
15 million public-facing services vulnerable to CISA KEV flaws
Over 15 million publicly facing services are susceptible to at least one of the 896 vulnerabilities listed in CISA’s KEV (known exploitable vulnerabilities) catalogue. Research has been undertaken to identify vulnerable systems exposed to cyberattacks from threat actors, whether state-sponsored or ransomware gangs. The findings from this research are particularly worrying because the examined vulnerabilities are known and highlighted in CISA’s KEV catalogue as actively exploited by hackers, so any delays in their patching maintain a large attack surface, giving threat actors numerous potential targets. Microsoft Windows, Adobe Flash Player, Internet Explorer, Google Chrome, Microsoft Office, and Win32k make up one-fourth of CISA’s KEV catalogue.
Researchers used the well-known Shodan web scanning service to find endpoints that are still vulnerable to CVEs added to CISA’s KEV catalogue. Using public knowledge search queries, the researchers found 15 million instances vulnerable to 200 CVE’s from the catalogue. With over half of those instances, vulnerable to one of the 137 CVEs concerning Microsoft Windows, making this component a top priority for defenders and an excellent target for attackers. Of the other remaining non-Windows vulnerabilities, over half of them are over five years old, with over 4.5 million devices being identified as vulnerable to KEV’s discovered between 2010 and 2020. Meaning that these machines did not patch the relevant published updates for years even though a patch was released, and these vulnerabilities are known to be exploited in the wild.
Notable CVE’s in the research are:
- CVE-2021-40438: medium-severity information disclosure flaw appearing in almost 6.5 million Shodan results, impacting Apache HTTPD servers v2.4.48 and older.
- Proxyshell: a set of three vulnerabilities impacting Microsoft Exchange, which Iranian APTs chained together for remote code execution attacks in 2021. Shodan returns 14,554 results today.
- ProxyLogon: a set of four flaws impacting Microsoft Exchange, which Russian hackers extensively leveraged in 2021 against U.S. infrastructure. There are still 4,990 systems vulnerable to ProxyLogon, according to Shodan, with 584 located in the U.S.
- HeartBleed (CVE-2014-0160): medium-severity flaw impacting OpenSSL, allowing attackers to leak sensitive information from a process memory. Shodan says a whopping 190,446 are still vulnerable to this flaw.
The 15 million is considered to be an estimate and a conservative one at that. Mainly because this data set contains only non-duplicates. As mentioned above, these are publicly known vulnerabilities which are also known to be actively exploited. Using data from Greynoise, which monitors and categories vulnerability exploitation attempts, the following was observed:
At the top of the list with the most exploited flaws is CVE-2022-26134, having 1,421 results in GreyNoise, and 816 exploitation attempts in the past month. This critical-severity flaw in Atlassian Confluence Server and Data Centre allows a remote attacker to execute an Object-Graph Navigation Language expression on the vulnerable instance. Other flaws ranking high in the list include CVE-2018-13379, a pre-authentication arbitrary files read impacting FortiOS devices, which has 331 results on GreyNoise, and Log4Shell, a malicious code execution bug on Log4J2 that had 66 exploitation attempts in the past month.
By utilising norm.‘s Vulnerability Patch Management service, you can ensure firstly that software is up to date with the latest security patches, greatly reducing the attack surface, by adding norm.‘s Threat Detection & Response module on top of this, you can ensure this attack surface is protected as best as possible.
Sources:
Known Exploited Vulnerabilities Catalog
Get to Know KEV In Our New Research Report
Barracuda researchers uncover three novel phishing tactics used by cybercriminals
In recent reports from their email security platforms, Barracuda researchers were able to uncover three tactics used by cybercriminals that, while uncommon in relation to other phishing attacks, were widespread, with between 11 and 15% of all companies using Barracuda software being targeted, often with multiple attacks occurring.
The first of these attack types uses Google Translate web links to hide malicious URLs. The attackers will use the Google Website Translate feature to send a Google hosted URL in an email that will lead to a phishing website. The attackers using this type of attack use translation services to translate a benign URL, which they will send to their targets via an email. The attackers will then change the payload to malicious content after the email has been delivered, as this will bypass most gateway-based defenses in place. These attacks are commonly known as Translation-Based Phishing or Translation Deception attacks. Phishing attacks such as these are also prone to using non-supported or poorly formed HTML pages, as these will avoid translation entirely. In this use-case, Google will provide a link back to the original URL while stating that it was unable to translate the underlying website, meaning that a user will not be able to see the true intentions of the URL.
The second of these attacks uses images, which are becoming increasingly prevalent in phishing attacks due to their ability to bypass text-based phishing detection and increased user likelihood to trust images on emails which are sent from a seemingly trustworthy source. These attacks operate by attaching a link onto the image, which could include a link to a call-back phone number or a malicious phishing site. Image based phishing attacks can come in many forms, but a common use of this attack type involves the use of fake invoice images, sent to a target from a seemingly legitimate source. The use of these attacks has risen significantly over the last decade and are likely to rise even further due to the advancements for their use.
The third of these attacks use special characters such as zero-width Unicode, non-Latin script, spaces, or punctuation to avoid detection. These forms of attacks are especially difficult to detect as special characters can sometimes be used for legitimate public uses within an email, including email signatures. These attacks can be highly effective as the characters used are not visible to the target receiving the message, and are only visible in the HTML code, so a target will only see what appears to be a legitimate plain text email, arousing no suspicion. The use of special characters is commonly used in typo-squatting attacks, where attackers register a look-alike domain using special characters to deceive recipients. These have since become more widely used within the body of an email as a measure to further deceive a target into believing the email is from a legitimate source. Several other attacks use similar techniques, such as Punycode, URL Spoofing and Watering Hole attacks.
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
Sources:
Threat Spotlight: 3 novel phishing tactics
Phishing campaigns continuing to use reCAPTCHA walls
norm.’s Security Operations Centre Analysts were alerted to an inbound phishing email to a norm. mailbox and investigated immediately. Tearing back layers of obfuscated, jumbled JavaScript embedded within, revealed a phishing site using Google’s reCAPTCHA service, a technique used by phishing campaign operators first reported by Barracuda in 2020 [1] and later by Unit42 in 2021 [2].
ReCAPTCHA is a free website security tool offered by Google that can tell humans and bots apart, something that some of us might find frustrating if you are constantly being asked to click photos of cats or fire hydrants.
Phishing campaign operators use human authentication services like this to prevent automated URL analysis tools from conducting site analysis, stopping any phishing detection in its tracks. Combined with well-crafted site styling and content the addition of verification services can also result in phishing targets trusting malicious, credential stealing sites.
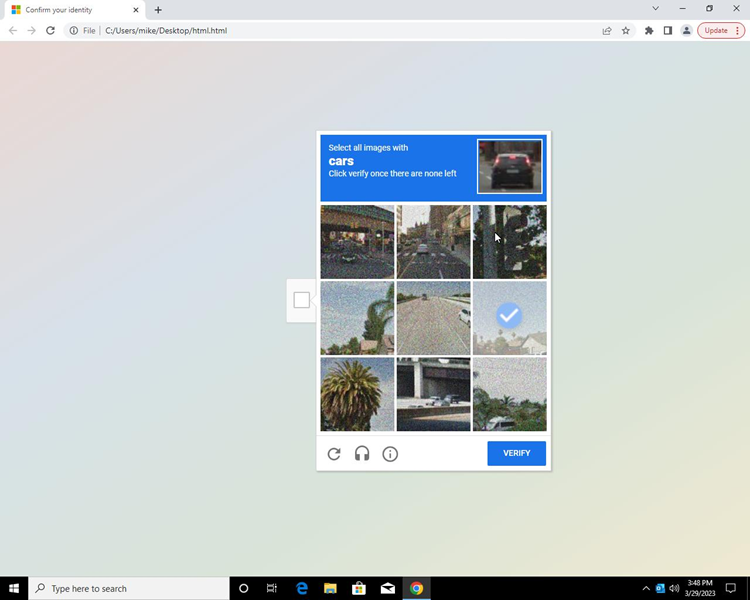
The attachment of this email contained obfuscated JavaScript, hiding a HTML Iframe element pointing towards secureonlineorderform[.]com.
This technique remains in use today, so norm. is using this opportunity to shine the light once again on this phishing technique. If an email lands in your inbox asking for urgent action or correspondence, take extra time to assess the following:
- Treat any content with zero trust, not assumed trust, when you see any link to a legitimate business. Attackers are continuing to target the assumed levels of trust that consumers have with well established brands and services. This is not an indicator that an email or attachment is inherently safe.
- Is the email expected? Does it relate to any ongoing, legitimate business?
- Do you recognise the sender or the business that they appear to be representing?
- Does the sender convey a high sense of urgency, or is there any emphasis on taking immediate action? Veiled threats and deadlines should be treated as suspicious.
- Report any suspicious emails to management or your IT team for investigation and forward the email to report@phishing.gov.uk – the UK Government’s dedicated suspicious email reporting service.
By utilising norm.’s Cyber Safety & Phishing service, users can be more aware of tactics used in phishing attempts, while norm.’s Threat Detection & Response service can detect and respond against malicious files and email attachments.
Sources:
[1] Threat Spotlight: Malicious use of reCaptcha (barracuda.com)
[2] Discovering CAPTCHA Protected Phishing Campaigns (paloaltonetworks.com)
[3] Step 5 – Avoiding phishing attacks – NCSC.GOV.UK
WordPress ‘Elementor Pro’ vulnerability
A vulnerability within WordPress Elementor pro plug was reported on 18th March 2023 by Jerome Bruandet of The Ninja Technologies Network with a CVSS v3.1: 8.8 (High) potentially leaving millions of websites potentially vulnerable to attack.
For the attack to work you need to be running the Elementor Pro plug in and not the free version available at wordpress.org. The website needs to have WooCommerce activated, the attacker needs to be an authenticated user to run code that could allow full site takeover.
When its activated it loads modules that register a couple of AJAX actions, one of them being pro_woocommerce_update_page_option that uses Elementor’s built-in editor. It calls update_option, a function that can be used to modify WordPress options in the database.
This function is supposed to allow admins and shop managers to update some specific WooCommercce options, but user inputs are not validated and does not restrict access to high privilege users only.
An authenticated user can leverage this vulnerability to create an admin account by enabling registration and setting the default role to administrator. The bad actor can then change the admin email address and redirect all traffic to an external malicious website by changing the site URL among many other possibilities.
Recommendations
An updated version was released on 22nd March 2023, if you are running a version that is 3.11.6 or below you should update to version 3.11.7. If you are running this plugin, then you should have been notified about the vulnerability.
Reference
High severity vulnerability fixed in WordPress Elementor Pro plugin.
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: