Cyber security and personal data breaches are costly, stressful and time consuming. Sadly, they’re also a fact of business life. Here’s our guide to preparing for, mitigating and getting back on your feet after a breach has occurred – fast!
Although it will vary according to the type and scale of the breach, typically cyber security incident response follows the below stages, based on the NIST Incident Response Lifecycle
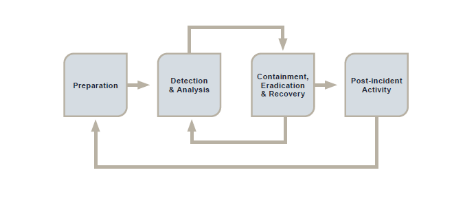
As with all incident response, preparation is vital. Primarily this equates to developing an incident response plan which identifies the key people, teams and procedures required to execute the plan and achieve the desired outcomes.
Traditionally, companies will develop a cyber security incident response plan and identify a team of people who are responsible for the key decisions and actions that need to be taken as part of that plan. These people can be either internal or external specialists, but must have the necessary technical, operational and legal expertise. Increasingly, organisations are turning to an external Cyber Security Incident Response Team (CSIRT) due to the level of experience and independence they bring.
Regardless of whether you decide on an internal or external team, your incident response plan should include:
✔ Defining what does, and does not, constitute a cyber security and/or personal data breach
✔ Determining a process for categorising the breach, which will depend upon factors such as whether personal data has been stolen, and if the affected organisation is still able to trade
✔ Detailing the level of response required in each case according to the categorisation
✔ Specifying how systems will be preserved for forensic examination
✔ Outlining the procedure for deciding who needs to be notified and when – including employees, customers, partners, the ICO and law enforcement
This last point is worth highlighting as often incident response is focused on the technical elements of identifying affected systems and getting them back up and running, but communicating with the relevant authorities is just as important. The ICO takes a dim view of organisations that don’t report a breach, or even worse try to cover it up. An expert in data protection law should be able to liaise with the ICO, clearly articulating the salient points and outlining the measures that are being taken to prevent future breaches. This will have a direct impact on whether the ICO decides to take enforcement action or not.
There’s a lot of hype about the impact of cyber security and personal data breaches and the havoc they can cause. The fact is that the level of disruption is directly linked to how well prepared an organisation is. Having a well thought out response plan is a vital part of that preparation, and will dramatically reduce the fall out should a breach occur.
If you’d like to find out more about the people, process and data protection elements of responding to a security incident, and how to stop it becoming a crisis, take a look at our recent webinar, Help! We’ve been breached – now what?
If you need help preparing for or responding to a cyber security and/or personal data breach, you can contact our expert team using the details below:
Phone: 020 3855 5303
Email: help@normcyber.com

Written by Natasha Scott
Natasha Scott is Head of Marketing at NormCyber and is responsible for driving awareness and engagement for the brand across all channels and audiences. She has worked in the technology industry for over 20 years in a variety of communications and marketing roles, and has a particular passion for all things digital and content-related.
