
May 2023, Microsoft Patch Tuesday
This month’s patch Tuesday has seen Microsoft address 40 CVEs, among them are 2 critical and 27 high CVSS ratings. Within this release, Microsoft have labelled eight as being likely-to-be-exploited and two with active exploitation detected in the wild. Below, we look at what we believe are the most critical findings from this month’s patch Tuesday release:
Firstly, a Windows Win23K Elevation of Privilege Vulnerability (CVE-2023-29336 7.8). Microsoft states “An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.” The attack has been added to the known exploitation database by the Cyber security & Infrastructure security Agency (CISA), with them making a dedicated statement, “These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risk.” They go as far as strongly urging all organisations to reduce their exposure to cyber attacks by prioritising timely remediation of catalogued vulnerabilities.
Another notable mention is a Windows OLE Remote Code Execution Vulnerability (CVE-2023-29325 8.1). It has a critical rating with the preview pane being confirmed as an attack vector, but it has a high attack complexity. Microsoft states, “This means successful exploitation of this vulnerability requires an attacker to win a race condition and also to take additional actions prior to exploitation to prepare the target environment.” Microsoft continued, “In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted email to the victim. Exploitation of the vulnerability might involve either a victim opening a specially crafted email with an affected version of Microsoft Outlook software, or a victim’s Outlook application displaying a preview of a specially crafted email. This could result in the attacker executing remote code on the victim’s machine.” With the availability of this attack being set as high, this suggests that you should apply updates as soon as possible in the fight against it. Microsoft is recommending that those who have not yet patched to read emails in plain text and to not open RTF files from unknown or untrusted sources to protect against this vulnerability.
The final threat norm. would like to bring to your attention from patch Tuesday is a Secure Boot Security Feature Bypass Vulnerability (CVE-2023-24932 6.2) by using the BlackLotus UEFI bootkit. This comes after the Secure Boot Security Bypass Vulnerability (CVE-2022-21894 4.4) was resolved back in January 2022, meaning this is becoming an actively targeted area by bad actors.
To exploit the vulnerability, an attacker who has physical access or admin rights of a target device could install a malicious boot policy. Once achieved, the attacker successfully bypasses the secure boot mechanism. With successful exploitation of this vulnerability requiring an attacker to compromise admin credentials on the device, there are additional steps required for you to be protected from this vulnerability. Microsoft stated “The security update addresses the vulnerability by updating the Windows Boot Manager, but is not enabled by default. Additional steps are required at this time to mitigate the vulnerability.” You can find the related documentation in the links at the end of this article, where you can use them to determine the impact that these additional measures may have on your environment.
We are expecting further updates for boot policies in July this year, with the enforcement phase coming in the first quarter of 2024. Although Microsoft are actively looking for opportunities to accelerate this timeline.
By utilising norm.’s Vulnerability Patch Management module, customers can ensure they are protected against vulnerabilities disclosed via vendor bug bounty programs.
Sources:
Microsoft’s May Patch Tuesday Fixes 38 Flaws, Including 2 Exploited Zero-Day Bugs
Win32k Elevation of Privilege Vulnerability
Secure Boot Security Feature Bypass Vulnerability
Windows OLE Remote Code Execution Vulnerability
CISA Adds One Known Exploited Vulnerability to Catalog
Phishing websites are now promoted via Google Ads, a new vector for attacks
When searching online using Google, it is almost impossible not to see a sponsored ad in a search result. In today’s cyber security climate, even sponsored Google search results can be malicious, with threat actors uncovering new attack vectors to target users online. These attacks can be especially malicious considering their placement within the search results of a Google web search, with advertisements given priority over the most relevant results to a query.
According to research from Scam Sniffer, the use of Google search advertisements in phishing scams has generated approximately $4 Million for threat actors, while only investing around $15,000 into putting these advertisements out into the world. Due to the level of financial input that attackers would need compared to the ‘reward’ they would obtain, it is no wonder why these forms of phishing attacks have become increasingly popular in recent history.
The primary danger with these Google advertisement phishing scams is that the advert links are always the highest result within a Google search, meaning that they are the first links a user sees when using the search engine. Due to their priority within a given Google search, the likelihood of a user clicking these malicious links drastically increases, as users typically go for the first option believing this to be the most relevant and legitimate option for them.
Google does implement a review process for potential advertisements; however, attackers have discovered a number of techniques that can be used to bypass the review process including debugging prevention and parameter distinction (Figure 1). The use of these techniques is a relatively simple workaround for attackers, however, there have been calls for Google to implement a Web3-focused engine aimed to detect malicious websites, along with monitoring landing pages continuously through the life cycle of advertisement placements.
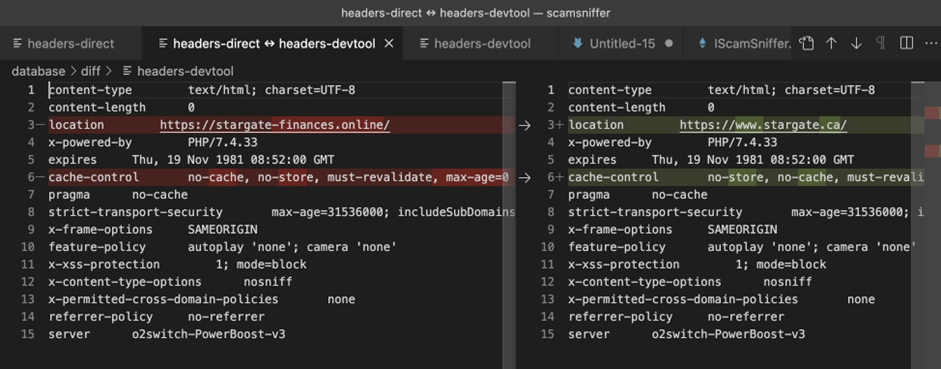
The Cyber Safety and Phishing module from norm. can educate users on how to spot a likely malicious link. With this education, not only would users be more aware of the tactics used by attackers but also the content will enable them to exercise caution when clicking on suspicious links. It is also recommended to take a minute to assess a link before clicking and never give any remote access to your device.
Sources:
Phishing Websites Are Now Promoted via Google Ads; How Can You Protect Your Business?
Phishing scam via Google search ads stole over $4M from users
Scam Sniffer on Twitter – Phishing scams leading to $4 million stolen
The Pyramid of Pain – give hackers a headache
David Bianco developed the Pyramid of Pain to visually demonstrate how indicators of compromise can vary and how some are more valuable than others. This framework also highlights the relationship that different IOCs have on an attacker’s ability to climb up the cyber kill chain and complete their objectives. By denying an attacker’s ability to use different indicators we can bring pain to the attacker via different pyramid tiers, with higher tiers causing the most amount of pain.
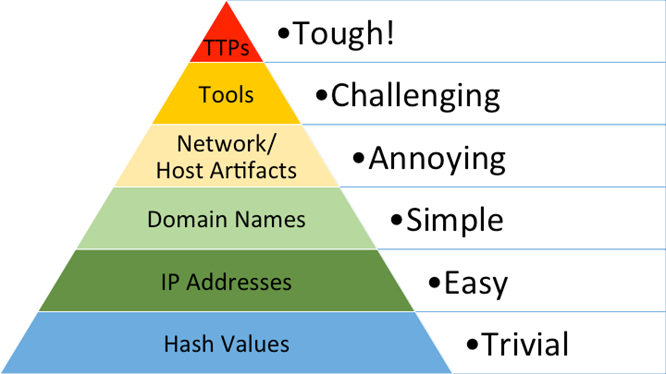
- Hash Values (Trivial)
Hashing algorithms allow us to tell two files apart, even if they are only minutely different. This principle applies for malware too, but any changes made by malware authors will produce entirely new and unique file hashes, meaning that hashes can be difficult for defenders to maintain and track. - IP Addresses (Easy)
Blocking IP addresses that are probing your network will force the attacker to spin up new VM’s with new public IPs, or route traffic for VPN/proxy services. This can bring slight financial pain to the attacker but is still easy for the attacker to complete. - Domain Names (Simple)
Because domain names resolve to IP addresses, it is a little trickier to register or deploy new domains as it can take several hours for public DNS to replicate an attacker’s domain to make it accessible. The financial costs are greater, and domains need to be hosted somewhere. - Host/Network Artefacts (Annoying)
This is the first stage where the inflicted pain becomes substantial, as these indicators are left behind on hosts themselves and in log files.
Host Artefacts (Annoying)
Endpoint Detection and Response (EDR) tooling can use signature and heuristic detections for artefacts such as registry keys, file content, and malicious services among others, forcing attackers to recompile their malware and tools to avoid detection.
Network Artefacts
Network artefacts come in the form of user agents and HTTP headers to name a few. Identifying and blocking traffic to Havoc C2 servers (for example) using the ‘x-havoc: true’ HTTP header could force an attacker to reconfigure their C2 infrastructure. - Tools (Challenging)
By stopping an attacker from using their tools we can severely disrupt their operations. Tools can be bought from hacking/malware marketplaces or can be custom made for a specific target. Either way, if we can detect and respond quickly to an attacker’s tool, we can inflict substantial financial pain to buy new tools or cost the attacker time to develop and research new tools themselves.
Vulnerability management can detect backdoor vulnerabilities on assets, while IDS technology can analyse traffic in real time for indicators of command-and-control traffic. - TTPs (Tough)
Tactics, techniques, and procedures (TTPs) cover the attacker’s actions from reconnaissance to acting on their objectives. Detection and response to how attackers conduct their attacks using established TTPs forces an attacker to improvise, learn new behaviours, or move on to a new target.
MITRE ATT&CK outlines several detections and mitigations for phishing, and by implementing them we can make this technique very hard to accomplish, forcing an attacker to use another technique or give up.
smartbloc. from norm. utilises the pyramid of pain to monitor and respond to attacker activities with Threat Detection & Response, Vulnerability Management, and round-the-clock SOC monitoring services.
Sources:
Enterprise Detection & Response: The Pyramid of Pain (detect-respond.blogspot.com)
The Pyramid of Pain
Royal ransomware
Royal ransomware group, originally known as “Zeon” has impacted several critical infrastructures such as manufacturing and healthcare in 2022. Their attacks are still being seen in 2023 impacting further organisations including education, bringing a total 157.
This threat actor has an active Twitter account called “LockerRoyal” where they announce their compromised victims, tagging them on the Twitter posts. Clearly, they are trying to get public attention.
The initial stage is based on exploring vulnerabilities such as:
- Callback phishing
- SEO poisoning
- Exposed remote desktop protocol (RDP) accounts
- Compromised credentials
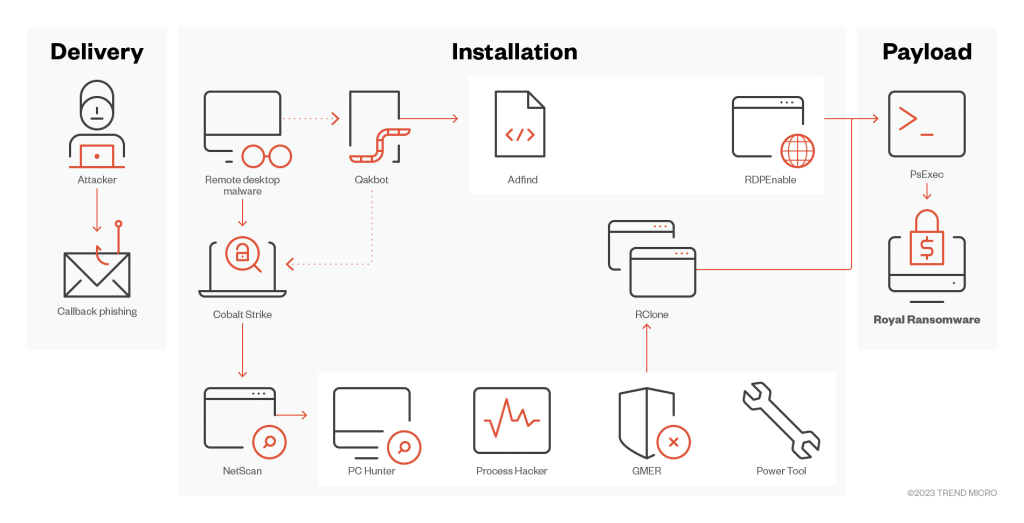
Once connection is established, the group will use tools to support this activity, like the TCP/UDP Chisel, AdFind.
During the infection chain, multiple PowerShell scripts will follow and, in some cases, will activate a BATLOADER.
The BATLOADER is a malware dropper and will download payloads to the victim host, such as VidarStealer, Ursnif/ISFB and redline Stealer. Other tools are also used which are common to system management like NSudo and the Remote Monitoring Management Tool (RMM).
Royal Ransomware utilise a unique encryption method that allows them to choose how much data they encrypt. During this encryption process, the threat actor has a hard-coded RSA public key and uses the AES encrypting method. The encrypted files have the extension “.royal_w”. Beyond the victims host, this ransomware also has functionality to encrypt network shares that are connected to the machine.
Indicators of compromise:
| Argument | Purpose |
| -path | Path to be used for targeting encryption |
| -id | 32-character ID for running sample |
| -ep | Encryption percentage – indicates the percentage of each file to be encrypted |
| -localonly | Encrypt only the local system |
| -networkonly | Encrypt file shares connected to system |
Royal Windows Variant – 595c869f8ec7eaf71fef44bad331d81bb934c886cdff99e1f013eec7acdaf8c9
Royal Linux Variant – b57e5f0c857e807a03770feb4d3aa254d2c4c8c8d9e08687796be30e2093286c
Royal Linux Variant – b64acb7dcc968b9a3a4909e3fddc2e116408c50079bba7678e85fee82995b0f4
Royal Linux Variant – 12a6d61b309171b41347d6795002247c8e2137522a756d35bb8ece5a82fc3774
Recommendations:
Organisations should implement Conditional Access, strong authentication policies and make sure its configuration is up to date, including Sysmon, Windows Command-line and PowerShell logging. Audit user, administrator and service accounts and review PowerShell executions.
norm. offers a Threat Detection & Response module that monitors events on each endpoint to detect malicious activity.
Sources:
StopRansomware: Royal Ransomware
Threat Assessment: Royal Ransomware
Google’s new.zip domain is a security incident waiting to happen
The internet is controlled by a strict set of rules, governed mostly by the Internet Corporation for Assigned Names and Numbers (ICANN). Only the ICANN has authority over top-level domains (TLD), the likes of .com. However, it delegates the responsibility of other TLDs to a number of approved organisations. One such organisation is Google, and Google has just launched the .zip domain.
The implications of having a .zip domain is particularly worrying because it is a commonly used file extension. It is not just the implication of potential victims manually clicking on the link believing it is a file and in fact being forwarded to a phishing link, a significant amount of software automatically converts links that look like URLs into something clickable. A string that ends with .com is almost always going to be a website. However, at the moment, software will not do this just yet with .zip domains since the programs need to be updated, but as they get updates with the most up to date TLD lists, it is likely that .zip will be included. The result being when someone says something like “Please find your latest-payslip.zip attached,” these up-to-date programs will automatically convert this to an actual clickable link. Given that the person receiving the email is expecting to get a zip file, an attacker could upload a zip file to this website, meaning that to the end user, nothing even looks out of place. But in fact, a malicious zip has been downloaded.
An example of the above attack method is already prevalent; Twitter, it is now converting the .zip TLD into a clickable URL, and its going as far as converting all mentions of .zip in old tweets to clickable URLS.
Some may note it is technically not the first time a TLD has shared a name with a file extension, since the .com file extension was used on MS-DOS machines. However, times have very much changed, and we no longer use the .com file extension for executables. This is highly unlikely to change with .zip.
There are already .zip domains being used in phishing campaigns, with attackers utilising names such as officeupdate.zip and Microsoft-office.zip. These hosted a classic credential harvester, where the user was prompted to enter their username and password.
As .zip is a relatively newly released TLD, more information will come to light, with the cost of a .zip domain from Google only costing £13/$15 there is no doubt we will see some very cleverly crafted malicious uses of this TLD.
An example of a specially crafted malicious use would be “latest-payslip.zip” being sent in an email to multiple email addresses of a companies domain. Sending this email at the perfect time; the end of the month, would surely increase the success rate of clicks and result in the attacker gaining access to the victims estate.
Another one of Google’s recently launched new TLD might cause similar issues. The TLD .mov is also available for public registration, and it too is also a file extension, albeit not as popular as .zip.
For now, there is little reason to access .zip domains; this may change if legitimate companies and software developers announce that their products are now also available on a specific .zip domain. norm.’s recommendation is to block all .zip domains at your firewall unless you have a specific need for them, if this is the case, allowing on a per domain basis is likely the best approach currently. Also consider if you have a need to purchase a .zip domain to prevent any impersonation attempts.
Sources:
Hackers are Actively Using the new.zip Domain for Malicious Attacks
New ZIP domains spark debate among cybersecurity experts
Get norm.’s threat bulletin direct to your inbox
norm. tracks and monitors the latest security trends and cyber threats and collates these into a fortnightly threat bulletin.
You can receive this bulletin for free, every fortnight, by entering your business email address below: