NormCyber threat bulletin: 9th November 2022

OpenSSL pre-announced critical vulnerability

OpenSSL pre-announced critical vulnerability

On 25th October, OpenSSL pre-announced a security-fix release of their open-source secure communication software. This software is used so extensively across organisations of all shapes and sizes that it attracted a lot of attention in the industry.
On 1st November, a patch was released, and two vulnerabilities were announced; one that could allow attackers to perform Denial of Service (DoS) attacks and another potentially Remote Code Execution (RCE), depending on the system context. The vulnerabilities have since been downgraded to high severity due to challenges attackers face in weaponizing the vulnerability in practice, but NIST still encourages prompt remediation.
How can NormCyber help?
Vulnerability Management from NormCyber detected the vulnerable OpenSSL installations more than 24 hours before the remediating patch was released. This allowed our customers to identify devices in need of remediation and align resources ahead of time, relieving some of the pressures associated with high profile remediations.
Manual detection logic
If you don’t have vulnerability scanning and detection capabilities, see below for manual detection steps.
Linux
Check for the vulnerable versions of OpenSSL by running ‘openssl version’ command.
Windows
Check for the vulnerable versions of OpenSSL by reviewing the OpenSSL DisplayName value in these registry keys:
• “HKLM\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall”
• “HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall”
References
CVE Reference: NVD – CVE-2022-3602 (nist.gov) & NVD – CVE-2022-3786 (nist.gov)
Vendor Advisory: OpenSSL Project – Advisory
Original Discovery: This issue was reported to OpenSSL directly on 17th October 2022 by Polar Bear
Affected Versions: OpenSSL prior to 3.0.7
Mitigation: Upgrade OpenSSL to 3.0.7
Hackers exploit PayPal invoicing bug to launch advanced phishing attacks
A new take on an old phishing technique has become known. Traditionally, phishing emails can be analysed by investigating the source of the email or more technical analysis such as headers, DMARC and DKIM. This would in turn highlight something amiss or contacting the sender would bring a compromised account to light. However, how would a suspicious email be analysed if it is sent from a genuine company where an account hasn’t been compromised?
This is the situation recipients of PayPal emails are asking themselves after a new method of exploiting genuine PayPal emails has emerged. The main cause behind the exploit is the PayPal invoicing feature. PayPal invoicing is a feature developed to ease the payment process of purchases made outside of PayPal. It allows businesses to send an email to their customer, invoicing them for the services/products that the business has provided.
The problem is that scammers have figured out a way to generate a “genuine” invoice for a product that has not been purchased. All the scammer needs is an email address, because a PayPal account is not needed to receive an invoice. This in turn, tricks PayPal into acting on the scammers’ behalf, sending phishing emails to unsuspecting users.
In the screenshot below, we can see the email appears to be from an official PayPal service account, it has the correct naming convention for the subject, all links within the email point to a genuine PayPal domain, including the “view and pay invoice” button. In conjunction with the message body appearing genuine, it paints a picture of a perfectly legitimate looking email. It’s only when you read the “seller note to customer”, where things start to look suspicious. This is where the classic call back scam exists, it is telling the user there has been a large transaction which will be deducted from their account and to contact a number within 24 hours to dispute this, which of course introduces scarcity into the mix to create a classic scam.
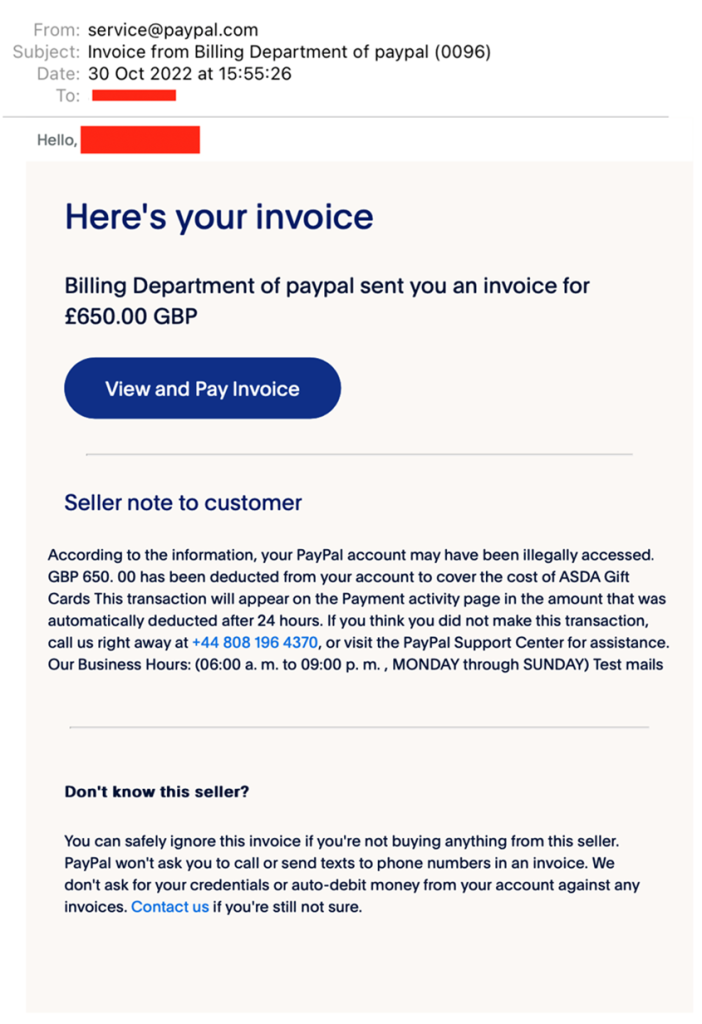
An obvious tell would be the heading stating, “seller note to the customer”, this is not a note from PayPal but from the alleged seller. However, due to the large number in the transaction and the scarcity implied in the message, a victim could be forgiven to glance over this.
A quick and easy implementation of a fix would be a filter on PayPal’s side, much like they have on auction sites, where if any contact details are discovered in the message, for example, an email address or telephone number, it is seen to be attempting to circumvent the communication system in place to protect the customer and the message will not be sent.
Until then, the Cyber Safety and Phishing module from NormCyber can educate users on how to spot a likely phishing/scam email. In this case, the fact it is a sellers note and not a PayPal note and traditional signs of a phishing/scam email.
Sources:
What is PayPal Invoicing and how does it work?
PayPal Phishing Scam Uses Invoices Sent Via PayPal
Hackers Exploit PayPal Invoicing Bug to Launch Advanced Phishing Attacks
Keeping ahead of the Zero-Day vulnerability curve
Recently Microsoft released their Digital Defence Report for 2022. This report, whilst not a wholly representative view of the digital threat landscape, provides invaluable insight from Microsoft’s perspective of general trends and it’s recommended reviewing. One such important finding is that threat actors are responding faster to Zero-Day exploits faster than before.
Microsoft report they “observed a reduction in the time between the announcement of a vulnerability and the commoditization of that vulnerability”, this is likely to only get worse as businesses further integrate and rely on IT systems.
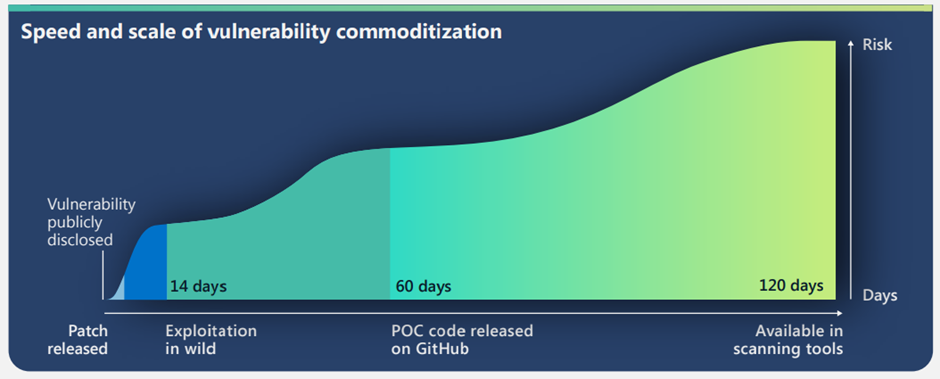
Financial incentives are a strong motivator for threat actors, as shown by the year on year rise in ransomware cases and offerings of commercialised ransomware services. This has pushed threat actors to develop and invest further in vulnerability exploitation and rapid response to be first to market.
The data provided by Microsoft only exemplifies the importance of addressing patchable / mitigatable exploits within organisations. It’s strongly recommended organisations keep and maintain a CMDB along with regularly scan internal systems for vulnerabilities. These data points make identification of potentially vulnerable systems fast and efficient.
NormCyber clients are provided access to smartbloc. LIVE, this platform offers a CMDB utilising the Threat Detection & Response and Vulnerability Management solutions. Using the CMDB within smartbloc. LIVE customers are provided a view of internal devices, their vulnerabilities and respective severity allowing for easy prioritisation. Customers who have taken the Vulnerability Patch Management service can use this to maintain consistent patching of common vulnerabilities / software, allowing for a focus on more urgent patching jobs.
Sources
Microsoft “Digital Defence Report 2022” Executive Report
Microsoft “Digital Defence Report 2022” Full Report
Palo Alto Unit 42 Ransomware Report
The National Cyber Security Centre (NCSC) scans all internet facing servers hosted in the UK
Working on behalf of the British Government and being a part of its Intelligence Agency, the NCSC has launched a new, interesting initiative. They aim to scan all of the nation’s internet-connected servers for possible known vulnerabilities or even zero-day threats as simulated attacks increase in complexity in the future.
It is taking a step forward in a similar fashion to Norway’s National Security Authority and Slovenia’s Cybersecurity Response Unit (SI-CERT) to proactively collect data and create an overview of the UK’s exposure to vulnerabilities following their disclosure as well as track their remediation over time.
This sounds like a noble cause. However, it also raises a few questions around legality, data protection and any potential impact on businesses.
Dr Ian Levy, the Technical Director of NCSC, explains that there are no hidden motives behind the scanning and only minimal amount of information is required to check if the scanned asset is affected by a vulnerability. He promises to be transparent about what NCSC is doing and reasons behind it.
What we know so far:
There is a possibility to opt out of having servers scanned by the government by emailing a list of IP addresses to: scanning@ncsc.gov.uk.
NormCyber provides a dedicated and fully customisable Vulnerability Management service that produces instantly available reports, which can be viewed within the smartbloc. LIVE platform along with recommended remediation.
Further reading:
British govt is scanning all Internet devices hosted in UK (bleepingcomputer.com)
UK government is scanning British internet space for zero-day threats | TechCrunch
The UK government is scanning all of the country’s internet connections | TechRadar
Scanning the internet for fun and profit – NCSC.GOV.UK
11th October 2022 Threat Bulletin