The Advanced Persistent Threat Group, TA577, are a prolific cybercrime group known for several high-profile attacks and deployments of Cobalt Strike. In their latest series of attacks, they’ve switched tactics, focusing on harvesting NTLM (NT LAN Manager) hashes via targeted phishing campaigns.
In this blog, Isaac Jackson, norm.’s Senior Penetration Tester, explores the world of NTLM hashes, their implications, and how to safeguard your organisation against this threat.
What are NTLM hashes?
NTLM hashes are cryptographic representations of passwords within the Windows operating system for authentication. When a user logs in to a Windows system, their password is hashed using the NTLM hashing algorithm. This hash is then compared to the stored hash value associated with the user account. If the hashes match, the user is granted access.
Historically, NTLM hashes were used in older versions of Windows for authentication purposes and continue to be supported in modern versions for backward compatibility. However, due to security weaknesses, such as susceptibility to various types of attacks like brute force and pass-the-hash, NTLM authentication is generally considered less secure in comparison to contemporary methods like Kerberos or stronger cryptographic protocols like NTLMv2.
NTLMv2 incorporates stronger a stronger hashing algorithm than the previous version, increasing the time taken for a hacker to run brute-force attacks, and implement protections against pass-the-hash style attacks. Whilst this can minimise the potential usage by an attacker, it is not immune to rule based dictionary attacks. Recognising this vulnerability is paramount for securing systems where NTLM authentication is in use, and when implementing a password policy within your organisation.
How is TA577 harvesting NTLM hashes?
TA577 employs a script that generates a malicious HTML page containing a meta refresh tag. This tag refreshes the page after a set period, directing the victim to a non-existent file share controlled by the attacker.
The attacker hosts this file share on a server equipped with a SMB listener. When the victim’s browser requests access to the file share, it unwittingly sends its NTLM hash along with the request to authenticate with the server. The attacker can then capture this hash, and use in pass-the-hash attacks, use offline brute force to give plaintext credentials, or simply use it to enumerate information about the domain and its users.
How to protect against this attack?
For Windows 11, and later versions, the SMB client provides the option to block NTLM for remote outbound connections. This effectively prevents the transmission of the NTLM hash as an authentication method to the attacker-controlled server. More information on this preventative method can be seen found on the Microsoft Community Hub. For older systems, blocking all outbound SMB traffic (typically ports 445 and 139) can be enforced through a firewall rule. However, this approach may potentially interfere with legitimate SMB requests if these are in use by your organisation.
How does this attack work in the wild?
Consultants at norm. have reconstructed the attack and developed a proof-of-concept script to detail how this attack works.
Initially, a custom python script is utilised to create the phishing page. In this instance, a company branded page entitled “payscales.html” which is subsequently compressed. Within this page resides a meta refresh tag that, when ran locally on a machine, will reach out to the attackers’ server in order to retrieve the file share.
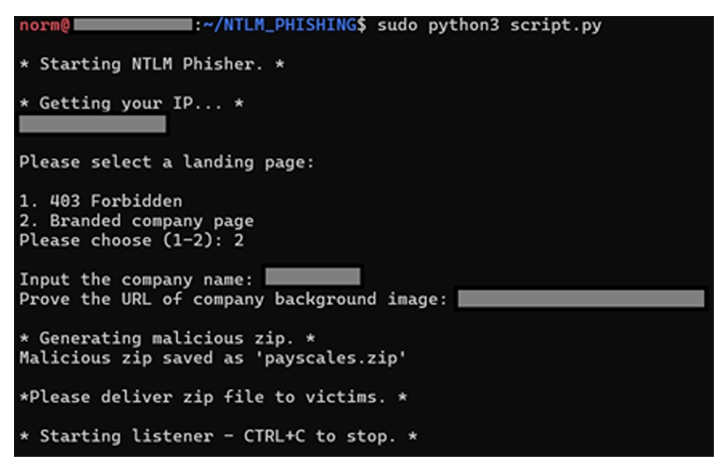
Fig 1 – Custom python script automating the generation of phishing page
![]()
Fig 2 – Malicious meta refresh tag embedded in HTML source code.
