
Google addresses actively exploited zero-day vulnerability in Chrome Browser
Google has released emergency updates to address a zero-day vulnerability in its Chrome browser. CVE-2023-5217 is a high-severity vulnerability that can lead to program crashes or arbitrary code execution. Google has mentioned in the advisory that the vulnerability is being exploited in the wild.
In this batch of updates, Google has also addressed two more high-severity vulnerabilities, CVE-2023-5186 and CVE-2023-51987. CVE-2023-5186 is a use after free vulnerability existing in Passwords and CVE-2023-5187 is a use after free vulnerability in Extensions.
CVE-2023-5217 is a heap buffer overflow vulnerability in VP8 compression format in libvpx. Libvpx is a free software video codec library from Google and the Alliance for Open Media (AOMedia). CVE-2023-5217 is the fifth zero-day vulnerability addressed by Google Chrome since the start of the year. The list includes:
- CVE-2023-4863 (August) – Heap buffer overflow in WebP
- CVE-2023-3079 (June)- Type confusion in V8
- CVE-2023-2136 (April) – Integer overflow in Skia
- CVE-2023-2033 (April) – Type confusion in V8
Google has made an update related to CVE-2023-4863 by providing a new identifier for this vulnerability, CVE-2023-5129. However, specifically for Google Chrome, this vulnerability is tracked as CVE-2023-4863.
Google Chrome versions before 117.0.5938.132 are affected by this vulnerability. Customers are requested to upgrade to the latest stable channel version, 117.0.5938.132, for Windows, Mac, and Linux.
References:
Google Chrome stable channel update for desktop 27 (chromereleases.googleblog.com)
Prevalence of ransomware in phishing attacks
According to the most recent ransomware statistics, phishing is the most common technique of ransomware distribution. Pursuant to a recent analysis, 75% of 1,400 firms questioned, experienced a ransomware attack, indicating the continuous presence of the threat in the business world.
26% of respondents reported that they had encountered a significant increase in email threats during the previous year, 88% of which were victims of ransomware. The original phishing attack’s primary goal is to obtain credentials rather than specifically stealing data with ransomware. According to a survey of 2,249 social engineering instances, 63% led to the compromise of credentials, which was higher than the percentages for the compromise of internal data (32%) and personal data (21%).
Hackers can get access to internal networks by using credentials to pose as a legitimate user. They may be able to spread ransomware from within the network whilst remaining undetectable and increase their attack, encrypting and deleting data before internal staff have a chance to react. The main mode of distribution for the ransomware Revil, seemed to be phishing. In 2021, instances utilising Revil frequently began with a ‘QakBot’ phishing email, according to IBM’s X-Force. This email would urge the recipient to pay an outstanding invoice or address another issue. Hackers have occasionally intervened in talks to introduce malicious link. When the email is opened, the target is prompted to unintentionally allow the QakBot banking malware to be dropped into a system. The enterprise may then be taken over by threat actors, who would undertake reconnaissance before attempting to breach data.
The table below depicts the top 10 countries targeted with ransomware attacks:
| Israel | India |
| South Korea | Kazakhstan |
| Vietnam | Philippines |
| China | Iran |
| Singapore | UK |
Snatch ransomware attacks, which are provided under the ransomware- as-a-service (RaaS) paradigm, are the ransomware attack of concern at present. The entity has been running a leaks website since November 2021, threatening to reveal stolen data if a ransom is not paid. According to the FBI and CISA, “some victims reported receiving a fake call from an unknown female who claimed affiliation with Snatch and detected them to the group’s extortion site.“
The entity establishes command-and-control (C&C) communication over HTTPS and leverages compromised administrator credentials to get enduring access to the network of victim. According to the FBI and CISA, a Russian bulletproof hosting company hosts the C&C server. The snatch threat actors spend up to three months on victims’ networks before deploying ransomware, looking for important data to steal and locating systems that they can encrypt.
Additionally, they try to turn-off security software. Once activated, Snatch alters registry keys, lists the system, looks for particular processes and creates harmless processes to run different batch files. It occasionally tries to remove volume shadow copies as well. In order to avoid endpoint detection programmes whilst encrypting victims’ files, the ransomware has also been observed rebooting devices in SafeMode. The software appends hexadecimal characters to file and folder names and places a ransom note in each, instructing victims to communicate through email or the Tox platform.
While Governments have made steps to prevent ransomware, including passing legislation and regulation such as strengthening law enforcement resources, these measures have not been effective in stemming the flow of attacks. Ransomware’s continual evolution has left a path of financial loss, data breaches, and operational interruptions in its wake, emphasising the critical need for strong defences and threat intelligence capabilities.
Real-time threat intelligence provides proactive ransomware defence by supplying information on threat actors, strategies, and targets. This allows organisations to reduce operational risks and protect their assets. Threat intelligence provides access to threat actor and malware maps, which show and prioritise the risks that are most important to you in real-time. From there, one can utilise intelligence cards to detect and deploy blocks or alerts for ransomware signs or behaviours, as well as the threat actors who employ them. Leveraging threat hunting playbooks can also be a proactive approach to search for indicators throughout the network before being attacked.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
Latest ransomware statistics (aag-it.com)
Ransomware attacks record in UK (therecord.media)
Ransomware changing why threat intelligence is essential (recordedfuture.com)
Critical infrastructure organizations warned of snatch ransomware attacks (securityweek.com)
Russian zero-day vendor announces $20m payouts for iOS and Android exploits
The Russian zero-day vulnerability platform Operation Zero announced on September 26th an increase in the largest payout for iOS and Android mobile exploits, with the largest maximum now set at $20,000,000.
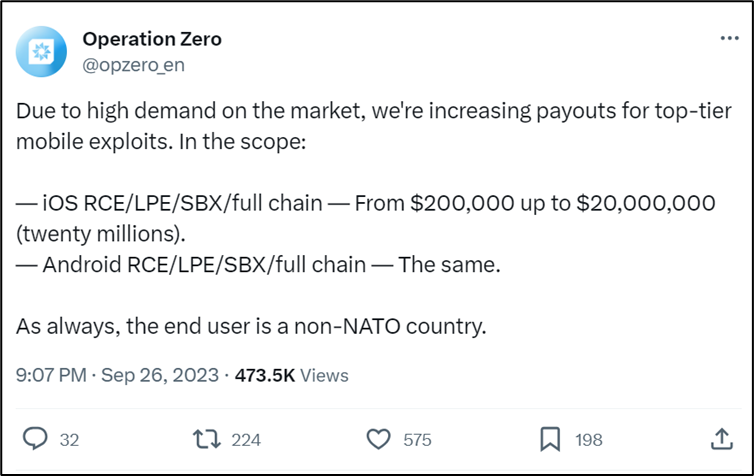
Operation Zero confirms that payouts will now range between $200,000 and $20,000,000 for remote code execution (RCE), local privilege escalation (LPE), and sandbox escape (SBX) exploits for both iOS and Android. This is a significantly higher maximum payout than competitor companies like Zerodium which had previously set ground-breaking payouts of $1,000,000 for iPhone exploits back in 2015.
Background: Zero-days are invaluable to nation states and advanced persistent threat actors (APTs) and are stockpiled in their thousands for conducting espionage among other tasks. As product vendors like Microsoft began to take responsibility of their own product security in 2002 under the “Trustworthy Computer Initiative”, the prices of exploits and zero-days began to rise as vulnerabilities began to get patched before making their way to the exploit market.
Bill Gate’s 2002 initiative paved the way for more ‘bug bounty’ programs, offering bug hunters and infosec professional’s alternative, or even primary, cash flow for their work – which for many years prior was disregarded by software vendors as hackers simply trying to break their products.
Operation Zero’s move represents how effective the bug bounty programs set up by Apple and Google have been at discovering and responding to zero-day exploits, forcing private companies, like Operation Zero, to significantly raise their payouts to entice security researchers into not disclosing their exploits directly to Apple and Google.
Operation Zero also added in their statement “As always, the end user is a non-NATO country.”, and when asked for comment by Lorenzo Franceschi-Bicchierai of YahooNews, “CEO Sergey Zelenyuk declined to say. “No reasons other than obvious ones,” he said.” Operation Zero’s clients are Russian private or government organisations only, offering access to zero-day exploits to Russian companies.
Managed Threat Detection & Response from norm. includes retroactive IoC detection for zero-day exploit attacks that can give you peace of mind that your networks are monitored around the clock for exploit activity.
References:
Operation Zero on X (twitter.com)
How to Sell Your Zero-Day (0day) Exploit to ZERODIUM (zerodium.com)
‘Jailbreak’ for iPhones wins $1m bounty | Hacking | (theguardian.com)
Bounty – Apple Security Research (security.apple.com)
Google Bug Hunters – Google Bug Hunters (bughunters.google.com)
Russian zero-day seller offers $20M for hacking Android and iPhones (yahoo.com)
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: