NormCyber threat bulletin: 18th October 2023

Two vulnerabilities found within cURL Data Transfer Project (Patched)

Two vulnerabilities found within cURL Data Transfer Project (Patched)

In recent cyber security news articles, it was revealed that two vulnerabilities were discovered within the software known as cURL, which is a data transfer project that aims to transfer data with URL syntax, supporting a wide variety of network protocols including FTP, HTTP, SMTP and SSL, among others. The two main vulnerabilities have been tracked and identified as CVE-2023-38545 and CVE-2023-38546, with the former of the two vulnerabilities labelled as “High Severity”, this vulnerability is described as “the most critical security flaw in cURL recent history” by cURL maintainers.
A brief outline of each vulnerability can be seen below:
CVE-2023-38545 is a flaw within the affected libcurl versions that forces cURL to overflow a heap-based buffer in the SOCKS5 proxy handshake. When cURL is asked to pass along a hostname to the SOCKS5 proxy to allow that to resolve said address instead of cURL doing that itself, the maximum hostname length is 255 bytes. If the hostname is longer than 255 bytes, then cURL switches to local name resolving and only passes the resolved address over to the proxy. However, with the present bug, the local variable saying “let the host resolve the name” could be provided the wrong value in the SOCKS5 handshake and then copy the exceedingly long name to the target buffer. Knowing this, a threat actor could use this bug to perform a denial-of-service attack.
CVE-2023-38546 is the less severe of the two bugs, as the bug is only present when a specific set of conditions are met. Libcurl itself can perform transfers, and in its API, an app creates “easy handles” which are essentially individual handles for single transfers. Libcurl also provides a function which can duplicate these “easy handles.” If a transfer has cookies enabled when duplication occurs, the state of the cookie-enable is also cloned but the cookies themselves aren’t. If the source handle doesn’t read any cookies from the specified file on the disk, then the cloned handle would store the file name as “none” (no quotes). Subsequent use of the cloned handle with no cookies would default to loading cookies from the “none” file, if the file is readable, and more importantly, if the file exists within the current directory of the program using libcurl.
Thankfully, within a few days of announcing the vulnerabilities, cURL have released patches for both of the flaws in their version 8.4.0 update which dropped on the 11th of October 2023. This specific update makes sure that cURL no longer switches to resolve mode if the specified hostname is too long, which therefore mitigates the risk of heap-based buffer overflows. It was noted by Daniel Stenbergy, cURL’s lead developer, that these flaws would not even exist if cURL was written on a memory safe language instead of C, however, the idea of porting cURL to another language has been considered but is not on the agenda.
By utilising NormCyber’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
References:
Patches Prepared for ‘Probably Worst’ cURL Vulnerability (securityweek.com)
Two High-Risk Security Flaws Discovered in Curl Library – New Patches Released (thehackernews.com)
CVE-2023-38545 (curl.se)
CVE-2023-38546 (curl.se)
New Magecart campaign alters 404 error pages to steal shoppers’ credit cards
Online shopping has come a long way since the first e-commerce order in the UK was processed in 1995 by WHSmith. In the two decades that have followed, anything one desires can be purchased online, this gives way to scammers and other threat actors to exploit unsuspecting consumers every step of the way.
Recently uncovered by the Akamai Security Intelligence group is a new Magecart online card skimming campaign, which is targeting an extensive list of websites running Magento and WordPress as their E-commerce back-end. Some victims include large organisations in the food and retail industry.
The complexity of this campaign relies on hiding in plain sight, the attackers rely on injecting malicious code into the HTML pages or within one of the first-party scripts that load when the webpage is accessed.
Akamai security researcher Roman Lvovsky explains in his report that the attack infrastructure is split in three phases to conceal the attack from detection by scanning tools or security researchers.
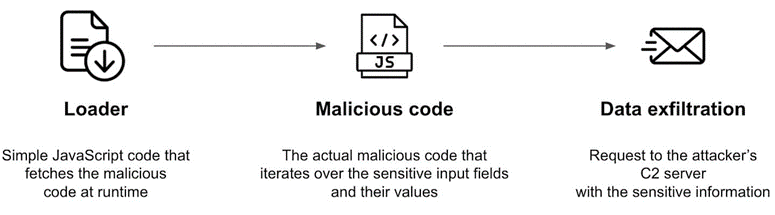
The researcher further explains that once the loader (Stage 1) is injected into the vulnerable webpage and gets executed, it calls out to the relative path “/icons” that does not exist on the victim’s infrastructure. This request, which should lead to a “404 Not Found” error being thrown, does exactly that. To the untrained eye this may lead to thinking that the malicious code is no longer active on the victim’s website, however, the team at Akamai dug a bit deeper and discovered that the attacker had altered the default “404 Not Found” page and concealed the malicious code (Stage 2) within it. Once the skimmer is present on the website, it is presented as an overlay on payment forms within checkout pages, leading to the capture and exfiltration (Stage 3) of card information in the form of a Base64-encoded string.
The use of the 404 error page is merely one of three variations used in this campaign. The other two methods employ the use of malformed HTML image tags on error attribute or adding in the skimmer code as an inline script that is disguised as a social media-esque tracking code snippet. Both of these methods are artfully designed to avert detection; however, the use of the 404 error page stands out for its creativity.
References:
New Magecart Campaign Alters 404 Error Pages to Steal Shoppers’ Credit Cards (thehackernews.com)
The Art of Concealment: A New Magecart Campaign That’s Abusing 404 Pages | Akamai
20 Years of eCommerce: The History in a Timeline | Yoma
Study reveals Conti affiliates’ money laundering practices
Ransomware hacker’s money laundering methods are strikingly basic, enabling the tracking of financial activities. A study during the Conti ransomware group’s 2022 collapse analysed 182 Bitcoin addresses linked to 56 Conti affiliates. These affiliates commonly conducted their transactions in a direct and transparent manner, with minimal obfuscation. Only 8% opted for crypto mixers, increasing the difficulty of tracking. Larger payouts prompted more mixer use (25%), while nearly 40% resorted to dark web services.
The affiliates often chose to conduct a single, direct transaction with most of their illicit proceeds, refraining from breaking it down into multiple transactions over time. This practice, however, is highly insecure, as it lacks any obfuscation layers to conceal the illicit origins of the proceeds.
Merely a small fraction of affiliates, 8%, employed a crypto mixer, a service that combines potentially tainted funds and randomly distributes them to destination wallets, making it exceedingly difficult to trace stolen cryptocurrency.
In the realm of cyber security, large enterprises have traditionally relied on Managed Security Service Providers (MSSPs) to protect their assets and ensure compliance. The shifting landscape, marked by a surge in cyber threats, has led to a trend where small and mid-sized organisations are now turning to MSSPs for governance, risk, and compliance (GRC). This expanding demand poses a range of challenges for MSSPs tasked with managing multiple clients’ platforms and executing compliance monitoring and vulnerability management.
As organisations of all sizes navigate the complex landscape of cyber security and compliance, understanding the dynamics of financial transactions within the realm of ransomware hackers and the role of MSSPs in safeguarding data and mitigating risks becomes crucial.
References:
Study Reveals Conti Affiliates’ Money Laundering Practices (bankinfosecurity.com)
Challenges and Solutions in MSSP-Driven Governance, Risk, and Compliance for Growing Organizations (bankinfosecurity.com)
From payday to payoff: Exploring the money laundering strategies of cybercriminals (link.springer.com)