
How much information do you share online?
Social media platforms, including LinkedIn and Facebook, encourage users to fill out their profiles with lots of personally identifiable information. Profile completion progress bars are a key example where platforms make it an objective to disclose as much information as possible. It is important to understand the level of information you are comfortable with sharing online as these details can be used by bad actors that scour social media platforms and company websites for information to identify targets of phishing or brute force attacks.
Cyber criminals also search for user credentials to abuse listed in public data breaches. Some of the most significant personal data breaches surfaced in a 2021 data leak of 500 million Facebook users and the 2018 breach of Netlog, which involved over 49 million leaked user details.
norm. has observed brute force activity performed against numerous users that have business account details listed in public data breaches. Notably, we see business accounts that have been involved in public data breaches and entire domains targeted as a result.
It is important to understand the risks associated with using business email addresses for personal use as it could end up putting your business in the firing line if a personal data leak occurs further down the line.
How to safeguard your online presence?
- Avoid signing up to services that you use personally with your business email account.
- Set up multi-factor authentication for your account as a safeguard against unauthorised access to your account by bad actors.
- Review privacy of your social media presence, do you need to share your phone number, email, or work location publicly?
- Is your email listed in any public data breach? Run your email accounts, personal or business, through HaveIBeenPwned.com to find out.
Sources:
Have I Been Pwned: Have I Been Pwned: Check if your email has been compromised in a data breach
Facebook Data Breach in 2021 533 million Facebook users’ phone numbers leaked on hacker forum (bleepingcomputer.com)
Netlog Data Breach in 2018 Microsoft Word – Communication to Users English – FINAL.DOCX
Attackers using SVG files to smuggle QakBot Malware onto Windows systems
A new distribution method to smuggle Qakbot malware onto Windows systems has been discovered. Phishing campaigns involving the Qakbot malware are using Scalable Vector Graphics (SVG) images embedded in HTML email attachments. The new distribution method was spotted by Cisco Talos, which said it identified fraudulent email messages featuring HTML attachments with encoded SVG images that incorporate HTML script tags.
HTML smuggling is a technique that relies on using legitimate features of HTML and JavaScript to run encoded malicious code contained within the lure attachment and assemble the payload on a victim’s machine as opposed to making an HTTP request to fetch the malware from a remote server.
The attack chain spotted by the Cisco Talos concerns a JavaScript that’s smuggled inside of the SVG image and executed when the unsuspecting email recipient launches the HTML attachment.
When the victim opens the HTML attachment from the email, the smuggled JavaScript code inside the SVG image springs into action, creating a malicious ZIP archive and then presenting the user with a dialog box to save the file. The ZIP archive is also password-protected, requiring users to enter a password that’s displayed in the HTML attachment, following which an ISO image is extracted to run the Qakbot trojan. The below image is an example of an email in the attack, with its HTML code by its side, revealing its malicious intent.
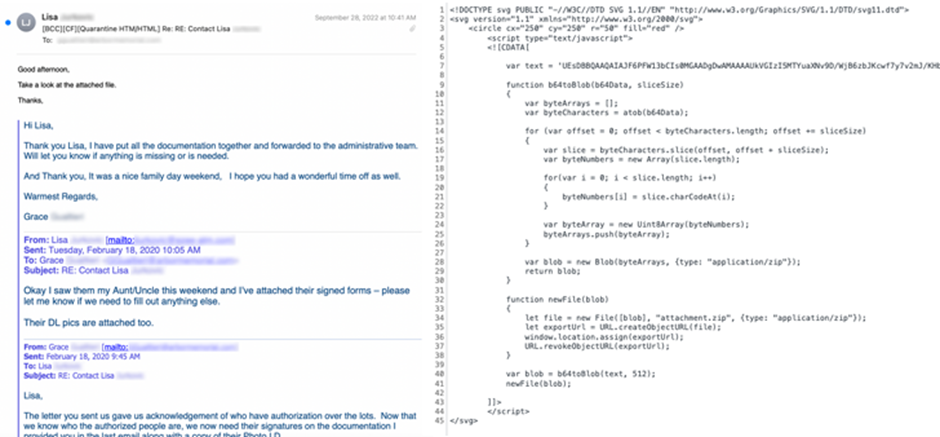
The finding comes as recent research from Trustwave SpiderLabs shows that HTML smuggling attacks are a common occurrence, with .HTML (11.39%) and .HTM (2.7%) files accounting for the second most spammed file attachment type after .JPG images (25.29%) in September 2022.
HTML smuggling’s ability to bypass content scanning filters means that this technique will likely be adopted by more threat actors and used with increasing frequency. However, having norm.’s Threat Detection service can prevent execution of potentially obfuscated scripts and prevent scripts from launching downloaded executable content, thus preventing this method of attack.
Sources:
HTML smugglers turn to SVG images (talosintelligence.com)
HTML File Attachments: Still A Threat | Trustwave
Hackers use Microsoft-signed malicious Windows drivers in post-exploitation activity
Threat actors are utilising malicious kernel-mode hardware drivers certified by Microsoft’s Windows Hardware Developer Program to bypass security checks. These drivers are being used in post-exploitation activity on systems where the attacker had already gained administrative privileges.
Microsoft was notified that several developers’ accounts for the Microsoft Partner Center were engaged in submitting malicious hardware drivers to obtain a Microsoft signature.
Mandiant and SentinelOne found a new toolkit consisting of two components named STONESTOP (loader) and POORTRY (kernel-mode driver). STONESTOP uses the POORTRY driver signed by Microsoft to terminate the associated protected processes or Windows services. This toolkit is being used by different threat actors in Bring Your Own Vulnerable Driver (BYOVD) attacks.
There is significant evidence that this toolkit is being used in multiple different attack types including ransomware attacks.
- Sophos analysis showed that Cuba ransomware operators used the BURNTCIGAR loader utility to install a malicious driver which was signed using Microsoft’s certificate.
- SentinelOne found Microsoft-signed toolkits in attacks against telecommunication, BPO, MSSP, and financial service businesses. Separately, it noted a similar Microsoft-signed driver used by the Hive ransomware against a medical entity.
- Mandiant identified a new threat actor named UNC3944 who are utilising the toolkit in attacks seen as early as August 2022, this APT is commonly known for gaining initial network access using SIM swapping attacks.
As multiple hacking groups are using Microsoft-signed drivers, security analysts assess that either the groups are leveraging a common criminal service for code signing or a supplier or service is designing and developing toolkits and drivers that other groups pay to access.
Microsoft has revoked several Microsoft hardware developer accounts that are associated with drivers used in cyberattacks. The company has released new Microsoft Defender signatures (1.377.987.0) to detect legitimate signed drivers in post-exploitation attacks. Users are suggested to update the signatures at the earliest and do a thorough scan of their environment to check for any suspicious activities. By utilising norm’s endpoint threat detection and response platform, with automatic up-to-date signatures to also detect the legitimate signed drivers which were abused.
In addition, Microsoft stated they are working with Microsoft Active Protections Program partners and Microsoft Partner Center to address these deceptive practices and prevent future customer impacts.
Sources:
I Solemnly Swear My Driver Is Up to No Good: Hunting for Attestation Signed Malware | Mandiant
Signed driver malware moves up the software trust chain – Sophos News
Mozilla fixes vulnerabilities that could have led to system takeover
Multiple high-impact vulnerabilities affecting Thunderbird, Firefox ESR, and Firefox were fixed by updates from Mozilla. These updates which addressed several vulnerabilities impacting the three aforementioned products, where if exploited, the flaws could have allowed arbitrary code execution and to take complete control of an affected system.
Mozilla released three advisories, addressing the issues with Thunderbird 102.6, Firefox ESR 102.6, and Firefox 108. All three of Mozilla’s products are impacted by one of the high-impact vulnerabilities, identified as CVE-2022-46878. According to Mozilla developers, Firefox 107 and Firefox ESR 102.5 both have memory safety issues. These flaws included those that appeared to have memory corruption, and with enough work, some of these could have been made to execute arbitrary code.
Another serious weakness, CVE-2022-46872, which affects the products of all three companies, might allow an attacker to view any file after taking control of a content process. Mozilla did point out that the particular flaw exclusively affects its Linux-only products. Attackers could use other critical flaws identified in the advisory to cause product crashes.
By utilising norm.’s Vulnerability Management and Patching service, software is kept up to date meaning devices are protected against vulnerabilities and exploits such as the above.
Further reading:
Security Vulnerabilities fixed in Firefox 108 — Mozilla
Mozilla Releases Security Updates for Thunderbird and Firefox | CISA
FortiOS critical vulnerability in SSLVPN component
Last week, norm. sent an out-of-band bulletin direct to our customers regarding a critical SSL-VPN vulnerability in FortiOS devices (CVE-2022-42475). We would like to use this opportunity to provide an update.
The positive news is that no further exploit attempts have been reported according to CISA.
However, there have been additional OS versions identified that are affected by the vulnerability, so if you run any of the versions below, please bring them into scope for patching purposes.
FortiOS version 6.0.0 through 6.0.15
FortiOS version 5.6.0 through 5.6.14
FortiOS version 5.4.0 through 5.4.13
FortiOS version 5.2.0 through 5.2.15
FortiOS version 5.0.0 through 5.0.14
Please note that the lowest version unaffected by this vulnerability is 6.2.12, with no 5.x.x fix available. Disabling SSL-VPN is still given as a valid workaround, which may be a more suitable short term mitigation for some customers with very old versions while potential upgrade impacts are considered.
Finally, there have been additional Indicators of Compromise identified. norm. has evaluated them and amended our detections accordingly.
References:
Known Exploit Catalogue: Known Exploited Vulnerabilities Catalog | CISA
CVE Reference: NVD – CVE-2022-42475 (nist.gov)
Vendor Advisory: PSIRT Advisories | FortiGuard
Original Discovery: This was discovered by FortiNet on 12 December 2022, potentially following a confirmed exploit attempt
Affected Versions:
FortiOS version 7.2.0 through 7.2.2
FortiOS version 7.0.0 through 7.0.8
FortiOS version 6.4.0 through 6.4.10
FortiOS version 6.2.0 through 6.2.11
FortiOS version 6.0.0 through 6.0.15
FortiOS version 5.6.0 through 5.6.14
FortiOS version 5.4.0 through 5.4.13
FortiOS version 5.2.0 through 5.2.15
FortiOS version 5.0.0 through 5.0.14
FortiOS-6K7K version 7.0.0 through 7.0.7
FortiOS-6K7K version 6.4.0 through 6.4.9
FortiOS-6K7K version 6.2.0 through 6.2.11
FortiOS-6K7K version 6.0.0 through 6.0.14
Mitigation:
Upgrade to FortiOS version 7.2.3 or above
Upgrade to FortiOS version 7.0.9 or above
Upgrade to FortiOS version 6.4.11 or above
Upgrade to FortiOS version 6.2.12 or above
Upgrade to FortiOS-6K7K version 7.0.8 or above
Upgrade to FortiOS-6K7K version 6.4.10 or above
Upgrade to FortiOS-6K7K version 6.2.12 or above
Upgrade to FortiOS-6K7K version 6.0.15 or above
Critical remote code execution vulnerability in SPNEGO extended negotiation security mechanism
Last week, norm. sent an out-of-band bulletin direct to our customers regarding a critical vulnerability in SPNEGO NEGOEX (CVE-2022-37958). We would like to use this opportunity to provide an update.
The positive news is that there has been no exploit publicly released yet so there is no evidence of affected systems being exploited.
However, more news sites are picking up on the news and reporting it. Any customers who utilise norm. Vulnerability Management have had a list of any affected assets uploaded to the documents area in smartbloc. LIVE. You can also use the vulnerability section in smartbloc. LIVE for live updates on which assets have been patched.
Further reading:
08th December 2022 Threat Bulletin
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: