NormCyber threat bulletin: 28th June 2023

“NoAuth” Azure AD vulnerability

In recent years, strong authentication methods have become a crucial cyber security measure for both individuals and organisations. This security implementation allows users and organisations to keep their networks secure by permitting only authenticated users access their protected resources, such as computer systems, networks, databases, and other network-based applications or services.
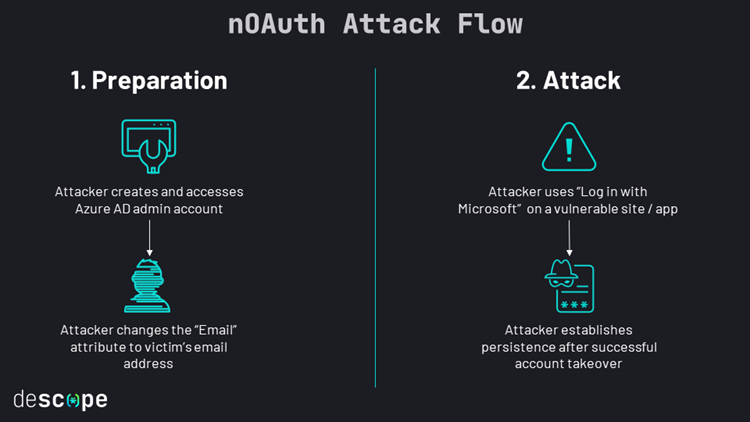
However, security researchers have recently spotted a serious authentication flaw for Azure Active directory (Azure AD), which has the potential for threat actors to cause devastating damage, through escalating privileges which can ultimately lead to full account take over. This authentication flaw (humorously labelled as “nOAuth”) can result in privilege escalation attacks against Azure AD OAuth applications and services that have been configured to use the email claim from access tokens for authorisation.
This misconfiguration can allow threat actors to modify email attributes under the “Contact Information” section in Azure AD and thereby gain access to a user’s account by exploiting the “Login with Microsoft” feature. Attackers can exploit this vulnerability flaw through simply creating and accessing an Azure AD admin account and altering the email address to that of a victim. After which, attackers can utilise the Single Sign-On (SSO) feature on vulnerable applications or services.
If the app merges user accounts without validation, the attacker now has full control over the victim’s account, even if the victim doesn’t have a Microsoft account. Successful exploitation allows the attacker to set up persistence, exfiltrate data, and carry out other post-exploitation activities based on the nature of the app.
Patching information
Microsoft has since published guidance to help developers address the flaw in vulnerable apps. They highly recommend that email claims should not be used for primary user identification purposes or authorisation purposes. Microsoft suggests developers to follow best practices for token validation. Finally, developers should review the app’s source code for incorrect authorisation patterns.
Microsoft has introduced two new claims that can be used to indicate if an email claim is from a domain-verified source and to redact the email claim if necessary. This provides flexibility for developers with specific use cases. In addition, the company Descope have been allocated a bug bounty total of $75,000 for their role in identifying and reporting this vulnerability to Microsoft.
Large-scale phishing campaign impersonates 100’s of brands to harvest user data
Since June 2022, a wide-spread phishing campaign has been in effect, impersonating hundreds of big brand names to harvest account credentials and financial data from unsuspecting users. This campaign has masked itself as many big brands, including Nike, Adidas, Superdry, Casio and many others. According to research performed by Bolster, there are ~3000 domains and 6000 websites included in this campaign (these metrics include inactive sites).
Additionally, research from Bolster states that the campaign had a considerable spike in activity at the beginning of 2023, where almost 300 new phishing sites were being released each month. The research suggests that the campaign has operated over 10 fake websites for brands such as Nike and Puma that feature a design and layout almost identical to the real thing, making it increasingly difficult to identify a fake site upon initial inspection. These websites have been seen to use domain names that incorporate the name of the brand (e.g., Nike) together with a city or country, and then ended with a generic Top-Level Domain such as “.com.” Again, this makes identifying a phishing site such as these difficult at a first glance as the URL looks legitimate and not obviously fake compared to other phishing pages.
Investigations into the domains used on these sites found that a large number were hosted through an organisation known as Alibaba, located in Singapore, most likely utilising their free cloud hosting. The ages of these domains were found to range anywhere from 90 days to 2 years old. Using older domains is an almost essential factor in the success of phishing websites, as websites that remain active and unoffending are less likely to trigger security tools, meaning that they can stay undetected for longer. This is known as domain ageing.
In further research by Bolster, it was found that several domains had survived for such a long time without detection that Google web search had indexed them, which in turn caused them to become high ranking search results. With these domains becoming high ranked search results, they become even more dangerous as many users assume that highly ranked search results are legitimate, so are more likely to interact with them than results further down the search order.
Investigations performed by BleepingComputer found that several of the webpages featured in this phishing campaign were highly realistic imitations of the webpages they are trying to mask as, including a realistic “About us” page, along with contact details and an orders page that works how you’d expect. The exact strategy of this campaign is unknown at this time, but it is suggested that these sites aim to either sell counterfeit goods under the guise of genuine products, or to harvest a user’s banking/card details to be sold later.
The Cyber Safety and Phishing module from NormCyber can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
Sources:
Massive phishing campaign uses 6,000 sites to impersonate 100 brands (bleepingcomputer.com)
Brand Impersonation Campaign Targeting Big Brands (bolster.ai)
Silent danger: One in five aged domains is malicious, risky, or unsafe (bleepingcomputer.com)
Phishing email, the persistent threat
Email plays a crucial role in sharing information and staying connected and cybercriminals have adapted their tactics to exploit unsuspecting individuals and organisations through phishing attacks. Hacking methods through phishing is not new to us and still remains one of the most efficient methods.
Phishing attacks have experienced a significant surge in recent years, causing devastating consequences for victims. Startling statistics reveal that approximately one-third of all data breaches in 2022 involved phishing techniques. More than 70% of phishing emails successfully deceive their recipients, emphasizing the effectiveness of these deceptive tactics. The financial impact of recovering from a phishing attack is estimated at an average cost of $4.9 million, highlighting the severity of the issue. Furthermore, phishing attacks have targeted prominent brands and a concerning 83% of UK businesses fell victim to phishing attacks in 2022.
Amidst the evolving threat landscape, threat actors use evading techniques in order to send further phishing emails from an employee to another compromised employee account which would seem as legitimate. Such known techniques are to change the mailbox rules and move malicious emails to unused folders. Some of these folders are RSS feeds or even just folders created by the attackers. This results in the victim not seeing incoming replies to any malicious emails sent out using the victims account.
Cybercriminals can also create personalised RSS feeds specifically designed to intercept and collect sensitive information from unsuspecting users’ mailboxes. Known as RSS feed injection, this refers to a malicious technique employed by cybercriminals to compromise the integrity of RSS feeds themselves. In this type of attack, the attacker exploits vulnerabilities in the RSS feed system to inject unauthorised or malicious content into the feed, manipulate existing content, or tamper with the feed’s functionality.
The goal of RSS feed injection attacks varies, but they generally aim to deceive or harm users who consume the content through RSS readers or aggregators. By injecting malicious or misleading content into the feed, attackers can spread malware, distribute phishing links, redirect users to malicious websites, or even manipulate the displayed information to mislead or deceive recipients.
As the threat landscape continues to evolve, individuals and organisations must prioritise cybersecurity awareness and implement robust defence measures. Understanding the different forms of phishing attacks and remaining vigilant are crucial steps in mitigating risks. It is essential to invest in comprehensive security protocols, employee training, and incident response plans to combat phishing attacks effectively and protect sensitive data. Additionally, individuals should exercise caution when subscribing to RSS feeds and ensure they are from reputable sources. Regularly updating security systems, staying informed about the latest phishing techniques, and maintaining strong email hygiene practices are essential in safeguarding against phishing exploits and RSS hacking.
Phishing attacks pose a persistent threat to individuals and organisations alike, with devastating consequences for victims.
Key Phishing Statistics for 2023
Sources:
Hide Artifacts: Email Hiding Rules (Mitre.org)
Phishing Statistics & How to Avoid Taking the Bait (DataProt.net)
How to fix a compromised (hacked) Microsoft Office 365 account (Microsoft.com)
Hackers steal $3 million by impersonating crypto news journalists (BleepingComputer.com)