NormCyber threat bulletin: 09th January 2023

LastPass breach update

Last year NormCyber wrote about the LastPass breaches, however over the Christmas period LastPass provided updated information relating to the breach that occurred in August 2022.
In this, LastPass advised that the threat actor was also able to copy a backup of customer vault data from the encrypted storage container which is stored in a proprietary binary format that contains both unencrypted data, such as website URLs, as well as fully-encrypted sensitive fields such as website usernames and passwords, secure notes, and form-filled data.
The key risks from this are:
The guidance being offered by NormCyber, as well as many others, is if you use LastPass is to assume that all your passwords have been or could be compromised and to change all the passwords stored in your LastPass Vault. Not just the Master password, as just changing the Master password will not have any impact as the threat actor has an offline copy of the vault that is secured only by the password set on or before August 2022.
Sources:
Notice of Recent Security Incident
LostPass: after the LastPass hack, here’s what you need to know
Attackers target Google Ads to serve malicious adverts to distribute malware
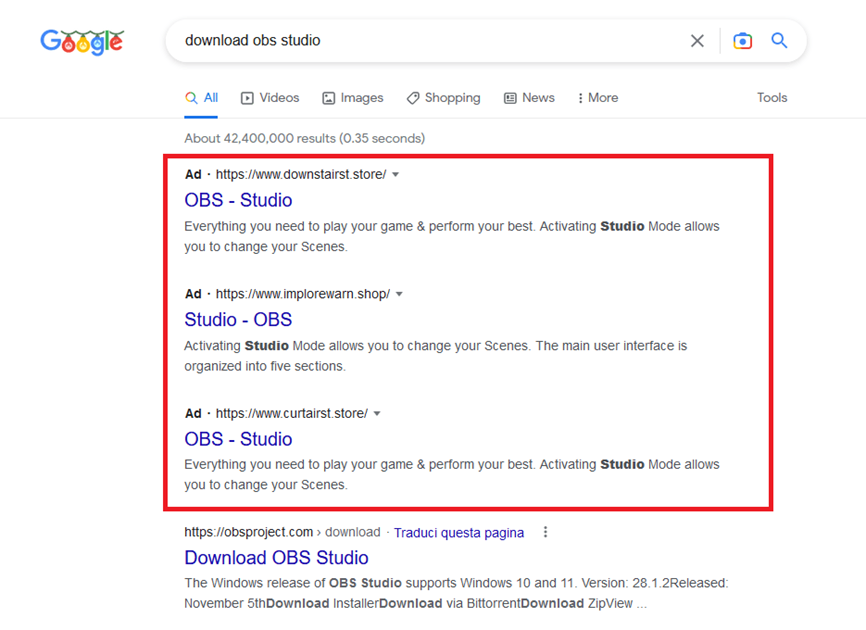
Operators of malware campaigns are making increasing use of ‘malvertising’ – MALicious adVERTISING – to distribute malware via the Google Ads platform. Businesses use Google Ads to promote search results for their services which often rank amongst the first few matching results. Malware operators can exploit this advertisement platform to serve malicious advertisements that direct the user to a benign website controlled by the attacker, which then takes the user to a malicious website impersonating a legitimate service provider. Bleeping Computer reports several popular products have been targeted with malvertising including Grammerly, Slack, Dashlane, and OBS.
OBS, the Open Broadcasting Software for content creators and live streaming, was targeted toward the end of December, whereby a malware operator created a fake website offering a fake OBS application download which contained RedLine Stealer – malware that harvests information from browsers including saved credentials, payment information, browser history, and cookies. The fake website was promoted via Google Ads and appeared above the official search result for OBS.
Online security tools do not always report that the fake sites are malicious and can go undetected for some time.
The fake OBS site provided above is still currently LIVE, serving the described malware. NormCyber advises that you do not make any attempts to visit this site.
It is common for malware to be bundled into legitimate software which appears to be unaltered and can be used as if no modification was made. However, an unusually large file size of an application downloaded from the internet may indicate that the installer may have bundled malware that will execute in the background.
Solutions
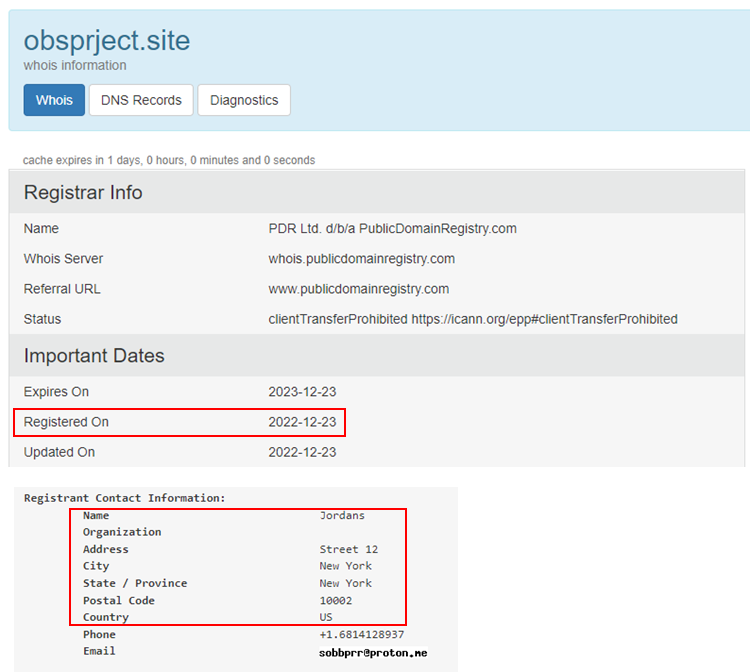
Take precautions when using search engines before clicking any links. Does the domain of the site contain spelling mistakes or missing letters (known as typosquatting), or is the domain name relevant to the product or service you are searching for? The age of a domain and registrar information can also raise suspicion over the legitimacy of the website – has the domain been created recently in the last few days/weeks, and is the registrar’s name correct/relevant? View these details with any WHOIS lookup tool.
