NormCyber threat bulletin: 23rd August 2023

Cybercriminals leveraging Cloudflare R2 cloud storage and Turnstile to avoid detection

Cybercriminals leveraging Cloudflare R2 cloud storage and Turnstile to avoid detection

In the past six months, Cloudflare R2 cloud data storage has seen a sizeable increase of use by threat actors, with an increase of 61 times the amount seen previously. Many of these phishing campaigns aim to target login credentials for Microsoft accounts, along with other applications including Adobe and Dropbox, to name a few.
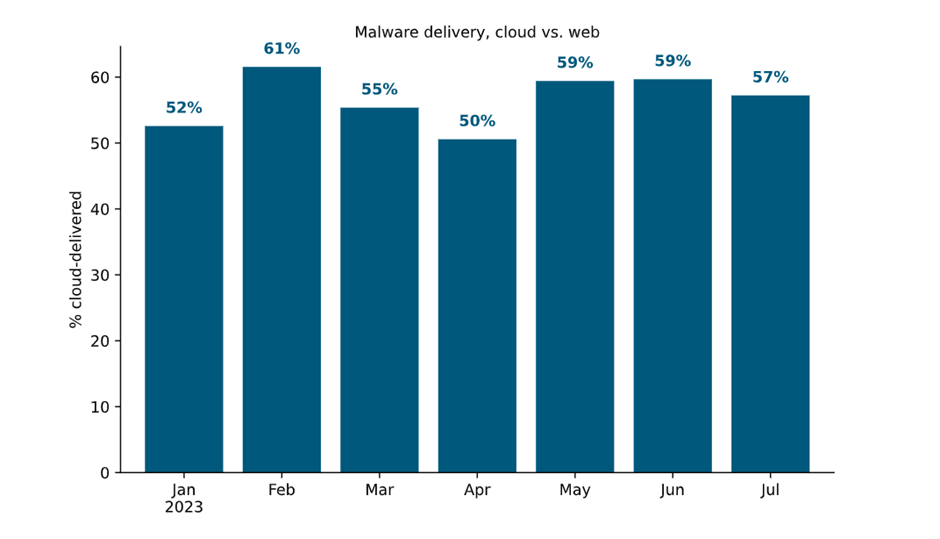
In a blog post published by Netskope, it was seen that 57% of all Malware downloads in July 2023 originated from 167 cloud applications, with Microsoft OneDrive being the number one application in terms of malware downloads. From January to July 2023, at least half of all malware downloads had originated from cloud applications. The research outlined that attackers could see the most success when targeting enterprise users when they abuse cloud applications that the organisation already uses, which is supported by the data that outlines OneDrive as the most popular cloud app for malware downloads, as it is widely used among many different organisations worldwide.
In the same blog post, it was also identified that these phishing pages not only abuse Cloudflare R2, but they also exploit the use of the company’s Turnstile process, which is an alternative to the reCAPTCHA anti-bot security measure. The Turnstile security measure allows a threat actor’s phishing page to remain undetected from bots designed to locate malicious phishing pages. This measure also prevents website scanning tools such as URLScan.io from reaching the site, as it will be unable to make it past the Turnstile security gate.
Additional detection evasion for these phishing sites is implemented by threat actors, which prevents the site from loading specific content until certain conditions are met, which again, helps to prevent detection. For example, if no URL parameter is passed to the referring website, visitors will be redirected to the Google homepage.
The Cyber Safety and Phishing module from NormCyber can educate users on how to spot a likely malicious email. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious emails and links. It is also recommended to take a minute to assess an email or message before responding and never give any remote access to your device.
References:
Cybercriminals Abusing Cloudflare R2 for Hosting Phishing Pages, Experts Warn (thehackernews.com)
Netskope Threat Labs Stats for July 2023 (Netskope.com)
Data leak exposes sensitive information of Police personnel at PSNI
A significant data breach came to light on August 8th, revealing personal information of both police officers and civilian personnel employed by the Police Service of Northern Ireland (PSNI). This incident unfolded because of an unintended data disclosure within a spreadsheet following a Freedom of Information (FoI) request. The breach divulged the surnames, initials, ranks, and work locations of current PSNI employees, including those engaged in sensitive roles like surveillance and intelligence. The data leak raised grave concerns regarding the security of police officers and their families.
The accidental data release took place on the afternoon of August 8th at around 2:30 PM BST. The information, shared in response to an FoI request for officer and staff counts at various ranks and grades, was inadvertently accompanied by a massive 10,799-line Excel spreadsheet containing the confidential details. Subsequently, the spreadsheet was taken down from the FoI website approximately two and a half hours later, following a request from the PSNI.
Assistant Chief Constable Chris Todd, the Senior Information Risk Owner, emphasised that the leaked information only included the mentioned details and no other personal information. He communicated this in a statement released by the PSNI. The incident was reported to the Information Commissioner’s Office as a data breach, and an investigation was initiated to identify potential security vulnerabilities.
In a press conference on the same day, Todd offered apologies for the data leak and acknowledged its severe impact on police officers and their families. He underlined the sensitive context in which the PSNI is currently operating, citing the heightened threat level for Northern Ireland-related terrorism that had been escalated from ‘Substantial’ to ‘Severe’ earlier in the year. This increase was prompted by an uptick in attacks on police officers in the region.
This serves as a reminder of the importance of data protection for organisations and businesses around the world, to help safeguard both their employees and operations. Industry experts reacted strongly to the breach, with legal expert Jonathan Armstrong highlighting the lasting psychological implications for the affected personnel. Brian Honan, CEO at BH Consulting, characterised the breach as one of the most severe he had encountered. He voiced concerns about the potential use of the exposed data by criminal elements or terrorists to target officers or hinder undercover and intelligence operations.
In summary, the accidental data leak of sensitive information from the PSNI represents a critical breach with significant security implications. The incident underscores the necessity of robust data protection measures and the vigilance required to prevent such breaches, especially in contexts involving law enforcement personnel working in high-risk environments.
References:
Northern Ireland Police Officers Vulnerable After Data Leak (infosecurity-magazine.com)
Threat intelligence playing an essential role in cyber world
Threat intelligence serves as a critical arsenal for organisations to comprehend and combat cyber threats. This invaluable information allows them to anticipate, thwart, and identify potential risks that target their assets. In a landscape fraught with uncertainty, where a single cyber threat can cripple an organisation, threat intelligence acts as a beacon of insight.
Modern cyber threats are a complex web of malicious actors leveraging malware to infiltrate targeted systems. They strategically pivot within networks to establish long-term access, enabling them to inflict damage, exfiltrate data, or compromise trade secrets. Organisations have responded by harnessing actionable threat intelligence obtained through advanced malware analysis techniques and sandboxes. This proactive strategy empowers them to bolster their infrastructure defences, elevate incident response capabilities, and tailor security tactics to effectively counter anticipated threats.
Jan Miller, CTO of Threat Analysis at OPSWAT, emphasises the pivotal role of threat intelligence in safeguarding critical assets. He underscores how understanding the ever-evolving threat landscape grants organisations a strategic edge in outsmarting malicious actors, an imperative in the dynamic cybersecurity arena.
Key insights from the research
Threat Intelligence Evolution: Approximately 68% of organisations recognise the urgency of investing more in tools and processes to enhance their threat intelligence capabilities.
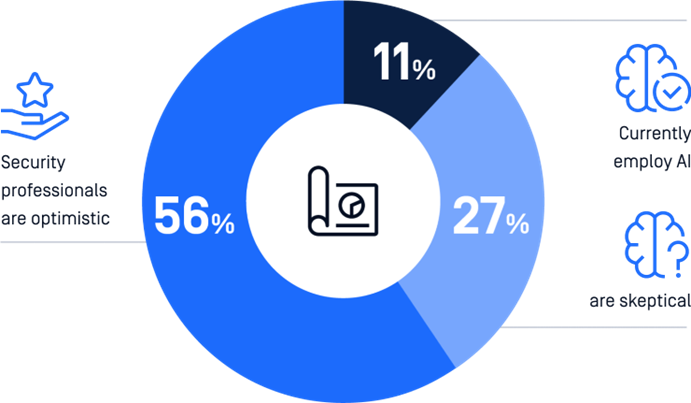
Maturity Levels: Only a mere 22% have fully matured threat intelligence programs. Most organisations are either in their initial stages or require additional investments in tools and processes.
AI Optimism: While currently only 11% of respondents use AI for threat detection, an optimistic 56% of security professionals envision its widespread future adoption, while 27% maintain a more sceptical stance.
Common Challenges: A) As common challenges emerge across organisations, including the identification of both known and unknown malware (68%), the struggle with insufficient signature-based solutions (67%), and managing fragmented tools (54%).
Phishing Concerns: Nearly half of the participants identify phishing URLs and email as top concerns for file types and delivery methods. This underscores the necessity of advanced security measures like Deep Content Disarm and Reconstruction (CDR), sandboxing, and link reputation checks.
Threat Intelligence is proven to be necessary armour in the ongoing battle against cyber threats. Equipping organisations with vital insights, it empowers proactive defence strategies and targeted response. In a digital landscape where uncertainties abound, harnessing Threat Intelligence is not just advantageous. it’s an imperative for safeguarding critical assets and ensuring resilient cybersecurity.
At NormCyber we utilise the latest threat intelligence to both proactively protect our customers against the latest threats and to enrich data we receive to allow us to see the full picture surrounding events.
References:
An introduction to threat intelligence (ncsc.gov.uk)
OPSWAT Publishes 2023 Threat Intelligence Survey Results at Black Hat USA, Reveals Only 22% of Organizations Have a Fully Mature Threat Intelligence Program – OPSWAT
Threat intelligence’s key role in mitigating malware threats – Help Net Security
NormCyber offering network scan for compromised NetScaler devices
In an update to Citrix alerting it’s users of a critical security flaw in NetScaler Application Delivery Controller (ADC) and Gateway, tracked as CVE-2023-3519 and having a CVSS score of 9.8, NormCyber is now able to offer a network scan for compromised NetScaler devices. This is in response to exploitation of the vulnerability being seen in the wild, particularly in the technology, professional services, government, financial services, and defence contractors sectors.
CVE-2023-3519 relates to a case of code injection that could result in unauthenticated remote code execution. It impacts the following versions:
Patches have been made available to address the three flaws in the below versions:
NormCyber’s recommendation is to apply the patch to the NetScaler devices to mitigate the vulnerability, and to also run the compromise scanner given the 0-day exploitation observed in the wild.
If you are a NormCyber smartbloc. customer and would like to utilise this offer, please contact your Focal Analyst who will assist you. If you are not a smartbloc. customer but would like this offer, please contact servicedesk@normcyber.com.
Sources:
CVE-2023-3519 Details (NIST)
Citrix ADC and Citrix Gateway security bulletin for CVE20233519 (Citrix)