
Unmasking and defending against Cryptocurrency Miners: Safeguard Your Endpoints
As the crypto boom gains momentum once again, the allure for malicious actors seeking to use your computing power for their profit intensifies. Cryptocurrency mining malware are programs crafted to hijack a computer’s processing power for mining cryptocurrencies, often without the user’s awareness.
This can take many forms. Recently, three new crypto miner packages—modularseven, driftme, and catme—were uncovered in the Python Package Index (PyPI) open-source repository, capable of deploying a cryptocurrency miner on vulnerable Linux devices. Prior to their removal, these harmful packages amassed a total of 431 downloads in the past month alone.
Attackers are also utilising dictionary attacks to guess SSH credentials on poorly secured Linux SSH servers, and upon successful entry, they install port scanners and other malware. The ultimate goal is to compromise vulnerable servers for crypto mining activities.
Given the dynamic nature of crypto mining malware, endpoint behavioural analysis plays a pivotal role in identifying potential threats. Monitoring system resources and detecting abnormal usage patterns, such as sudden spikes in CPU or GPU activity without corresponding user actions, can serve as red flags.
Upon detection of a crypto miner, swift action like every detection of malware is imperative. Isolating the affected system, disconnecting it from the network, and terminating malicious processes are immediate steps to curtail further damage. Subsequently, completely removing the malware and conducting a thorough system scan ensures a clean and secure environment.
But what can you do to prevent it from getting on your endpoints in the first place?
Proactive measures are paramount in the ongoing battle against crypto miners. Educating end-users about the risks associated with downloading unfamiliar software and promoting cautious online behaviour can mitigate the chances of malware infiltration. Additionally, implementing intrusion detection systems and network monitoring tools adds an extra layer of defence against crypto mining threats. Regularly updating and patching software is equally crucial, as outdated programs often harbour vulnerabilities exploited by crypto miners.
In summary, as the cryptocurrency landscape continues to expand, so does the threat posed by crypto miners on piggybacking off the processing power on your endpoints. Vigilance, advanced cyber security tools, and user education are critical components in the fight against these malicious actors. By staying ahead and promptly responding to potential threats, organisations and individuals can prevent any unwanted applications hijacking your processing power.
References:
Three New Malicious PyPI Packages Deploy CoinMiner on Linux Devices | FortiGuard Labs (fortinet.com)
Beware: 3 Malicious PyPI Packages Found Targeting Linux with Crypto Miners (thehackernews.com)
Warning: Poorly Secured Linux SSH Servers Under Attack for Cryptocurrency Mining (thehackernews.com)
The importance of password security
Do you think that Password123 is secure enough?
For most of us, the Internet is an integral part of our daily routine. Whether you like to read the news from The Guardian, apply for jobs on LinkedIn, read your Outlook emails or update your wardrobe thanks to Asos, you will likely have an account to do so.
Passwords are responsible for protecting the personal information behind your online accounts. This information can include your bank details, your home address, or your phone number, and when your data is more valuable than oil it is important to ensure its security.
How could an attacker gain access to your password?
There are a variety of methods at an attacker’s disposal when it comes to gaining credential access. In one scenario it may start with a phishing email which harbours a fake login window, harvesting your credentials. It could be through a password spray, where the attacker will test a selection of the most commonly used passwords against your username. The actor may also attempt to brute force the account, this can be done through some popular tools like “John The Ripper”. These tools can hash passwords to find matches that have been leaked in data breaches, or it will attempt to run every word found in a dictionary to find a password match. It depends on the amount of time, knowledge, and resources available to the attacker as to which method they may choose.
Anything that can be easily guessed should not be used as a password. The longer and the more complex the password, the more difficult it is to crack. Pure Cloud Solutions recommends a minimum of 12 characters, with an assortment of upper and low case letters and special characters works best. A password of this intricacy is said to take around 34 years to crack.
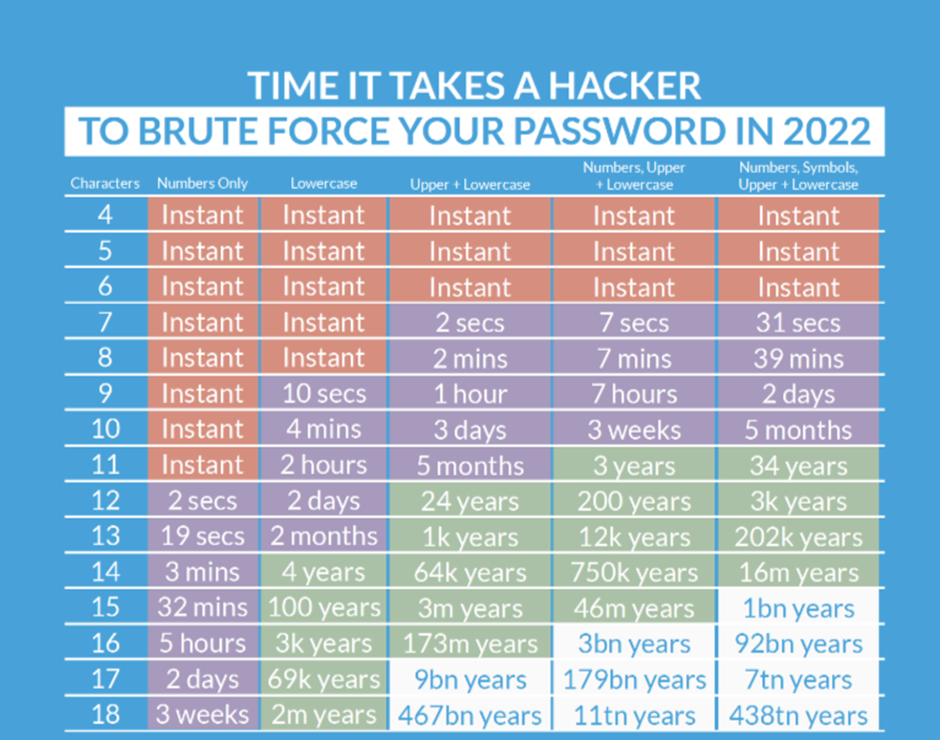
So how can you protect your passwords?
Make sure that all of your passwords are long and complex, making them more difficult to crack. In addition to this, make sure that all of your passwords are unique, do not reuse your passwords for multiple accounts. If you learn that your account details have been found in a data leak, make sure that you change your password as soon as possible. Having many accounts and many passwords to remember can be a challenge, to help mitigate forgotten passwords you can store them in a reliable password manager, but it is important to bear in mind that if someone gains access to this, they will be in possession of all of your passwords.
Another way to protect your accounts is by ensuring that your software is up to date. As soon as a software update is available for your apps and devices installing it will not only provide you with the newly released features but also often provide any patches for exploits that have recently been discovered, which can protect you from malware and viruses. Finally, enabling multi-factor authentication on your accounts will make it more difficult for an attacker to gain access to your accounts. Every time you attempt to sign into an account you will be prompted with a code to verify that you are gaining access to your account, and not an attacker. Setting up multi-factor is quick, easy and will help protect your data going forward.
References:
The New Black Gold: How Data Surpassed Oil in Value (LinkedIn.com)
7 Ways Hackers Steal Your Passwords (sentinelone.com)
How long will it take to hack your password? (purecloudsolutions.co.uk)
Turn on 2-step verification (2SV) (ncsc.gov.uk)
CISA Warns Users of Known High-Impact iOS and macOS Flaw (Patched)
The United States Cybersecurity and Infrastructure Security Agency (CISA) announced on Wednesday 31st of January the addition of a high-severity flaw affecting iOS, iPadOS, macOS, watchOS, and tvOS to their Known Exploited Vulnerability (KEV) list based upon evidence suggesting active exploitation of the aforementioned exploits. This vulnerability is currently being tracked as CVE-2022-48618, with a CVSS score of 7.8.
The exploit concerns a bug within the kernel code that can allow an attacker with arbitrary read and write capabilities to bypass pointer authentication. This particular vulnerability may have been exploited against versions of iOS released before iOS 15.7.1, says an Apple spokesperson regarding the exploit.
Apple has stated that the problem has already been addressed with improved checks, although it is not currently known how the vulnerability has been weaponized in real-world cyber-attacks at this time. An interesting observation made in regard to this exploit is the fact that patches for this vulnerability were released in late 2022 with the release of iOS, iPad OS, and tvOS 16.2 alongside macOS Ventura 13.1 and watchOS 9.2. However, the public disclosure of this occurred more than a year later in January 2024. Interestingly, Apple did resolve a similar flaw in the kernel with the 15.6 versions of iOS and iPadOS which occurred in July 2022. The CVE in question was CVE-2022-32844 which featured a CVSS score of 6.3.
A statement from Apple was released at the time, stating that “An app with arbitrary kernel read and write capability may be able to bypass pointer authentication”, and that “A logic issue was addressed with improved state management” in regard to the vulnerability.
Resources
CISA Warns of Active Exploitation Apple iOS and macOS Vulnerability – The Hacker News
CVE-2022-48618 – NIST
Preparing your app to work with pointer authentication – Apple
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: