
Google Addresses Two Pixel Zero-Days, CVE-2024-29748
The latest Pixel Update Bulletin from April 2024 has addressed two critical vulnerabilities, CVE-2024-29745 and CVE-2024-29748, that were being exploited. Here are the details:
CVE-2024-29745 – This vulnerability is an information disclosure flaw in the Pixel’s bootloader. The bootloader is a key component that loads the operating system into the phone’s memory. Forensic companies have been exploiting this vulnerability by rebooting devices into fast boot mode after the first unlock, enabling them to dump memory data. This could lead to local information disclosure with no additional execution privileges needed. The vulnerability was discovered by security researchers from GrapheneOS, a privacy and security-focused Android distribution.
CVE-2024-29748 – This vulnerability is an elevation of privilege bug in the Pixel firmware. The flaw allows local attackers to interrupt factory resets initiated by apps using the device admin API. This renders such resets insecure and could lead to local escalation of privilege with no additional execution privileges needed. Forensic firms have been exploiting this vulnerability to circumvent PIN protection and gain access to stored data. There is a possible way to bypass due to a logic error in the code. While Google’s firmware fix addressed part of the issue, GrapheneOS pointed out that it remains possible to halt the wipe by cutting power to the device. In response, GrapheneOS is developing a more comprehensive solution.
Both vulnerabilities were considered high-severity zero-day vulnerabilities impacting Pixel smartphones. Google has patched these vulnerabilities in the April 2024 update. All supported Google devices will receive an update to the 2024-04-05 patch level. Google encourages all customers to accept these updates to their devices.
By utilising norm.’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
References
Pixel Update Bulletin—April 2024 (source.android.com)
New Phishing Campaign by Threat Actor Group TA547
TA547 is a threat actor group which has recently started targeting German organisations using a tool for stealing information named Rhadamanthys, as part of a phishing campaign. According to Proofpoint, TA547’s use of Rhadamanthys marks a new development. Additionally, researchers suspect the actor employed a PowerShell script potentially generated by a large language model (LLM).
TA547 has a long resume of engaging in financially motivated cyber attacks. Initially gaining notoriety for trafficking Trickbot, the group has since utilized a variety of other prominent cyber crime tools such as Gozi/Ursnif, Lumma stealer, NetSupport RAT, StealC, ZLoader, and Adhubllka ransomware.
In recent times, TA547 has transitioned into an initial access broker (IAB) for ransomware attacks, demonstrating adaptability by employing geofencing tactics to target specific regions.
In the latest campaign, email messages impersonating the German company Metro AG contain a password-protected ZIP file. Upon opening, this file executes a remote PowerShell script to launch the Rhadamanthys stealer directly into memory. Notably, the PowerShell script includes detailed comments for each instruction, suggesting potential generation or rewriting using an LLM.
Proofpoint notes a shift in TA547’s techniques, including the use of compressed LNKs and the introduction of the previously unseen Rhadamanthys stealer. This highlights how threat actors leverage likely LLM-generated content in their malware campaigns.
Additionally, phishing campaigns have adopted unconventional tactics, such as directing recipients to click on links in emails which look like notifications for voice messages. These links lead to heavily obfuscated HTML content, running JavaScript code embedded within SVG images, which prompts users to enter their credentials on a second-stage page encrypted using CryptoJS.
Other email-based attacks have facilitated the rise of Agent Tesla, favoured for its affordability and versatile data exfiltration capabilities. Social engineering campaigns also manifest as malicious ads on search engines, enticing users to download bogus installers for popular software, ultimately deploying Nitrogen and IDAT Loader.
The infection chain associated with IDAT Loader utilises the MSIX installer to launch a PowerShell script, contacting a Telegram bot to fetch another PowerShell script. This script bypasses Windows Antimalware Scan Interface (AMSI) protections, triggering the execution of the loader, which subsequently loads the SectopRAT trojan.
In light of these evolving tactics, it’s crucial to remain vigilant against phishing emails. Be cautious when opening attachments or clicking on links, especially from unknown or suspicious sources. Verify the sender’s identity and the legitimacy of the email before taking any action. Additionally, consider implementing security measures such as email filtering and education programs to raise awareness among employees about the dangers of phishing attacks. By staying informed and practicing good cyber security hygiene, we can better protect ourselves and our organisations from falling victim to phishing scams.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
TA547 Uses an LLM-Generated Dropper to Infect German Orgs (darkreading.com)
TA547 Phishing Attack Hits German Firms with Rhadamanthys Stealer (thehackernews.com)
Unveiling Native Branch History Injection (BHI): A Menace to Intel Systems
Researchers from the Systems and Network Security Group at Vrije Universiteit Amsterdam have unveiled what they claim to be the “first native Spectre v2 exploit” targeting the Linux kernel on Intel systems. Dubbed Native Branch History Injection (BHI), this exploit facilitates the extraction of sensitive data from memory by circumventing existing Spectre v2/BHI mitigations. Tracked under CVE-2024-2201, this vulnerability affects modern processors from Intel, AMD, and Arm.
Although BHI was initially revealed in March 2022 as a technique to circumvent Spectre v2 protections in processors from Intel, AMD, and Arm, this latest development showcases its effectiveness, specifically against Intel systems. Despite Intel’s recommendations to disable Linux’s unprivileged eBPFs as a mitigation strategy, BHI demonstrates its ability to bypass this countermeasure.
Unlike previous methods reliant on eBPFs, Native BHI showcases that BHI can be achieved without them, affecting all susceptible Intel systems. Meaning that an unauthorised attacker could potentially exploit this vulnerability to extract privileged memory from the CPU by engaging in speculative jumps to a selected gadget as visualised in Figure 1 below.
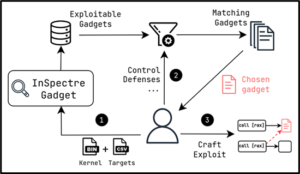
Figure 1 – Visualisation of Exploitation Chain
Existing mitigation techniques such as disabling privileged eBPF and enabling IBT (Indirect Branch Tracking) are deemed insufficient against BHI exploitation, as stated by the CERT Coordination Center. InSpectre Gadget, a program highlighted in the disclosure, identifies code fragments within the kernel that could be abused to evade Intel microprocessor safeguards and obtain secret data.
The impact of this exploit extends to various systems including Illumos, Red Hat, SUSE Linux, Triton Data Center, and Xen, though AMD asserts no awareness of any impact on its products. This revelation follows recent research on GhostRace, a variant of Spectre v1, and Ahoi Attacks, targeting hardware-based trusted execution environments (TEEs) like AMD SEV-SNP and Intel TDX.
GhostRace exploits speculative execution and race conditions to leak data from modern CPU architectures, while Ahoi Attacks utilise malicious interrupts to compromise the integrity of CVMs, potentially granting remote access and elevated privileges to threat actors. AMD acknowledges vulnerabilities in the Linux kernel implementation of SEV-SNP and confirms that fixes have been integrated into the main Linux kernel.
In summary, the disclosure of Native BHI underscores the persistent threat posed by Spectre vulnerabilities, emphasising the necessity for ongoing vigilance and mitigation efforts within the cyber security landscape.
Here at norm., we appreciate how difficult it is to keep on top of all these new exploits, so why not leave it to the professionals? Our Managed Threat Detection and Response package service provides near real-time security monitoring for your network, services, and devices. Using telemetry feeds, threat intelligence feeds, use cases and play books, the norm. Security Operations Centre (SOC) identifies and isolates threats in near real-time, giving you peace of mind 24 hours a day, every day.
References:
Researchers Uncover First Native Spectre v2 Exploit Against Linux Kernel (thehackernews.com)
New Exploit Bypasses Existing Spectre-V2 Mitigations in Intel, AMD, Arm CPUs (thehackernews.com)
GitHub – vusec/inspectre-gadget: InSpectre Gadget
‘GhostRace’ Speculative Execution Attack Impacts All CPU, OS Vendors (darkreading.com)
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: