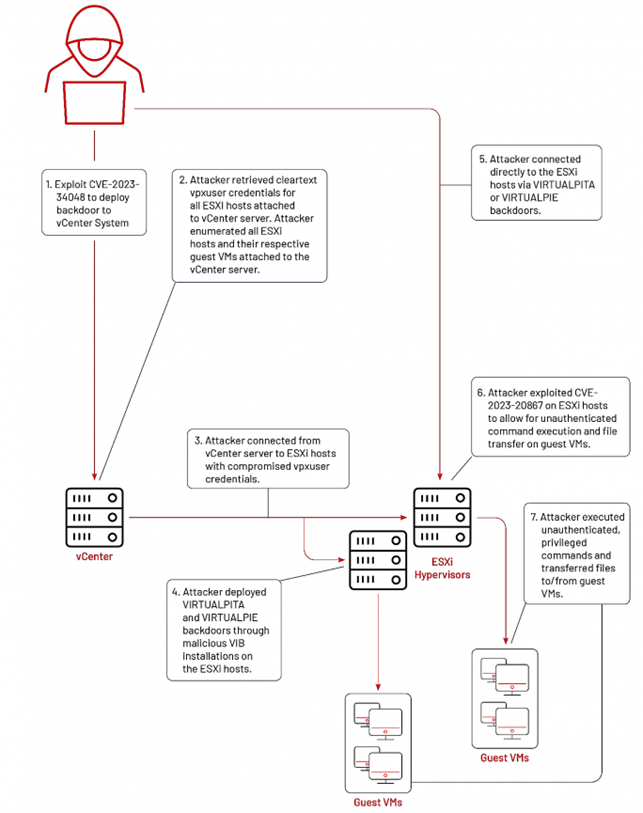
Subsequent stages of the attack involved retrieving clear text “vpxuser” credentials for the hosts, connecting to them, and installing the VIRTUALPITA and VIRTUALPIE malware. This provided the adversary with direct access to the hosts. The exploitation of another VMware flaw (CVE-2023-20867, CVSS score: 3.9) was also disclosed by Mandiant in June 2023, allowing arbitrary commands execution and file transfer to and from compromised guest VMs on ESXi hosts. In March, Mandiant revealed the threat actor also abused a Fortinet zero-day (CVE-2022-41328) in the same operation to compromise FortiGate firewall devices and install formerly unknown Castletap and Thincrust backdoors.
To mitigate potential threats, users of VMware vCenter Server are advised to update to the latest version. UNC3886 has also been noted for exploiting CVE-2022-41328 (CVSS score: 6.5), a path traversal flaw in Fortinet FortiOS software. This enabled the deployment of THINCRUST and CASTLETAP implants, facilitating the execution of arbitrary commands and exfiltration of sensitive data from target environments.
The cyber attacks orchestrated by UNC3886 specifically target firewall and virtualisation technologies due to their lack of support for endpoint detection and response (EDR) solutions, allowing the group to persist within targeted environments over extended periods.
References:
Chinese Hackers Silently Weaponized VMware Zero-Day Flaw for 2 Years (thehackernews.com)
Chinese Hackers Covertly Exploited VMware Zero-Day Vulnerability for a Period of Two Years. | by DEF-X | Jan, 2024 | Medium
Chinese hackers exploit VMware bug as zero-day for two years (bleepingcomputer.com)
Cyber threat collaborators unite for a surge in Phishing emails post-holidays
In a cyber showdown that defies expectations, two formidable threat actors have teamed up, unleashing a dynamic alliance to spearhead a potent and unprecedented wave of cyber threats.
Just last week threat actors, TA866 and TA571, orchestrated a widespread phishing campaign targeting North American organisations post the holiday break. The emails featured generic subject lines and corporate hooks, leading users to click on OneDrive links within attached PDFs, resulting in the delivery of custom malware known as “WasabiSeed” and “Screenshotter.”
TA866, initially associated with the Screentime campaign, is suspected to have financial motivations. Screenshotter functions as a reconnaissance tool to pinpoint high-value targets, leading to the deployment of the Rhadamanthys information stealer. Overlaps between Screentime and Asylum Ambuscade, a crimeware group engaged in cyber espionage since 2020, were discovered by ESET.
The latest attack chain involves a shift from macro-enabled Publisher attachments to PDFs with rogue OneDrive links. TA571, a spam distributor, then aids in disseminating these booby-trapped PDFs. TA571 offers a spam service delivering various malware, including DarkGate, enabling attackers to execute commands such as information theft and cryptocurrency mining to affected machines.
The timing of the attack, occurring after the holiday break, aligns with a trend where major e-crime actors take hiatuses during holidays. This observed reduction in activity is notable among high-volume, well-resourced cyber crime groups. TA571’s break between mid-December and the second week of January is a specific example. As these serious threat actors return online, experts anticipate an increase in overall threat landscape activity.
Luckily, you don’t need to deal with these issues on your own, help save yourself from future troubles by partaking in the Cyber Safety and Phishing module from norm. It can educate users on how to spot a likely malicious email. With this education, not only would you be more aware of the tactics used by attackers but the content will also enable you to exercise caution when clicking on suspicious emails and links. We highly recommend that you take a minute to assess an email or message before responding and never give any remote access to your device.
References:
Invoice Phishing Alert: TA866 Deploys WasabiSeed & Screenshotter Malware (thehackernews.com)
Security Brief: TA866 Returns with a Large Email Campaign (proofpoint.com)
Screentime: Sometimes It Feels Like Somebody’s Watching Me (proofpoint.com)
Threat Actors Team Up for Post-Holiday Phishing Email Surge (darkreading.com)
Apple Releases patch for Zero-day vulnerabilities used in attack against iOS and macOS
Apple has released a new software version which patches vulnerabilities being exploited by threat actors across a range of Apple products. The threat actors have been seen to be targeting iPhones, iPads, and Macs. However, Apple has provided extended range of coverage and addressed the vulnerabilities in products such as Safari, iOS, iPadOS, macOS, watchOS, and tvOS. Along with this zero-day vulnerability, Apple has addressed multiple vulnerabilities affecting its popular products.
There are three vulnerabilities which Apple state they have observed being exploited in the wild, a simple breakdown of these is:
CVE-2023-42916: This is a an out-of-bounds read flaw that exists in the WebKit browser engine. This vulnerability can be exploited by simply processing web content. Successful exploitation of the vulnerability can disclose sensitive information. Apple has fixed the vulnerability with improved input validation.
CVE-2024-23222: This is a type of confusion flaw that exists in the WebKit browser engine. An attacker could exploit the vulnerability by processing maliciously crafted web content. Successful exploitation of the vulnerability leads to arbitrary code execution. Apple has fixed the vulnerability with improved checks.
CVE-2023-42917: This is a memory corruption flaw which exists in the WebKit browser engine. An attacker could exploit the vulnerability by processing maliciously crafted web content. Successful exploitation of the vulnerability may lead to arbitrary code execution. Apple has fixed the vulnerability with improved locking.
CVE-2023-42916 and CVE-2024-42917 have both been seen targeting iOS devices with software versions before iOS 16.7.1 installed. Whereas CVE-2023-4916 has been seen by Apple to be targeting no specific software version device, any iOS device before this 17.3 release and any MacOS device before this Sonoma 14.3 release.
The entire update covers over 24 other identified vulnerabilities, however only the 3 above have been confirmed to being observed as actively exploiting devices in the wild.
In order to mitigate the threats posed by the above vulnerabilities, Apple is recommending users to update their devices to the latest versions as soon as possible. This includes:
- iOS 17.3
- macOS Sonoma 14.3
- tvOS 17.3
- Safari 17.3
However, user’s whose devices cannot support the latest major iOS update (17), can update their older devices to the following versions for a security only update:
- iOS 16.7.5
- iOS 15.8.1
- macOS Monterey 12.7.3
- macOS Ventura 13.6.4
References:
About the security content of tvOS 17.3 – Apple Support
About the security content of Safari 17.3 – Apple Support
About the security content of iOS 17.3 and iPadOS 17.3 – Apple Support
About the security content of macOS Sonoma 14.3 – Apple Support
About the security content of iOS 16.7.5 and iPadOS 16.7.5 – Apple Support
About the security content of macOS Monterey 12.7.3 – Apple Support
About the security content of macOS Ventura 13.6.4 – Apple Support
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: