
Ghostscript bug could allow documents to run system commands
Do people within your organisation use Ghostscript? You might say no but this is where it can get tricky, it could be imbedded in other programs and in use without you directly knowing.
It could be baked into package-based software services such as Linux distro, Homebrew on Apple, or Chocolatey on Windows. Having comprehensive conversion capabilities and flexibility performance Ghostscript is a Page Description Language (PDL) software.
Bad actors are always after ways in which to turn programs that are good against us. This can be seen in a product that is a widely used; The household extension; PDF (Portable Document Format). PDF files rely on PostScript code to define how to compose a document. Companies can use Ghostscript in the background to import EPS (Embedded PostScript) that might be downloaded from image libraries. It reads both EPS and or PDF program code which describes how to construct the pages of the document and then converts it into a format that displays it.
As the title of this article suggests versions older can be exploited, versions older than 10.01.2 are susceptible to bad actors using it for compromise. CVE-2023-3664 was reported on 21st June 2023 and the team at Artifex have already issued the software to fix the vulnerability. They stated in their press release “We recommend applying this security fix as soon as possible.”
Why was this possible? Ghostscript handling of files for output made it possible to send the output in pipe rather than a regular file (Pipes are system objects that pretend to be files). This can put the data into a temporary block of memory. When this is then actioned, it uses the data sat in the block of memory like it comes from a file on the disk. This feature enabled you to send out specially crafted filenames starting with %pipe% or |this gave you the chance to launch a command on the victim’s computer. Thankfully, the code has been updated to stop the use of %pipe% or |.
How do you fix the problem? If you use Ghostscript directly then update to 10.01.2 or other software services that I previously mentioned, then get the latest versions of these. If you have it in the form of a bundle the check with the provider about their Ghostscript update.
By utilising norm.’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
References:
Security Vulnerability fixed in Ghostscript 10.01.2 (artifex.com)
Ghostscript bug could allow rogue documents to run system commands – Naked Security (sophos.com)
CVE – CVE-2023-36664 (mitre.org)
Debian — Security Information — DSA-5446-1 ghostscript
How effective is ChatGPT when it comes to phishing sites?
ChatGPT has been identified as a significant step forward in AI, developed by OpenAI, it enables the public to be able to access a large amount of publicly available information. Everyday, security analysts deal with many types of warnings, but the most vulnerable is phishing attacks, which are the simplest way for hackers to assault their targets. It was therefore investigated to see if ChatGPT could aid in the identification of phishing sites.
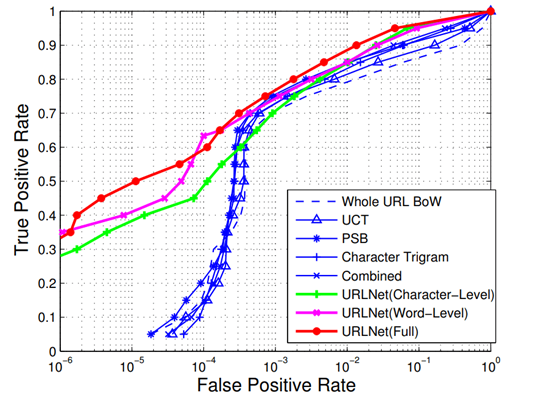
The URL has been utilised to determine whether the sender email address is fraudulent in the context of assisting security operators to accessing phishing emails. The reason behind choosing URL classification is due to the simplicity of integration into an LLM (Large language model). Modern LLM’s, such as ChatGPT, may only accept a limited number of symbols at a time. URLs are considered text, which is consistent with LLMs ability to process text. The two ways in which the question was addressed to ChatGPT was “Does the link lead to a phish website? and Is this link safe to visit?” In response to the first query, Kaspersky researchers recorded detection rates of 87.2 percent with a false positive of 23.2 percent and 93.8 percent with a false positive of 64.3 percent. From this it can be understood while ChatGPT has a successful rate in detecting phishing sites. The rate of false positives, however, cannot be overlooked either. To put this into context in relation to the first question of “is it phishing?”, in a well- known article called URL.net, in which Le et al. addressed a very similar job, the authors achieved almost the same level of detection rate (-85%) with a false positive rate of about 0.4% using a specifically built convolutional neutral network. For clarity, check the illustration below.
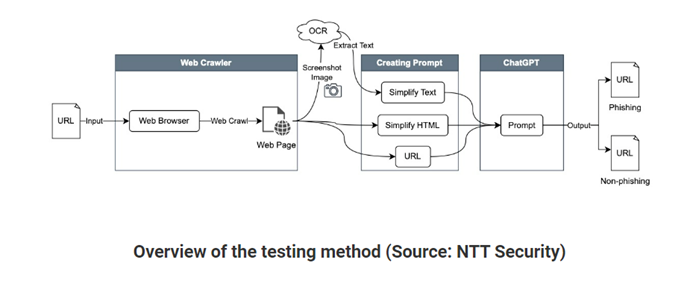
NTT security Japan researchers adopted a different strategy of adding additional information points, which resulted in improved performance. They entered the website’s URL, HTML, and text that was optical character recognition (OCR) extracted from the website. After evaluating one thousand phishing and non- phishing sites with the motive to detect social engineering methods and any other suspicious activity. The experiment brought about an increase in the accuracy percentage to 98.3 with a recall of 98.4 in GPT-4. The effectiveness of GPT-4 to eliminate false negatives has improved, according to a comparison between GPT -3.5 and GPT -4. They also emphasised that while ChatGPT was beneficial at accurately recognising tactics like fake malware infection warnings, fake login errors, phishing SMS authentication requests and identifying domain names that are not legitimate. It sometimes missed detecting domain squatting and specific social engineering approaches, as well as determining whether a legal domain name had several subdomains, and so on. Furthermore, it fared less well when tested with websites in various languages.
The above research shows it can be understood that ChatGPT appears to be a smart tool when used figuratively. It is a useful tool to get started, but without probing, integrating and non-linear thinking to examine the content, the outputs may not result with accuracy. Science has always been a human enterprise; we should embrace recent technologies rather than fear them, but not at the expense of losing the human element from science. This type of technology can help flesh-and-blood analysts by identifying suspicious sections of URLs and recommending potential attack targets. Additionally, it could improve traditional ML pipelines by being used in weak supervision pipelines. The best way to use ChatGPT proficiently should be used in conjunction with other forensic tools rather than as a sole means of detection.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
A Chat(GPT) about the future of scientific publishing (researchgate.net)
ChatGPT shows promise in detecting phishing sites (helpnetsecurity.com)
What does ChatGPT know about phishing? (securelist.com)
Detecting phishing sites using ChatGPT (researchgate.net)
US Federal Agencies expose hundreds of networking appliances to the internet
The Censys Research Team has revealed that US federal agencies have hundreds of publicly accessible network device management interfaces, creating a wide attack surface for remote unauthorised access to Government networks. A recently published CISA (the Cybersecurity & Infrastructure Security Agency of the US) directive – BOD 23-02 – in early June has begun the process of mitigating this threat, but Censys found hundreds of devices that are in violation of this new directive.
Censys set out to identify internet exposed management interfaces for firewalls, VPNs, routers, access points etc. – finding many popular networking devices including FortiGuard and SonicWall firewalls with publicly accessible management interfaces. Censys discovered numerous remote access protocols enabled on these devices including SSH, Telnet, FTP, SMB and SNMP. CISA’s BOD 23-02 directive mandates that these devices should never be exposed to the internet in such a way. These protocols have a long history of vulnerabilities and are still frequently targeted, especially when new 0-day exploits are published, and attackers scour the internet for vulnerable systems.
It has been a long-standing focus for the United States and its allies to understand and mitigate attacks on critical infrastructure and industrial control systems for several years, particularly focusing on state-sponsored attacks from Russia, China, and North Korea. Censys’ findings reveal that more work is required to lock down Government networks.
By utilising norm.’s managed Threat Detection & Response services you can ensure that your infrastructure is monitored around the clock for unauthorised remote access and service discovery/scanning. norm.’s Vulnerability Patch Management service ensures that your publicly accessible assets are secure and up to date with the latest security updates.
References:
Identifying CISA BOD 23-02 Internet-Exposed Networked Management Interfaces with Censys – Censys
Binding Operational Directive 23-02 Implementation Guidance | CISA
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: