NormCyber threat bulletin: 8th February 2023

Emotet returns with new methods of evasion

Since July 2022, Emotet had appeared as though it had ceased its operations, however, recently run Emotet botnets (namely Epoch4 and Epoch5), have came back to life and begun sending out spam emails once again. These phishing emails used various methods to lure victims into first opening them, and then downloading and executing excel files, with macros used to download the Emotet dropper.
Emotet is famously known for steadily evolving and adding new techniques for evasion, which has aided it in its high likelihood of successful infection. Part of this evolving is also able to host an array of modules, each used for different aspects of information theft that report back to their command-and-control (C2) servers. From process monitoring to grabbing Microsoft Outlook email addresses, Emotet has been observed to inject both proprietary modules and readily available freeware tools, adding and tweaking them over the years with alarming effectiveness.
In it’s recent resurrection, Emotet has turned to good old fashioned social engineering to manually override the new Mark-Of-The-Web flag feature introduced by Microsoft and explained in our previous threat bulletin. When users open an Excel attachment, they are instructed to move the newly downloaded file into Excel’s ‘Templates’ folder. This directory is chosen as this folder is automatically trusted by Microsoft, any file executed from here is ignored by the Protected View functionality, allowing any macros to run without hinderance.
Once the macros are run, it is back to normal operations as far as an Emotet infection goes, they reach out to the internet to download and execute the Emotet malware. The Emotet dropper is downloaded to a randomly generated folder under %UserProfile%\AppData\Local as a .dll file. This .dll file is also given a randomly generated name. Once downloaded, macros use regsvr32.exe to execute Emotet. At this point, Emotet will run in the background, reaching out to its C2 server in order to download additional malware. It also achieves persistence on the system by creating the registry key so that it may stay active on the local machine, awaiting further instruction.
By utilising norm’s Cyber Safety & Phishing service, users can be more aware of tactics used in phishing attempts. In addition, NormCyber’s Threat Detection & Response service can detect against malicious files such as known Emotet files.
Lockbit operators launch LockBit Green
LockBit has remained one of the most active global threats last year, with more victims than any other ransomware group, such as Conti, Hive, and BlackCat. Since its launch, the LockBit operation has gone through numerous iterations with its encryptor, starting with a custom one LockBit Red and moving to LockBit Black (aka LockBit 3.0).
Ransomware operators often lookout for a way to take their ransomware to the next level. Recently, LockBit operators developed a new variant of their malware available on their portal. Dubbed LockBit Green, this new variant was designed to include cloud-based services among its targets.
Much like LockBit Black being derived from BlackMatter’s source code, the new variant has a significant overlap (89%) with Conti ransomware v3. LockBit Green’s ransom note is identical to the one used by the LockBit Black variant; only the ransom note filename has been changed to !!!-Restore-My-Files-!!!.txt. Additionally, It uses random extensions rather than the standard .lockbit extension.
LockBit has a reputation as a RaaS group and its operators keep releasing new variants with additional capabilities. Experts estimate ex-Conti members will prefer LockBit Green as they probably feel comfortable using Conti-based ransomware and LockBit Green could have a big impact on victim organisations. It has been reported that there have already been at least five victims hit with the new LockBitGreen. By utilising NormCyber’s smartbloc. service, you can ensure you are at the forefront of protection.
New high-severity vulnerabilities discovered in F5 BIG-IP products
F5 has warned of a high severity flaw impacting BIG-IP appliances, that could lead to denial of service or arbitrary code execution. The issue is rooted in the iControl Simple Object Access Protocol (SOAP) interface and affects the following versions of BIG-IP –
In its advisory, the company has explained “A format string vulnerability exists in iControl SOAP that allows an authenticated attacker to crash the iControl SOAP CGI process or, potentially execute arbitrary code.” Additionally, they added “In appliance mode BIG-IP, a successful exploit of this vulnerability can allow the attacker to cross a security boundary.”
Given that the iControl SOAP interface runs as root, a successful exploit could permit a threat actor to remotely trigger code execution on the device as the root user. This can be achieved by inserting arbitrary format string characters into a query parameter that’s passed to a logging function called syslog, Bowes said.
F5 noted that it has addressed the problem in an engineering hotfix that is available for supported versions of BIG-IP. As a workaround, the company is recommending users restrict access to the iControl SOAP API to only trusted users. Additionally, by utilising NormCyber’s Vulnerability Patch Management service, applications are kept up to date to mitigate any risk as soon as possible.
Phishing sites using dynamic content to deceive victims
The most common phishing attacks that Norm. are alerted to will contain the victim’s email address within the phishing URL which is then auto filled into the phishing site. AhnLab has recently reported that phishing campaign operators have begun using dynamically generated content to customise credential harvesting sites to make their attacks even more legitimate to their victims. The spoofed logon page will change appearance to include imagery associated with the victim’s organisation. This has been made possible by a very simple feature made available by Google, of all the places. Google’s Favicon (website icon) lookup service can grab imagery for a provided domain.
This link will grab the favicon for Norm Cyber.
This allows dynamic content to be generated on the fly which makes phishing sites more deceiving for victims.
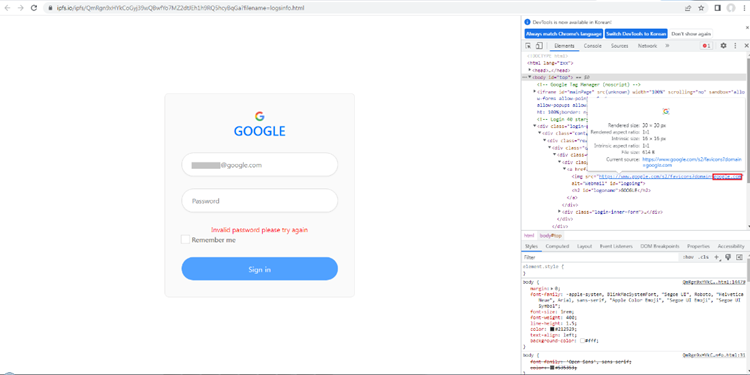
Source: AhnLabs https://asec.ahnlab.com/en/46786/
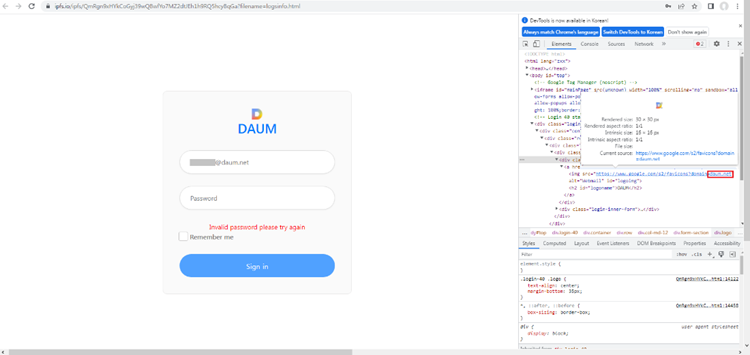
Source: AhnLabs https://asec.ahnlab.com/en/46786/
How to spot phishing fundamentals
Are you expecting the email, has it appeared out of the blue?
Is the sender calling for immediate or urgent action to be taken, or is the sender claiming to hold a position of authority? Has a deadline been set for action to be taken?
Check for poor grammar, spelling, and the use of multiple fonts or non-English characters. Phish operators use these techniques to bypass keyword filters.
Sources:
How to spot a scam email, text message or call – NCSC.GOV.UK
Ransomware targeting VMware ESXi
Admins, hosting providers, and the French Computer Emergency Response Team (CERT-FR) warn that attackers are actively targeting VMware ESXi servers unpatched against a two-year-old remote code execution vulnerability to deploy a new ESXiArgs ransomware. Tracked as CVE-2021-21974, the security flaw is caused by a heap overflow issue in the OpenSLP service that can be exploited by unauthenticated threat actors in low-complexity attacks.
CVE-2021-21974 affects the following systems:
The attack is primarily targeting ESXi servers in version before 7.0 U3i, and through the OpenSLP port 427.
According to a Censys search, approximately 3,200 VMware ESXi servers worldwide have been compromised in the ESXiArgs ransomware campaign. The ransomware encrypts files with the .vmxf, .vmx, .vmdk, .vmsd, and .nvram extensions on compromised ESXi servers and creates a .args file for each encrypted document with metadata.
A patch for the vulnerability being exploited has been available since 23 February 2021 and norm strongly recommends applying the patch as soon as possible but adds that systems left unpatched should also be scanned to look for signs of compromise. By utilising NormCyber’s Vulnerability Patch Management service, ESXi servers would be patched and therefore mitigated against this attack.
Further reading:
06th February 2023 Data Protection Bulletin