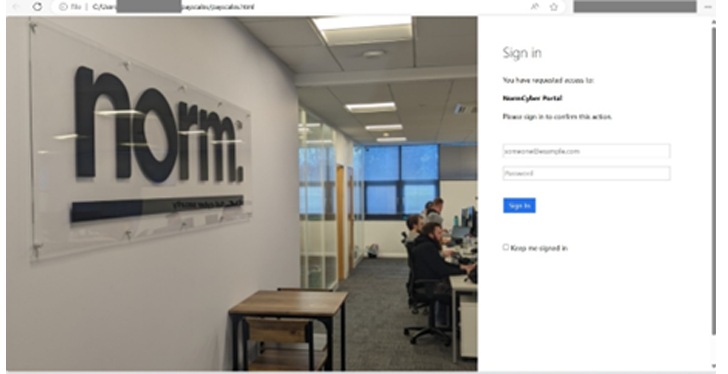
Fig 3 – landing page generated by custom script.
Subsequently, the script initiates a SMB listener, facilitating incoming connections to authenticate with the malicious server upon requesting the file share. The zip file containing the HTML page is then dispatched to victims. The rationale behind zipping the file rather than sending it as a page is to encourage the targets to download the file locally before opening. This strategy aims to exploit one of the principles of social engineering. For instance, consider the following example, which is designed to induce fear and curiosity.
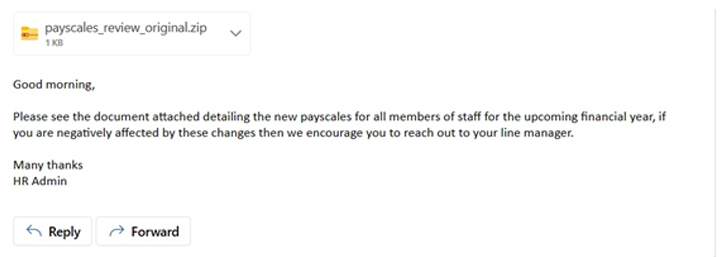
Fig 4 – email sent to targets containing the zipped HTML page.
Upon downloading and opening the page, the victim is presented with the landing page detailed earlier, and then the meta refresh tag reloads the content and initiates a SMB request to the attacker. The accompanying NTLM hash is then captured and can be used for further attacks.

Fig 5 – NTLM hash captured on attacker machine instantly on refresh tag initiation.
Conclusion
In conclusion, the evolving tactics of cybercriminal groups like TA577 underscore the persistent threat landscape organisations face today. Their shift towards acquiring NTLM hashes through targeted phishing campaigns highlights the importance of understanding and mitigating vulnerabilities associated with legacy authentication methods.
TA577’s approach to harvesting NTLM hashes via malicious HTML pages demonstrates the need for robust defence strategies. Implementing measures like blocking NTLM for remote outbound connections, as supported by Windows 11 SMB client, can significantly reduce the risk of hash theft. For older systems, firewall rules blocking outbound SMB traffic may serve as a temporary solution, albeit with potential interference to legitimate operations.
As organisations continue to fortify their cyber security posture, it’s crucial to stay vigilant against emerging threats and adopt proactive measures to safeguard sensitive data and systems. By understanding the tactics employed by threat actors like TA577 and implementing effective countermeasures, organisations can better defend against evolving cyber threats and protect their digital assets.

Written by Isaac Jackson
Isaac Jackson, a seasoned offensive security expert, currently holds the position of Senior Penetration Tester at NormCyber. Proficient in both infrastructure and web application penetration testing, Isaac remains committed to proactively addressing evolving threats. He specialises in crafting exploits for emerging vulnerabilities to facilitate effective client remediation efforts, earning accolades for his payloads, including recognition from esteemed organisations like Hak5. Isaac’s adeptness at uncovering intricate attack pathways within networks empowers norm.’s clients to promptly fortify their infrastructure against potential threats.