Software vendors may provide file hashes of files available for download which can be used to verify the integrity of files downloaded from the internet. You can use PowerShell to calculate the file hash of any given local file to compare with the file hashes provided by the software vendor. Alternatively, you can submit any file downloaded from the internet to VirusTotal or JoeSandbox for further analysis.
Consider the use of an Ad-blocker within your browser of choice. Although Google will attempt to hide search results that are deemed to be malicious, attackers do have techniques to evade detection. An ad-blocker can, in most cases, remove adverts entirely from view.
Sources
Hackers abuse Google Ads to spread malware in legit software
Fake OBS Studio Websites Advertised on Google Lead to Infostealer
Get-FileHash Powershell Reference
Reported phishing attacks have quintupled
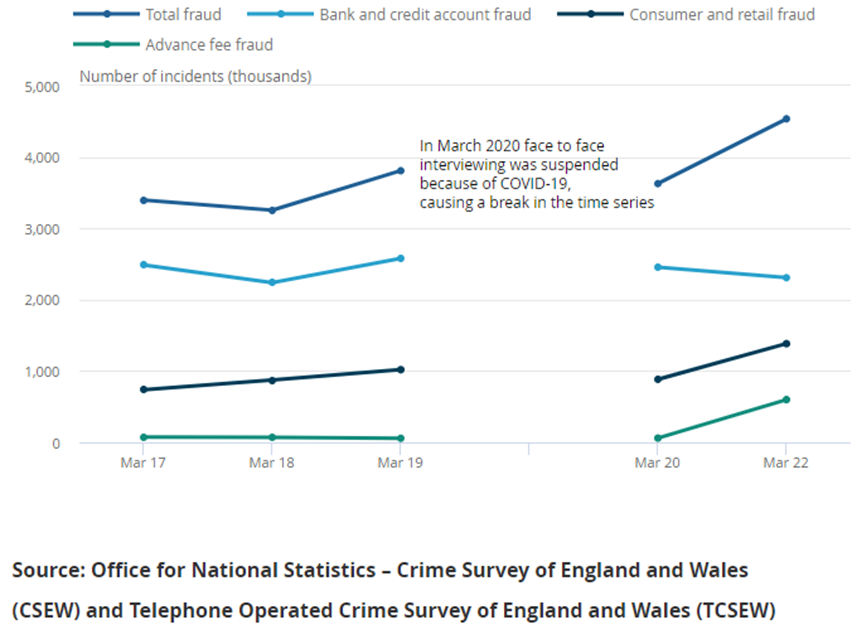
The third quarter of 2022 saw Anti-Phishing Working Group (APWG) observe 1,270,883 total phishing attacks, this is the worst quarter for phishing that APWG has ever observed. The highest monthly total ever reported to APWG was August 2022 with 430,141 phishing sites
Over recent years reported phishing attacks submitted to APWG have more than quintupled since the first quarter of 2020, when they observed 230,554 attacks. It’s not only phishing attacks reported to APWG that have risen, but there is also an obvious rise everywhere you look.
The rise in Q3 2022 was attributable, in part, to increasing numbers of attacks reported against several specific targeted brands. These target companies and their customers suffered from large numbers of attacks from persistent phishers.
Threat researchers noted the following statistics:
Researchers summed up by declaring current security tools and processes like security awareness training can help to identify new attack trends, norm’s cyber security phishing training & awareness package can educate users on how to spot a likely phishing email.
Sources:
APWG | Unifying The Global Response To Cybercrime
Phishing attacks – who is most at risk? – Office for National Statistics (ons.gov.uk)
Over 255m phishing attacks in 2022 so far | Security Magazine
Windows 8.1 end of support reminder
This is a reminder that Windows 8.1 goes out of support from Microsoft on 10th January 2023.
This means that you will no longer receive feature or security updates for this operating system, posing a growing security risk as time goes on.
In conjunction with this, key applications will stop supporting Windows 8.1 in the coming weeks and months, most notably the Office 365 suite and Google Chrome. Office 365 will not receive any 8.1 updates after 10/01/2023, but Chrome has extended support up until the end of the month, with the last supported version being Chrome 109 (currently in Beta).
It is recommended that organisations still running Windows 8.1 strongly consider upgrading or assessing the potential benefits of tactical mitigations (VDI environments, additional network segmentation etc).
Sources:
Microsoft Reference: Windows 8.1 support will end on January 10, 2023 – Microsoft Support
Google Reference: Sunsetting support for Windows 7 / 8/8.1 in early 2023 – Google Chrome Community
Office365 Reference: Windows 8 and Windows 8.1 end of support and Office – Microsoft Support
Further reading:
21st December 2022 Threat Bulletin