
Zero-day exploit found and exploited in Barracuda’s ESG Appliances
Barracuda has recently revealed that threat actors based out of China have exploited a new zero-day vulnerability within their Email Security Gateway (ESG) devices to deploy backdoors on several of said devices.
The vulnerability is being tracked as CVE-2023-7102 and as of writing this article, the vulnerability is currently under analysis and has yet to receive a CVSS score. The vulnerability itself is related to arbitrary code execution residing within a third-party and open-source library named Spreadsheet::ParseExcel, which is used by the Amavis scanner within the gateway screen that scans Microsoft Excel email attachments for potential malicious files.
The threat actor group that has been attached to this activity is tracked by Mandiant as UNC4841, which coincidentally was linked previously with the exploitation of another Barracuda zero-day vulnerability earlier in 2023 (CVE-2023-2868). Exploitation of this new vulnerability can be accomplished by using a specially created Excel email attachment, which is subsequently followed by the deployment of newly developed variants of SEASPY and SALTWATER implants that allow for persistence and command execution.
The vulnerability in question could be considered quite severe, as it doesn’t require any interaction with a user. The way it works is that a threat actor would send an email to a target containing the specially crafted Excel file, which would then be scanned by the Barracuda EGS appliance and in turn, this would execute the malicious code hidden within the Excel file.
As of December 21st, 2023, Barracuda have released a security update that has been automatically applied across all devices and have reassured that no further action from customers is required. Barracuda also stated that a patch to remediate devices compromised by the vulnerability exploitation would be released the day after. This patch would target appliances which show indicators of the newly identified malware variants. Barracuda did not disclose the size of the compromise.
While the ESG vulnerability has been patched, the original exploit found in the Spreadsheet::ParseExcel Perl module (version 0.65) is still unpatched. This exploit has been given the CVE number of CVE-2023-7101, which advises downstream users to take remediation action at the appropriate level.
By utilising norm.’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
Sources:
Chinese Hackers Exploited New Zero-Day in Barracuda’s ESG Appliances (thehackernews.com)
NVD – CVE-2023-7101 (nist.gov)
NVD – CVE-2023-7102 (nist.gov)
Barracuda Email Security Gateway Appliance (ESG) Vulnerability (barracuda.com)
Unmasking and defending against Cryptocurrency Miners: Safeguard your Endpoints
As the crypto boom gains momentum once again, the allure for malicious actors seeking to use your computing power for their profit intensifies. Cryptocurrency mining malware are programs crafted to hijack a computer’s processing power for mining cryptocurrencies, often without the user’s awareness.
This can take many forms. Recently, three new crypto miner packages – modularseven, driftme, and catme – were uncovered in the Python Package Index (PyPI) open-source repository, capable of deploying a cryptocurrency miner on vulnerable Linux devices. Prior to their removal, these harmful packages amassed a total of 431 downloads in the past month.
Attackers are also utilising dictionary attacks to guess SSH credentials on poorly secured Linux SSH servers, and upon successful entry, they install port scanners and other malware. The goal is to compromise vulnerable servers for crypto mining activities.
Given the dynamic nature of crypto mining malware, endpoint behavioural analysis plays a pivotal role in identifying potential threats. Monitoring system resources and detecting abnormal usage patterns, such as sudden spikes in CPU or GPU activity without corresponding user actions, can serve as red flags.
Upon detection of a crypto miner, swift action like every detection of malware is imperative. Isolating the affected system, disconnecting it from the network, and terminating malicious processes are immediate steps to curtail further damage. Subsequently, completely removing the malware and conducting a thorough system scan ensures a clean and secure environment.
But what can you do to prevent it from getting on your endpoints in the first place?
Proactive measures are paramount in the ongoing battle against crypto miners. Educating end-users about the risks associated with downloading unfamiliar software and promoting cautious online behaviour can mitigate the chances of malware infiltration. Additionally, implementing intrusion detection systems and network monitoring tools adds an extra layer of defence against crypto mining threats. Regularly updating and patching software is equally crucial, as outdated programs often harbour vulnerabilities exploited by crypto miners.
In summary, as the cryptocurrency landscape continues to expand, so does the threat posed by crypto miners on piggybacking off the processing power on your endpoints. Vigilance, advanced cyber security tools, and user education are critical components in the fight against these malicious actors. By staying ahead and promptly responding to potential threats, organisations and individuals can prevent any unwanted applications hijacking your processing power.
Sources:
Three New Malicious PyPI Packages Deploy CoinMiner on Linux Devices | FortiGuard Labs (fortinet.com)
Beware: 3 Malicious PyPI Packages Found Targeting Linux with Crypto Miners (thehackernews.com)
Warning: Poorly Secured Linux SSH Servers Under Attack for Cryptocurrency Mining (thehackernews.com)
Beyond Phishing: Understanding the nuances of Spear Phishing and Whaling Attacks
Teach a man how to phish and he’ll be successful for a day, teach a man how to spear phish and he’ll be successful for life.
So, what is Phishing? Phishing is the deployment of fake emails by criminal actors, to elicit personal information or to make a financial gain. It is a form of social engineering that requires you as a user to take some form of action, this may be through a seemingly emails requesting personal data, licking a link or downloading an attachment.
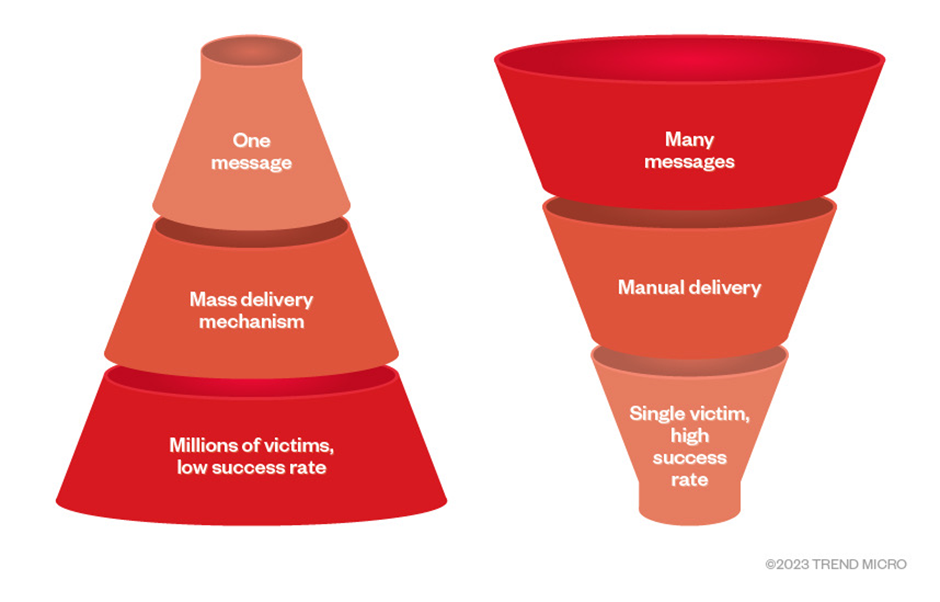
Phishing emails are sent out in large volumes and often have a low success rate, as the average click rate for a phishing campaign in 2021 was found to be 17.8% (AAG). However, that is not to say they’re not effective, as an estimated 90% of cyber-attacks begin with a phishing email (Cloudflare). In 2022, some of the most imitated companies were couriers (FedEx and DHL) and the likes of Google, LinkedIn, and Microsoft.
Guidance on how to handle Phishing Emails is readily available, LinkedIn is one source that has provided guidance on what to do if you receive a phishing email and what it is likely to look like, with common subjects relating to account suspension, security alerts and account termination. Similarly, companies like Evri do the same, stating poor language, unusual email addresses, lack of personal greetings and unrecognised addresses from links may indicate you’ve received a phishing email.
Spear phishing is an email phishing attempt with a targeted user. The sender can use open-source intelligence to collect personal information about the recipient and/or businesses they are attempting to contact. As a result, the actor can create a more tailored email, creating a false sense of security as the recipient may believe it is an internal communication. Examples of this may manifest as unprecedented document reviews that need downloading or a link that allegedly directs to a shared drive.
Whaling attacks, like spear phishing are targeted email phishing attempts however instead of being targeted at regular people or groups, the attacker’s victims are high-level executives within successful companies. Again, these attacks rely on open-source intelligence which is then used to deceive the employee into thinking they’re engaging in internal communications.
The cost of investigating spearfishing and whaling attacks tends to be much higher than a generic phishing campaign. A single email phish delivered to an employee can cost a business up to $85.33 if it takes up to 60 minutes to investigate (Hoxhunt). In contrast, a whaling attempt directed at FACC, an Austrian Aerospace company in 2016 cost the company $47 million (Fortinet).
If you receive an unexpected email requesting you to redirect a parcel or an email from your boss asking you to send some employee information to HR out of the blue, double-check. It is always better to be safe than sorry.
References:
Phishing: Spot and report scam emails, texts, websites and calls (ncsc.gov.uk)
What Is Phishing? A Brief Guide to Recognizing and Combating Phishing Attacks (comptia.org)
The Latest 2023 Phishing Statistics (updated January 2024) (aag-it.com)
Introducing Cloudflare’s 2023 phishing threats report (cloudflare.com)
Phishing emails (linkedin.com)
How to spot and report potential fraud (evri.com)
How much does phishing really cost businesses? (hoxhunt.com)
What is a Whaling Attack (Whaling Phishing)?
The Future of Whaling Attacks – AI-Powered Harpoon Whaling (trendmicro.com)
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: