
Credential stealing phishing campaign
Threatlabz and Microsoft have just uncovered a new strain of a large-scale phishing campaign around mid-June this year propagated as part of the phishing as-a-service (PhaaS) cybercrime model. The Microsoft intelligence team stated in a series of posts on X that “this development in the PhaaS ecosystem enables attackers to conduct high volume phishing campaigns that attempt to circumvent MFA protections at scale”. It uses an adversary-in-the-middle (AiTM) attack approach that can circumvent multi-factor authentication. The end users of Microsoft’s email services who work in businesses are the intended targets of this attack. In certain instances, this phishing attempt resulted in the compromise of an executive’s work email, which was then used to send other phishing emails as part of the same campaign. The campaign continues to be potent, and the threat actor registers new phishing domains practically daily. The words “password reset” and “password expiry” were utilised in several domain names. Some of the domain spoofing password reset theme examples are:
- expiryrequest-mailaccess[.]com
- expirationrequest-passwordreminder[.]com
- emailaccess-passwordnotice[.]com
- emailaccess-expirynotification[.]com
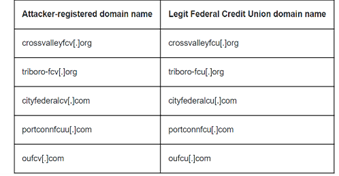
The majority of the organisations that were targeted were based in the US, UK, New Zealand, and Australia. The bulk of the organisations targeted were in the FinTech, Lending, Finance insurance, Accounting, Energy, and Federal Credit Union industries, according to cloud data telemetry. This list of targeted industry verticals is not all-inclusive.
An email with a malicious link is sent to the victim to start the phishing attempt. Some malicious links were supplied directly in the email body, while others were contained in the HTML file that was attached to the email. Numerous techniques were used to route users to phishing websites. Using websites intended for legitimate use by web developers to quickly create new code pages, paste a redirect code with the most recent phishing site’s URL into them, and then send the link to the hosted redirect code victims in bulk. The campaign uses a client fingerprinting process where the moment user visits the page is shown JavaScript code that was stolen from the FingerprintjS project. This code’s goal is to gather information from the client’s browser. Unlike conventional credential phishing kits, AiTM phishing attempts finish the authentication process with the real mail provider’s server. They can accomplish this by serving as a MiTM proxy and relaying all correspondence between the client(victim) and the server (mail provider).
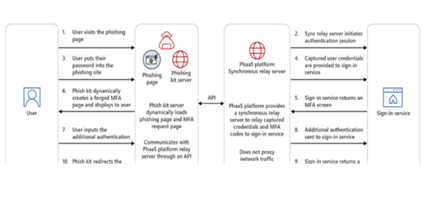
One of the ways that phishing kits with AiTM capabilities operate is by using reverse proxy servers (phishing pages) to route traffic to and from the client and a legitimate website while covertly capturing user credentials, two-factor authentication codes, and session cookies. Another approach uses synchronous relay servers presented with “a copy or mimic of a sign-in page, like traditional phishing attacks,” Microsoft said. The actor group storm 1295 which created the Greatness PhaaS platform provides synchronous relay services to the other attackers. Cisco Talos initially identified Greatness as a service in May 2023 that allows fraudsters to target business users of the Microsoft 365 cloud service by employing convincing login and decoy sites.
The ultimate goal of the phishing attack in question is aimed to steal session cookies giving threat actors access to privileged systems without having to reauthenticate. Users should take extreme care not to open attachments or links in emails sent from unreliable or unknown sources. Users should check URL in the browser’s address bar before entering any credentials as a best practice.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
Phishing-as-a-Service gets smarter (thehackernews.com)
Microsoft warns of Adversary-in-the-middle uptick on phishing platforms (infosecurity-magazine.com)
Large-scale AiTM attack targeting enterprise users of Microsoft email services (zscaler.com)
Operation Duck Hunt: Major disruption to Qakbot malware network
700,000 Qakbot infections have been taken down worldwide putting a substantial dent in the botnet’s operations – the US Department of Justice and FBI, working together with international partners, announced on Tuesday 29th August [1]. Codenamed ‘Operation Duck Hunt’, the FBI and partners seized $8.6m of fraudulent cryptocurrency.
Qakbot, aka QBot/Quakbot/Pinkslipbot, is a banking trojan malware that has been on the scene since 2007. Qakbot is primarily delivered via phishing emails, embedded within Office document files. The malware steals banking credentials and sensitive information from infected devices but has abilities to drop follow-on malware, beacon to command-and-control (C2) servers, and log user keystrokes.
Qakbot is a tool in the arsenal of several criminal groups – Conti, Black Basta, ProLock among others – to distribute and support ransomware attacks because of its ability to control vast numbers of compromised devices via a botnet.
Operation Duck Hunt redirected Qakbot botnet traffic to servers owned and controlled by the FBI and its partners, instructing infected devices to download a Qakbot uninstallation file to detach victim machines from the botnet.
The UK’s National Crime Agency reports that it has taken down UK-based Qakbot command-and-control servers [2]. While this is hailed as a significant breakthrough against cybercrime, one of the largest led by the US, we can expect that the criminal groups affected will move to new botnets or construct new attacker infrastructure.
By utilising norm.’s managed Threat Detection & Response service you can ensure that your devices are monitored 24×7 for malware delivery and detonation, and that your web traffic is inspected to detect malicious activity.
References:
Office of Public Affairs | Qakbot Malware Disrupted in International Cyber Takedown | United States Department of Justice
Qakbot: cybercrime service taken out in international operation – National Crime Agency
WinRAR vulnerability, have you updated yet?
Do you or your company use WinRAR? Then you need to read this. A WinRAR zero-day vulnerability has been found by Group-IB, it enables threat actors to take advantage of hiding malicious code in zip archives posing as files like .jpg or .txt and others. This code may also have been distributed on crypto currency trading forums meaning that this could even being used by smaller threat actors.
CVE-2023-38831 has a score of 7.8 which is classified as high. According to Group-IB over 500 million users worldwide use WinRAR, making this software one of the most popular compression tools available. This means that the vulnerability does not only effect crypto currency traders but many users across multiple industries. When a user receives an archive, the likelihood is that it is opened with WinRAR, resulting in a potentially dangerous situation for any business.
With this posing such a risk RARLAB have acted quickly with a beta patch being released on the 20th of July 2023 and the final update version being released on 2nd August 2023, meaning anything before version 6.23 should be updated to protect against the vulnerability.
By utilising norm.’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
References:
Traders’ Dollars in Danger: CVE-2023-38831 zero-Day vulnerability in WinRAR exploited by cybercriminals to target traders (group-ib.com)
CVE-2023-38831 Detail (nist.gov)
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: