NormCyber threat bulletin: 06th March 2024

Critical VMWare Vulnerability Prompts Uninstall Request for EAP Plug-in

Critical VMWare Vulnerability Prompts Uninstall Request for EAP Plug-in

VMWare has recently urged all users to uninstall the deprecated Enhanced Authentication Plug-in (EAP) following the uncovering of a critical security vulnerability. The vulnerability in question is being tracked as CVE-2024-22245, has been scored 9.6 on the CVSS scale and is described as an arbitrary authentication relay bug.
In an advisory statement published by the company, it was stated that a malicious actor could trick a domain user with the EAP plug-in installed on their web browsers into requesting, then relaying service tickets for arbitrary Active Directory (AD) Service Principal Names (SPNs). EAP is a software package which is designed to allow users to directly log into vSphere’s management interfaces and tools via their web browser. However, EAP is not included by default and is also not part of vCenter Server, ESXi or Cloud Foundation.
Another discovery made in the same EAP tool was a session hijack flaw, which is being tracked as CVE-2024-22250 and given a CVSS score of 7.8. This vulnerability can allow malicious actors with unprivileged local access to a Windows OS to seize a privileged EAP session.
Ceri Coburn, from the company Pen test Partners has been credited with the discovery and reporting of both the vulnerabilities back in October 2023. It is also not clear as to why VMWare took many more months to advise on remediation methods for this vulnerability.
It is worth noting that the vulnerabilities only effect users who have added the EAP to Windows systems to connect VMWare’s vSphere via the vSphere client. VMWare have stated that the vulnerabilities will not be addressed, instead requesting that users remove the plug-in altogether to mitigate the threat. The plug-in can easily be removed from client systems using the OS’s system for uninstalling software.
By utilising NormCyber’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
References:
VMware Alert: Uninstall EAP Now – Critical Flaw Puts Active Directory at Risk (thehackernews.com)
VMware Arbitrary Authentication Relay and Session Hijack Vulnerabilities Impacting Deprecated Enhanced Authentication Plug-in (EAP) (CVE-2024-22245 & CVE-2024-22250) – Qualys ThreatPROTECT
VMSA-2024-0003 (vmware.com)
Mac Users Being Targeted By Scammers
Researchers from MalwareBytes have discovered cyber criminals targeting Mac users with fake calendar invites. Research shows attackers are using this attack method to target users who have shown an interest in cryptocurrency in Telegram chat groups; however, this model can easily be replicated to target any Mac user.
The attack is relatively simple, the attacker will send a link supposedly to add a meeting to the targets calendar, however, in reality this link actually runs a script to install malware on the targets machine. In order to appear genuine, the attackers often impersonate official cryptocurrency investors and companies, forcing these companies to make public announcements which deny they are the operators of certain accounts.
An example of this is the cryptocurrency investor Signum Capital, they were being impersonated by an attacker on Telegram who was sending out invites by direct message to their targets. In this particular attack, the attacker reached out to targets by direct messaging users in a cryptocurrency chat group and asking if they have an interest in hearing about the opportunity in a call or meeting. If the victim showed an interest, this is when the attacker would send out an invitation for a meeting. When the time came for the victim to join the meeting, the invitation link did not work, the victim would reach out and the attackers would claim this is a known issue, caused by a “regional access restriction” and to resolve this issue by running a script.
This attack method of using AppleScript is not new, as MalwareBytes director of core technology Thomas Reed states “it has been used against Mac users with moderate frequency by malware creators over the years”, he goes on to explain this is because “it has the advantage of being very easy to write, and if compiled, is also extremely difficult to reverse engineer… Also have the advantage of being able to very easily get administrator permissions.”
By utilising the Cyber Safety and Phishing module provided by NormCyber users can recognise potential scams, by learning typical phishing tactics and signs of phishing links.
References:
Malicious Meeting Invite Fix Targets Mac Users (MalwareBytes)
Ransomware: An Overview
Ransomware is everywhere in the news, but what is it? Ransomware is a form of malware, which is designed to encrypt your personal information on your device. Ransomware accounted for 17% of all cyber attacks in 2022, and the cost of ransomware attacks was estimated to cost $30 billion in 2023 overall.
There are several types of ransomware. Crypto ransomware is one of the most infamous types, it encrypts your data and files and requires a decryption key in order to regain access to your information. A Locker ransomware may display a countdown clock to convince you of the urgency required, whilst simultaneously locking your system and preventing you from accessing any applications. Scareware may impersonate an anti-virus program and it will notify you of an issue with your device, such as a virus. It will then direct you to a payment page to fix the problem. This could result in your screen being filled with pop-up ads, the device being locked, or the sole purpose could have been for you to pay the ransom. Another variant is Doxware ransomware, in addition to encrypting your files it will also threaten to expose private information. An example of this can be seen with Ransoc, this malware informs the user that it has detected abuse material on their device and if they do not pay the ransom they will be imprisoned.
The final type of ransomware is Ransomware as a Service (RaaS). Anyone who lacks the ability to create or distribute the malware themselves can approach an operator, who will carry out the attack, collect the ransom and potentially restore access on their behalf, in return for a portion of the ransom. One of the most harmful forms of ransomware stems from a group called LockBit, first seen in 2019, who operate Ransomware as a Service. Although law enforcement scored a win by disrupting their activities last week.
Ransomware can be spread through phishing emails, enticing the recipient to click on a link or open an attachment within the email. Clicking on malicious URLs within phishing emails or on websites can enable the ransomware to begin auto-installing on the device, once it is installed it then has the ability to spread. A lack of network segmentation gives an attacker free range and can inhibit environment restorations.
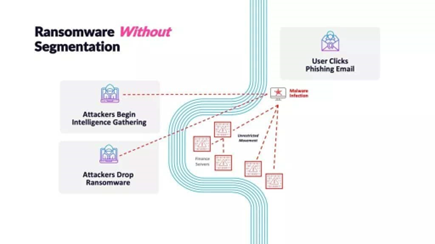
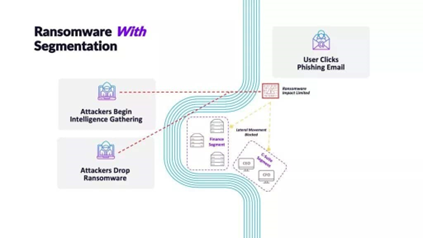
If you become a victim of ransomware, paying the ransom isn’t always the best idea, although it may seem the easiest. Paying the ransom can indicate to other actors that you are worth attacking as you are likely to pay again. Furthermore, there is nothing to stop the actor from sending repeated ransom requests to see how much they can accrue. Even if the ransom is paid, there is no guarantee that they will give you the decryption key, or that the decryption key will even properly work.
The best action to take is to contact your security service provider, who will run an incident response exercise. This could include isolating the device, disconnecting devices from the network if they are exhibiting suspicious behaviours, assess the damage; and check for encrypted or oddly named files, Ascertain the source of the ransomware you are dealing with, and restore your systems from backup if possible. If the malware has been eradicated it may be possible to find decryption keys for the specific strain of malware you have been dealing with, if none of these options are viable the only option may be to start rebuilding. Another important step is to inform law enforcement of the attack, in addition to the Information Commissioner Office, if a data breach has been observed.
By utilising the incident response from NormCyber we provide assistance in both mitigation, containment, and recovery of an incident.
Resources
How Does Ransomware Actually Spread? (Akamai)
5 types of Ransomware (CrowdStrike)
Law enforcement disrupt world’s biggest ransomware operation (Europol)
What is ransomware? (IBM)
What is Doxware? (MonsterCloud)